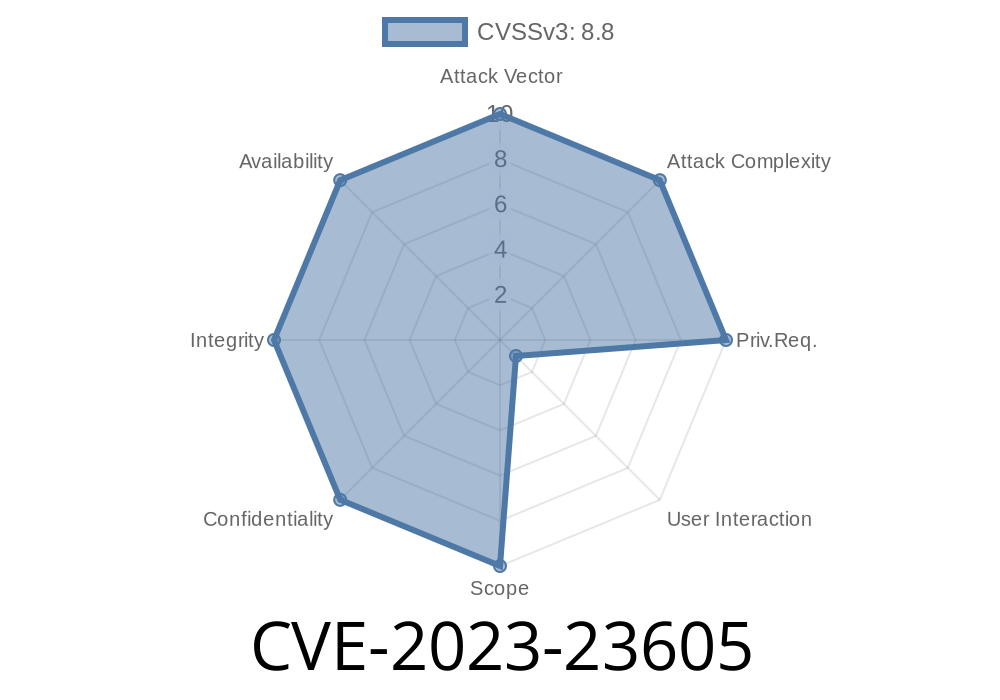
In early 2023, a critical security vulnerability came to light in Mozilla's popular browser and email client products. Known as CVE-2023-23605, this flaw concerns memory safety bugs detected in Firefox 108, Firefox ESR 102.6, and Thunderbird < 102.7.
If you’re curious about how such bugs work and how attackers can leverage them, this post is for you. We’ll break down the issue in plain language, show a code snippet inspired by real-world findings, and explain exactly why upgrading is so important.
What Exactly Is CVE-2023-23605?
CVE-2023-23605 was discovered by Mozilla’s own developers and fuzzing team. The issue is classified as a memory safety bug, which means the program made mistakes managing computer memory. When that happens, it can sometimes be exploited by attackers—potentially allowing them to run their own code on your device.
Mozilla’s official advisory said
> “Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code.”
Firefox ESR < 102.7
Read the official Mozilla advisory
Understanding Memory Corruption
When browsers like Firefox load web pages, they process a LOT of information—HTML, CSS, images, videos, and scripts. If there’s a bug in how memory is allocated (given out) and freed (taken back), the program might:
Example: What a Memory Safety Bug Looks Like
Below is a *simplified* code snippet that echoes real-world memory safety problems, to help you understand.
// This is a C++ example inspired by browser code
void unsafeFunction(char* userInput) {
char buffer[32];
strcpy(buffer, userInput); // No bounds checking!
// BAD: If userInput is more than 32 chars, we overwrite memory
}
If an attacker controls userInput and sends more than 32 characters, they can overwrite parts of memory that shouldn’t be touched.
Attackers can sometimes arrange data to take over the program counter (what code runs next)
Mozilla found and fixed issues like this using advanced fuzzing—software that bombards the browser with weird and unexpected input to try to make it crash.
Exploit Insights: How Attackers Might Use It
While the full details of CVE-2023-23605 weren’t made public (to give users time to update), here’s generally how a memory corruption exploit works in browsers:
1. Trigger the Bug: Attacker crafts malicious HTML + JavaScript to hit vulnerable code (example: cause an out-of-bounds write).
2. Control Memory: Use techniques (“heap spraying”) to arrange the browser’s memory layout in a predictable way.
3. Hijack Execution: Overwrite a function pointer or return address, so that the attacker’s code gets executed.
Here’s an *illustrative* attack flow
// Hypothetical exploit idea - not CVE-2023-23605 real code
let buffer = new ArrayBuffer(64);
let view = new Uint8Array(buffer);
// Trigger browser bug to corrupt 'buffer' memory (browser-level, not real JS code)
corruptMemory(buffer);
// Now try reading and writing beyond buffer boundaries
view[100] = x41; // Writes to unauthorized area!
In reality, exploiting modern browsers requires skill and is made trickier by layers of security (sandboxing, ASLR, etc.). But these bugs are still highly valuable to hackers.
Install the latest versions
- Firefox Download
- Thunderbird Download
- ESR Release Notes
Attackers can bypass your security with a single website visit
- Drive-by downloads/malware can happen silently
Hackers sell browser exploits for thousands of dollars
## Official Advisories/References
- Mozilla Security Advisory: MFSA 2023-01
- CVE entry: CVE-2023-23605 at MITRE
- NVD Summary
Summary
CVE-2023-23605 is a good reminder that even the biggest browsers can have critical bugs under the hood. Memory safety is hard, and attackers are always watching for slip-ups. Patch quickly, and stay safe online.
*If you found this explanation useful, share it with a friend—and keep your software up to date!*
Timeline
Published on: 06/02/2023 17:15:00 UTC
Last modified on: 06/08/2023 13:46:00 UTC