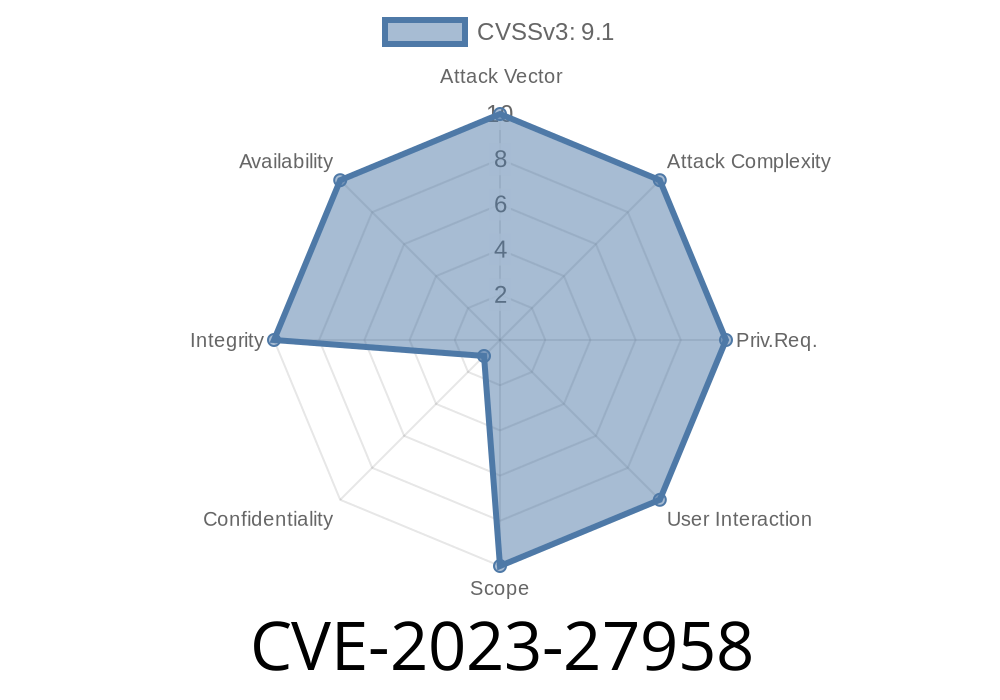
CVE-2023-27958 is a significant security vulnerability found in Apple’s macOS kernel. This bug could let a remote user—without even having direct access to your computer—cause your system to crash or corrupt its memory. That’s a big deal, especially if you rely on your Mac for important tasks. Thankfully, Apple patched the issue in new updates, but let’s dive deep into this CVE, how it works, and why it matters—for both regular users and anyone curious about system security.
What is CVE-2023-27958?
CVE-2023-27958 is a vulnerability in the XNU kernel, the core of macOS. Poor memory handling means specially crafted network data might trick your system into mishandling memory. This can crash the computer (think: “kernel panic”) or allow nasty stuff like kernel memory corruption, which is a stepping stone to even more serious attacks.
To sum it up: A bad actor on your network could remotely cause your macOS device to freeze or run malicious code.
Technical Dive: How the Exploit Works
While Apple did not publish every technical detail (for obvious reasons), the core problem lies in the kernel’s memory handling of certain network requests. Here’s the basic idea simplified:
Remote Input: Your Mac receives network data (could be over Wi-Fi, LAN, or even Bluetooth).
2. Bad Handling: Because of this bug, macOS’s kernel fails to check the size or content of what it’s handed.
Memory Corruption: The malformed data overflows, corrupts, or improperly maps critical memory.
4. Crash or Control: Either the system crashes to protect itself, or in the worst case, an attacker gains control.
Pseudocode Example (Simplified & Hypothetical)
// Simplified: Handling incoming network buffer
void vulnerable_function(char *data, size_t len) {
char kernel_buffer[256];
// BAD: No bounds check!
memcpy(kernel_buffer, data, len);
// ... further processing
}
// An attacker could send "len" > 256 and crash the system!
Note: In real kernel code, it’s way more complex, but the error comes down to missing checks and unsafe memory copy.
Exploit Details
Real-world exploits were not publicly released, thanks to responsible disclosure and Apple’s fast patch. But a skilled remote attacker could craft network packets targeting your Mac to trigger this bug.
*Sample Exploitation Approach (Conceptual):*
1. The attacker identifies a service exposed to the network (e.g., AirDrop, network printing, file sharing).
If you look at the release notes, for example
- Apple Security Updates – macOS Big Sur 11.7.5
- macOS Monterey 12.6.4 Update Info
- macOS Ventura 13.3 Update Info
- Apple Security Release Notes (CVE Entry)
You’ll notice language like
> “The issue was addressed with improved memory handling. This issue is fixed in macOS Big Sur 11.7.5, macOS Monterey 12.6.4, macOS Ventura 13.3.”
What Should You Do?
Update your Mac!
If you’re running anything older than Big Sur 11.7.5, Monterey 12.6.4, or Ventura 13.3, you are at risk—even if you don’t use the internet much.
You can update by going to:
Conclusion
Vulnerabilities like CVE-2023-27958 show how even tiny bugs in the kernel can have massive impact. Apple moved quickly to patch it, but it’s up to users to keep systems updated.
Remember:
Take network security seriously, even at home
Original References:
- Apple Security Updates List
- CVE-2023-27958 Entry (MITRE)
Timeline
Published on: 05/08/2023 20:15:00 UTC
Last modified on: 05/19/2023 16:15:00 UTC