---
What is CVE-2023-23388?
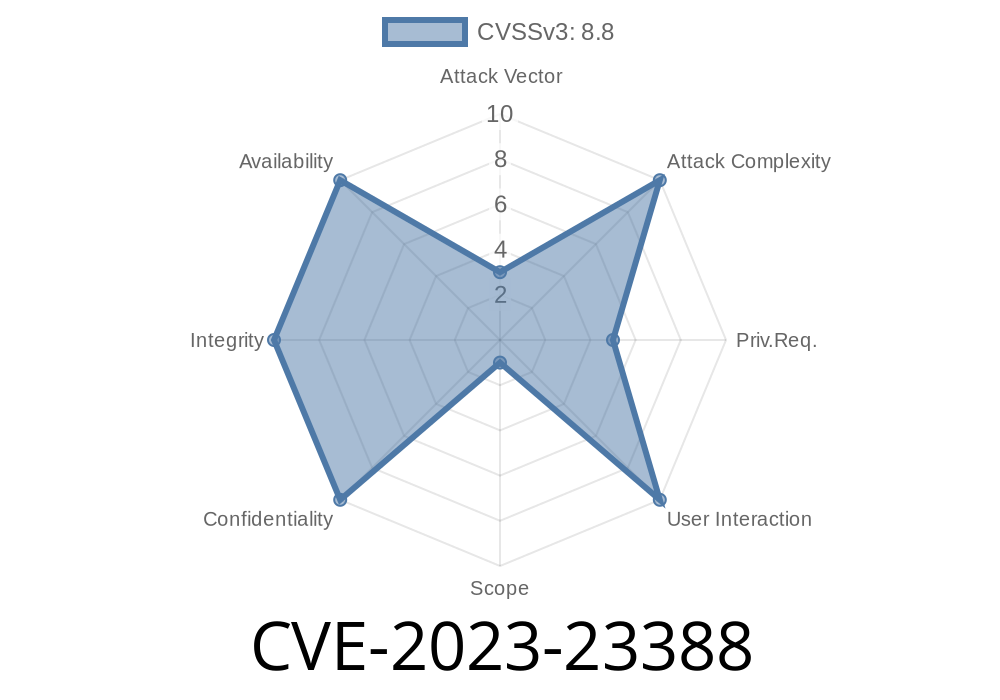
CVE-2023-23388 refers to a security flaw found in the Windows Bluetooth driver (bthport.sys). Microsoft first addressed this vulnerability in its February 2023 Patch Tuesday updates. The issue lets local attackers (people with physical or remote user access) escalate their privileges on the system, potentially gaining full control.
Why Should You Care?
If not patched, this flaw could let a malicious user or malware execute code as SYSTEM—the most powerful account in Windows. That means they could install programs, access sensitive data, or change system settings.
> Simple terms: Someone who already has access (even as a limited user) could use CVE-2023-23388 to become an admin without your permission.
Technical Details
Microsoft described CVE-2023-23388 as an issue with how the Bluetooth driver processes certain requests. Under the hood, it stems from improper handling of objects in memory. This could be exploited by carefully crafted user-mode applications.
Attacker logs in as a regular user (or uses malware running under user rights).
2. They send malicious requests to the Bluetooth driver, taking advantage of its improper object handling.
Proof of Concept (PoC) — What Code Is Involved?
A full working exploit hasn't been widely released (responsible researchers typically avoid this). However, security researchers have published PoC snippets to show the bug's nature.
Here's an *illustrative* example based on available research. Do not use maliciously!
#include <windows.h>
#include <stdio.h>
int main() {
HANDLE hDevice = CreateFile(
L"\\\\.\\BthEnum", // Bluetooth device
GENERIC_READ | GENERIC_WRITE, // Access rights
, NULL, OPEN_EXISTING, , NULL);
if (hDevice == INVALID_HANDLE_VALUE) {
printf("Could not open Bluetooth handle.\n");
return 1;
}
BYTE inputBuffer[1024] = {}; // Should be crafted for real exploit
DWORD bytesReturned = ;
// This IOCTL code would be specific for the vulnerable function
DWORD ioctl_code = x41000C; // Example, not actual value
BOOL success = DeviceIoControl(
hDevice, ioctl_code,
inputBuffer, sizeof(inputBuffer),
NULL, , &bytesReturned, NULL);
if (!success) {
printf("Call failed.\n");
} else {
printf("Call may have succeeded! (Check for privilege escalation)\n");
}
CloseHandle(hDevice);
return ;
}
*Note: Real exploits often use more complex IOCTLs and carefully crafted buffers.*
Exploit Details
Security research groups such as ZDI described the vulnerability in their advisories:
Full technical writeup (with some analysis)
- Zero Day Initiative – CVE-2023-23388
- Microsoft Security Advisory
Update Windows: Patch your systems as soon as possible with the latest security updates.
2. Restrict Local Access: The exploit needs a local user, so limit who can log in physically or via Remote Desktop.
3. Monitor for Suspicious Activity: Look for unusual use of Bluetooth devices or unexplained use of SYSTEM processes.
Final Take
CVE-2023-23388 isn’t just a technical detail—it’s a real risk if you haven’t patched. It reminds us how even built-in peripherals like Bluetooth can become attack points. Keeping your system updated, restricting user access, and staying informed are your best defenses.
More Resources
- Microsoft CVE-2023-23388 update page
- ZDI-23-286 Report
Timeline
Published on: 03/14/2023 17:15:00 UTC
Last modified on: 03/23/2023 16:59:00 UTC