---
Introduction
In early 2023, Oracle issued a critical security advisory for a vulnerability in Oracle VM VirtualBox, tracked as CVE-2023-21990. This "Core" component bug could allow a high privileged local attacker—that is, someone who can log into the same computer where VirtualBox runs—to fully compromise the VirtualBox system. Because so many people and companies rely on VirtualBox for safe, isolated virtual environments, this exploit is *a big deal*.
Let's look at what CVE-2023-21990 means, how it could be attacked, who is at risk, and—most importantly—how you can protect yourself.
What Versions Are Affected?
If you are using VirtualBox 6.1 (anything before version 6.1.44) or VirtualBox 7. (anything before version 7..8), you are affected.
- Oracle's official advisory: Oracle Critical Patch Update Advisory - April 2023
About CVE-2023-21990
Type: Easily exploitable local vulnerability
Attack prerequisites: Attacker has a user account (high privilege) on the host
Component: Core (affects core VirtualBox code, not just a plugin or optional driver)
Potential impact: Full takeover of VirtualBox and “scope change”—the attacker may be able to “break out” and impact other products on the host machine.
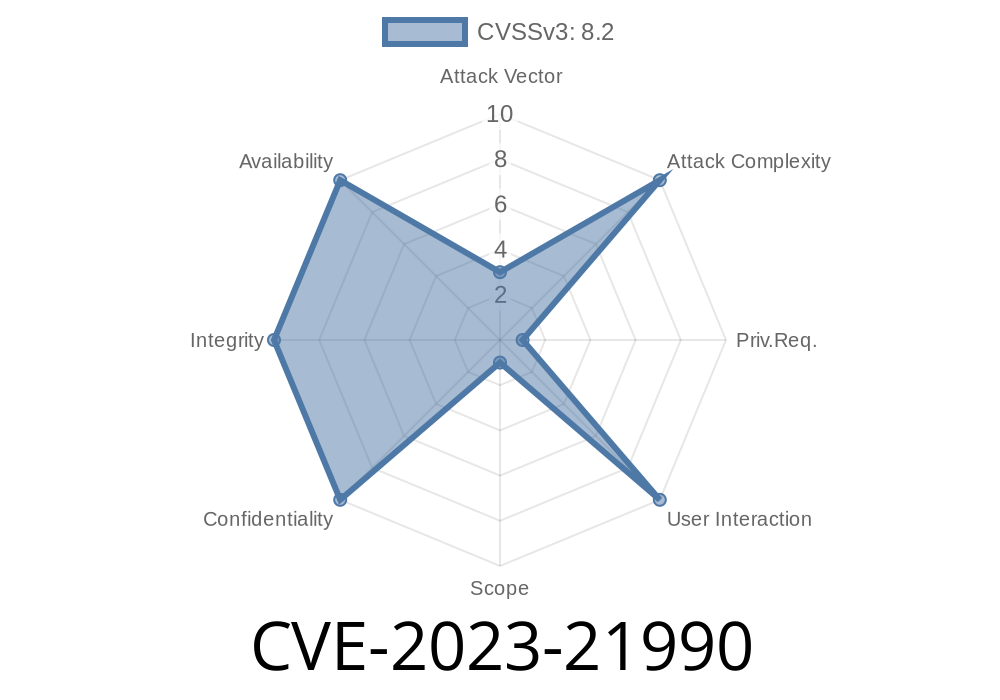
CVSS Base Score: 8.2 High
CVSS Vector: (CVSS:3.1/AV:L/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H)
What does this mean practically? If you have a malicious administrator or a compromised privileged account on your VirtualBox host, that person could run code that entirely takes over VirtualBox, and possibly even uses that access to attack other apps on your computer.
How Does the Exploit Work?
Oracle hasn't published low-level details, but security trackers (NVD) and researcher post-mortems point at a classic privilege escalation and escape-from-VM vulnerability:
A privileged user runs code on the host system (the same computer running VirtualBox).
2. The exploit interacts with the vulnerable VirtualBox Core process, either by sending crafted requests, abusing a flaw in inter-process communication, or exploiting a bug like a heap overflow or type confusion in the core binaries.
3. Successful exploitation allows the attacker's code to execute with the same privileges as VirtualBox, potentially leading to a full takeover.
There is potential for “scope change,” meaning that the attacker could escalate outside the VirtualBox app and impact the broader system.
The key danger: Even though you have to be a privileged user, this scenario is common in shared environments (labs, enterprises, universities) or if a system is compromised by some other means.
Example: Demonstrating a Hypothetical Exploit (Conceptual)
Note: This is a simplified *example* for educational purposes. The real exploit would depend on the exact bug.
Suppose there was a buffer overflow in the Core component of VirtualBox that could be triggered by a malformed API call from a privileged user.
Here is a very simplified C code snippet to demonstrate how such an exploit *might* look
#include <stdio.h>
#include <string.h>
// Hypothetical vulnerable VirtualBox API call
void vboxCoreAPI(char *input) {
char buf[256];
// Vulnerable code: no length check!
strcpy(buf, input);
// ... core functionality
}
int main(int argc, char *argv[]) {
if (argc != 2) {
printf("Usage: %s <attack_payload>\n", argv[]);
return 1;
}
vboxCoreAPI(argv[1]);
return ;
}
An attacker might craft an attack_payload that is longer than 256 characters, which overwrites memory after buf—allowing arbitrary code execution.
Again: The real flaw could be much more complex, but unsafe handling of data in the core component is a common bug class.
Update VirtualBox immediately!
- Get version 6.1.44 or 7..8 (or later) from the Official VirtualBox Download Page.
Follow Oracle’s official guidance and security advice.
- See Oracle CPU Documentation for full details.
More References
- NIST NVD - CVE-2023-21990
- Official VirtualBox Security Notices
Summary
CVE-2023-21990 is a serious vulnerability in VirtualBox’s core that allows a high-privilege local attacker to take over VirtualBox—and possibly impact the rest of the host. If you use VirtualBox versions older than 6.1.44 or 7..8, update *right now* and double-check who has access to your system.
By staying informed, updating your software, and restricting who can get privileged access, you’ll be much safer against bugs like CVE-2023-21990.
If you're running VirtualBox—especially in a shared environment—don't wait. Patch before it’s too late!
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/18/2023 20:37:00 UTC