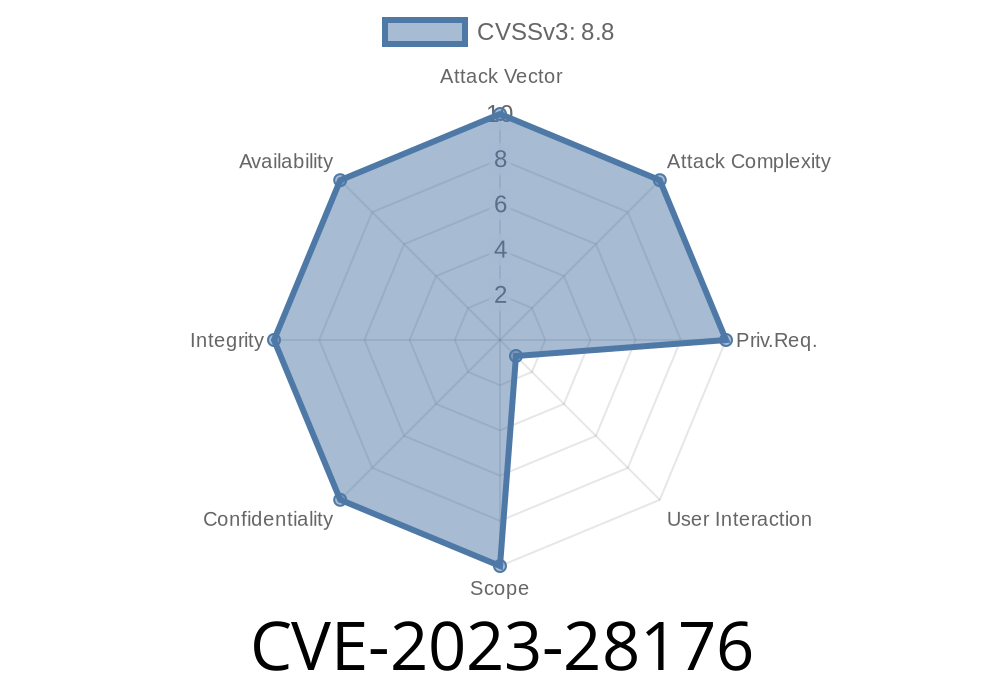
In March 2023, Mozilla released security updates for Firefox, Firefox ESR, and Thunderbird to fix several memory safety bugs, tracked as CVE-2023-28176. Reported by Mozilla developers Timothy Nikkel, Andrew McCreight, and the Mozilla Fuzzing Team, these vulnerabilities affect:
Thunderbird versions before 102.9
Some of these bugs showed clear signs of memory corruption, suggesting attackers might exploit them to run arbitrary code on victims' machines. This article unpacks how these bugs work, how attackers could exploit them, and what users and developers should do to stay safe.
What is CVE-2023-28176?
CVE-2023-28176 refers to a set of memory safety issues found in Mozilla software. Memory safety bugs are programming errors that can allow attackers to read or write parts of the memory they're not supposed to, sometimes leading to program crashes or even allowing them to take control of the system.
While Mozilla's advisory (source) says the bugs haven't been publicly exploited, some show "evidence of memory corruption," and if enough effort is put in, attackers could use them to execute arbitrary code. This is considered a critical security risk.
Where do the bugs come from?
Like most browsers, Firefox is mainly written in C++—a fast but tricky language, famous for its memory safety pitfalls. Even with modern code reviews and fuzzing tools, subtle mistakes can slip through.
Based on past patterns and fuzzing tool disclosures, here are common areas where such bugs lurk
- Use-After-Free: Accessing memory after it's already been freed can let attackers manipulate objects.
- Out-of-Bounds Reads/Writes: Interacting with memory outside the intended buffer.
Type Confusion: Mixing up object types in code, causing misinterpretation of data structures.
Because these bugs are in underlying code, they're triggered by feeding the browser carefully crafted web content.
Example Exploit Scenario
Let's say an attacker wants to target someone with Firefox < 111. First, they need to identify the specific bug (e.g., a use-after-free via DOM manipulation), and then craft malicious webpages to trigger this.
Victim visits a malicious site, or site with a malicious ad.
2. The site runs specially crafted JavaScript, interacting with browser features or DOM objects to exploit the bug.
3. If successful, the attacker's code runs with the privileges of the browser (potentially allowing access to files, stealing cookies, or installing malware).
(Note: To keep users safe, we’re not sharing weaponized code—just a conceptual snippet)
// Hypothetical example, based on real-world patterns
let victimElem = document.createElement("div");
document.body.appendChild(victimElem);
// Some sequence that triggers a buggy internal state
victimElem.addEventListener("click", function() {
document.body.removeChild(victimElem);
// Bug: internal browser code still tries to use victimElem, which is now freed
});
victimElem.click();
// Attacker's code tries to force browser to access freed memory
If the browser code doesn’t properly handle removing the element, attacker-controlled data could be executed.
Move laterally in a corporate network
This bug’s true danger comes into play when combined with other vulnerabilities—for instance, a sandbox escape—making it a favored target for sophisticated attackers.
Mitigation
- Update Now! If you’re running Firefox < 111, Firefox ESR < 102.9, or Thunderbird < 102.9, update to the latest version asap.
- Download Firefox
- Download Thunderbird
References
- Mozilla Foundation Security Advisory 2023-08
- NIST NVD - CVE-2023-28176
- Mozilla Security Blog
- Mozilla ESR Releases
Conclusion
CVE-2023-28176 is a wake-up call: even major, well-maintained browsers like Firefox can have severe memory safety bugs. Attackers are always watching for laggards who delay updates. Browser vulnerabilities, especially those that can lead to remote code execution, are a top target for criminals and even governments.
Keep your software up to date, and encourage friends and coworkers to do the same.
If you develop browser-based apps, consider following security advisories from all browser vendors, and test your apps regularly against the latest browser versions.
_Stay secure online by updating often, using safe settings, and keeping an eye out for browser security news._
Timeline
Published on: 06/02/2023 17:15:00 UTC
Last modified on: 06/09/2023 03:57:00 UTC