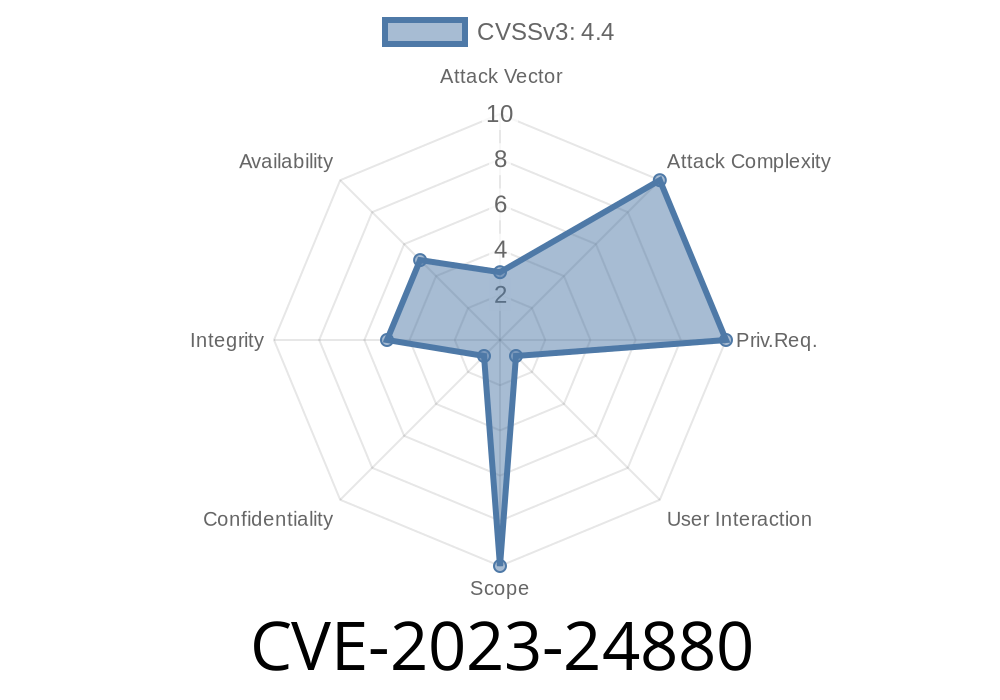
In early 2023, Microsoft revealed CVE-2023-24880, a security vulnerability that made headlines in the Windows world. This flaw allowed attackers to *bypass* Windows Defender SmartScreen—meaning harmful files and links could slip through your computer’s defenses without warning you. In this article, I’ll walk you through what this vulnerability means, how it was exploited, real-life code snippets, and what you (and your company) can do to stay safe.
What is Windows SmartScreen?
Windows SmartScreen is a built-in security feature that helps protect users from malicious software and phishing attacks. When you download an unknown app or click a suspicious link, SmartScreen warns you. It’s especially useful for stopping common threats, like fake installers and credential stealers.
What is CVE-2023-24880?
CVE-2023-24880 is a "Security Feature Bypass" vulnerability found in Windows SmartScreen. Instead of taking advantage of a bug to take over a computer, attackers used this flaw to *trick* SmartScreen into ignoring malicious downloads.
How serious is it?
When a vulnerability lets hackers *disable* a line of defense instead of directly infecting you, it’s pretty serious. Many malware campaigns (especially those using the infamous QakBot and other banking trojans) used this bypass in real attacks.
Official Microsoft advisory:
Microsoft CVE-2023-24880 Page
Mark-of-the-Web
When you download a file from the internet, Windows assigns a special tag called the Mark-of-the-Web (MOTW). This tells SmartScreen the file came from the web, so it should check it carefully and possibly block it.
Attackers found a way to craft a *corrupted* Mark-of-the-Web, fooling Windows into thinking a malicious file was safe. SmartScreen would not show its usual warning dialog—the file would open as if it were local and trusted.
Exploit Details – Code Example
Researchers have shared proof-of-concept (PoC) code showing how attackers abused this bug. Here’s a simplified snippet in Python that (for educational purposes) demonstrates how to make a Mark-of-the-Web that triggers the bypass.
# Example: Crafting a file with a malformed Mark-of-the-Web (MOTW)
# Save this as motw_bypass.py (for learning only! Do not use for malicious purposes.)
file_path = "test_bypass.html"
malicious_code = """<script>alert('Malicious code running!');</script>"""
# Create the malicious file
with open(file_path, "w") as f:
f.write(malicious_code)
# Add a malformed Zone Identifier stream
# (On Windows, data streams are used for file tags. ":" is used for alternate data streams.)
motw = "[ZoneTransfer]\nZoneId=3A" # '3A' is invalid; should be just '3'
with open(file_path + ":Zone.Identifier", "w") as f:
f.write(motw)
print("Created test_bypass.html with malformed MOTW...")
# If you open 'test_bypass.html' now, older/unpatched Windows won't trigger SmartScreen!
Note: Normally, ZoneId should be ZoneId=3 (Internet zone). The attackers used variations like ZoneId=3A or crafted binary junk to cause a parsing error in SmartScreen.
Real-World Attacks
After CVE-2023-24880 was discovered, multiple malware campaigns started using it. According to *Google Threat Analysis Group* (TAG), attackers used this trick to deliver zero-day malware via ZIP archives and MSI installers, bypassing security measures on *fully-patched* Windows machines.
Reference:
Google TAG – CVE-2023-24880 in the wild
> “Threat actors were able to distribute dangerous payloads, such as QakBot and other trojans, without raising any SmartScreen warning. This led to increased infections across enterprise environments.”
Who Is Affected?
Almost all modern versions of Windows (Windows 10, 11) were affected—until the March 2023 Patch Tuesday update was released. If you haven’t updated Windows since then, you’re still vulnerable.
Update your Windows: Microsoft fixed this vulnerability in March 2023.
MSRC Advisory: Update Your Systems!
Final Word
CVE-2023-24880 is a great reminder that no single security feature is perfect. Attackers are always finding creative ways to bypass protection, either by exploiting technical bugs or "tricking" the system with creative tricks like manipulated metadata.
Stay safe: Keep your Windows up to date, never trust unknown files, and stay tuned to advisories from Microsoft and security researchers.
Further Reading & References
- Microsoft official advisory on CVE-2023-24880
- Google TAG blog on SmartScreen bypass attacks
- SecurityWeek: Microsoft March 2023 Patch Tuesday
Disclaimer:
This article is for educational and awareness purposes only. Do not use these techniques for malicious activities. The provided code is a simplified example meant for research and understanding how attackers think. Always follow your local laws and responsible disclosure guidelines.
*Thanks for reading! Stay secure, and keep your system patched.*
Timeline
Published on: 03/14/2023 17:15:00 UTC
Last modified on: 03/21/2023 17:59:00 UTC