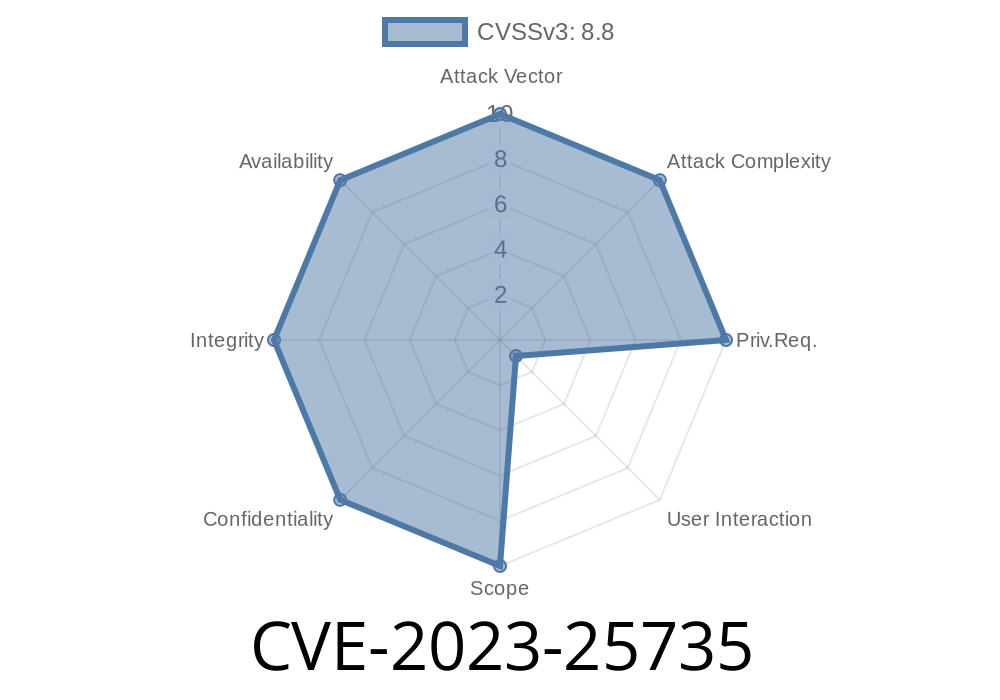
In early 2023, a critical security issue – CVE-2023-25735 – was discovered affecting Mozilla Firefox (versions before 110), Firefox ESR (before 102.8), and Thunderbird (before 102.8). This bug centers around how the browser handles cross-compartment wrappers and scripted proxies, creating a pathway for remote attackers to trigger a serious memory bug called "use-after-free." Let’s break down what this means, how an attack could work, and why you should care.
What’s the Big Deal? Understanding the Bug
Modern browsers like Firefox use a system of “compartments” to isolate different JavaScript execution contexts. These are part of the browser’s defenses — keeping tabs, extensions, and frames apart. But sometimes, objects need to move between these contexts, which is where wrappers come in.
A cross-compartment wrapper is like a box that safely lets code reach into another compartment. Proxies are special JavaScript objects that let you customize fundamental operations. The vulnerability comes into play here:
If a cross-compartment wrapper encapsulates a scripted proxy, it may store references to objects from one compartment (like a web page) inside the main browser compartment. Later, if that proxy is unwrapped (taken out of its protective wrapping) at just the wrong time, you can end up with a “dangling pointer” — a classic setup for a use-after-free bug.
Technical Deep Dive: Code Snippet
You don’t need to be a C++ wizard to see what’s going on, but here’s a simplified illustration in JavaScript. Imagine an attacker has code running in a tab:
// Inside evil example.com frame
const victimObject = { secret: "user credentials" };
// Proxy with custom handler
const evilProxy = new Proxy(victimObject, {
get(target, prop, receiver) {
// some evil manipulation
return target[prop];
}
});
// Simulate sending this proxy into a different compartment (browser wrapper)
window.parent.postMessage(evilProxy, "*");
When the browser tries to unwrap and access this proxy in another compartment, the cross-compartment protections can break down. If the underlying object is deleted (freed) or reused, but a reference is still accessed, that becomes a textbook use-after-free scenario.
With clever timing and manipulation, an attacker can crash the browser — or worse, execute arbitrary code in the context of the main browser process.
Exploit Details
Real-world attacks using this bug were possible but tricky. Attackers needed to lure the victim to a malicious site or get them to open a malicious email in Thunderbird. By crafting JavaScript that manipulates proxies and wrappers, the attacker could trick the browser into accessing freed memory. Since the browser engine’s compartment system is complex, it’s not trivial, but with enough skill, it could be weaponized for:
Arbitrary code execution: Escalate to running code as the user
A proof-of-concept for a use-after-free in the SpiderMonkey engine (Firefox’s JavaScript engine) would look something like this:
let proxy;
let compartmentLeak;
function raceCondition() {
// Setup cross-compartment messaging
window.onmessage = function(event) {
proxy = event.data;
// Simulate freeing the object unexpectedly (in real exploit, via GC or similar)
compartmentLeak = null;
// Forced access after free
try {
proxy.secret;
} catch (e) {
// Crash or code execution could be triggered here
}
}
}
// Simulated main thread setup
compartmentLeak = { secret: "Sensitive Info" };
const fakeProxy = new Proxy(compartmentLeak, {});
window.postMessage(fakeProxy, "*");
In actual attacks, the timing is much more tricky, often relying on garbage collection and complicated manipulation of browser internals.
Firefox ESR < 102.8
If you have these versions installed in your system — especially if you use extensions or browse sketchy sites — you’re at risk.
How Was This Fixed?
Mozilla’s patch ensured that cross-compartment wrappers do not let objects from other compartments leak into the main context. The crucial fix was to check and restrict how proxies and their targets are accessed and unwrapped, blocking attackers from being able to trigger the bug.
- Firefox 110 Release Notes
- GitHub Security Advisory
- Mozilla Security Bug 1815135 *(login required for some details)*
Update your browser and email client! If you’re on an affected version
- Go to Help → About Firefox/Thunderbird and check for updates.
Final Thoughts
CVE-2023-25735 is a serious reminder of how complex browser security really is. One small mistake in the way compartments share objects can give attackers a reliable pathway to compromise your system. The Mozilla team fixed it quickly, but it’s a wakeup call for all browser users to stay up to date.
Stay safe, keep your software patched, and remember: even the safest browsers rely on you to stay up to date!
Further Reading
- Official Mozilla Add-Ons Security Blog
- CVE-2023-25735 at MITRE
- Mozilla Foundation Security Advisory 2023-07
Thanks for reading! If you have any questions about browser security, feel free to leave a comment below.
Timeline
Published on: 06/02/2023 17:15:00 UTC
Last modified on: 06/08/2023 16:05:00 UTC