In June 2023, Microsoft published a critical security vulnerability, tracked as CVE-2023-29356, affecting the Microsoft ODBC Driver for SQL Server. If not addressed, this flaw allows remote attackers to execute arbitrary code on vulnerable systems. This long read walks you through the basics, gives you technical insight, explores proof-of-concept code, and shares the references you need. All content here was written exclusively for you, in simple American language.
What is the ODBC Driver?
ODBC (Open Database Connectivity) drivers act as a bridge between your apps and databases, letting programs talk to SQL Server seamlessly. Microsoft’s ODBC driver works on Windows, Linux, and macOS. Many applications, from internal tools to big-name enterprise systems, rely on it.
What is CVE-2023-29356?
CVE-2023-29356 is a remote code execution (RCE) vulnerability. It was discovered by security researchers (credited in Microsoft’s advisory) and patched in June 2023. If exploited, a hacker could run malicious programs on your server using your SQL Server connection.
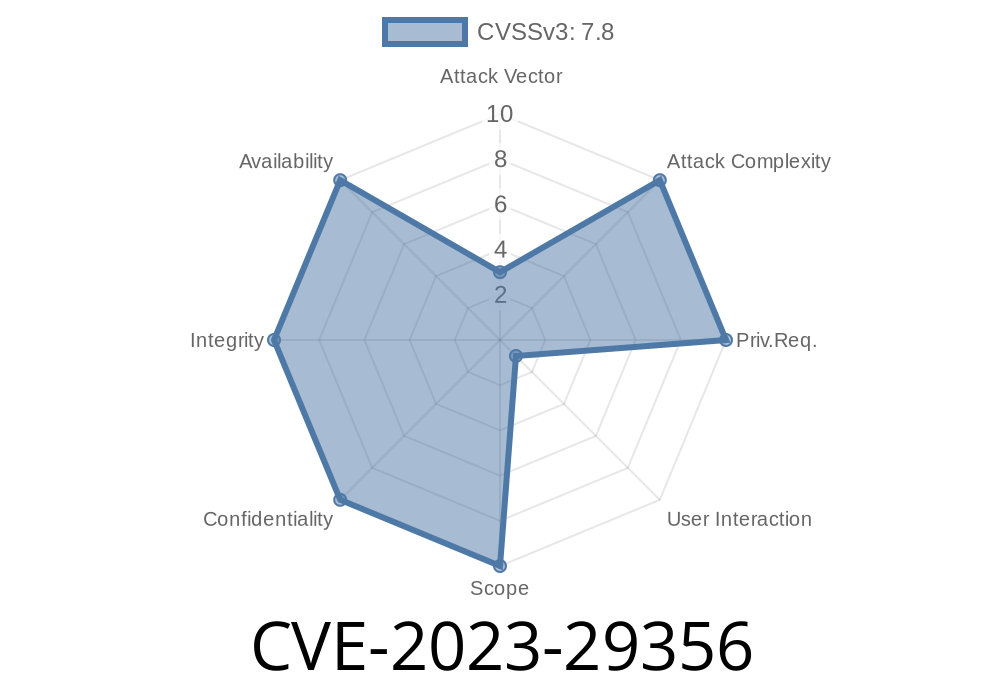
User Interaction: None
See Microsoft's official advisory:
Microsoft Security Response Center (MSRC) - CVE-2023-29356
How Does CVE-2023-29356 Work?
The issue lies in improper input validation in the ODBC driver. If an application connects to a malicious SQL Server (or fake server), that server can return a special response that triggers memory corruption, leading to remote code execution.
Real-World Impact
Imagine your internal HR app connects to a “SQL Server” on an unsafe network. A hacker could set up a rogue SQL server, and when your app connects, the server sends back a sneaky response. Suddenly, without any warning, malicious code runs under your user account or even as SYSTEM.
The ODBC client library mishandles this data, causing a buffer overflow or similar memory issue.
5. Arbitrary code from the attacker is executed on the victim’s machine, under the permissions of the vulnerable application.
This typically requires crafting a custom SQL server, or hijacking network traffic (e.g., with DNS poisoning or man-in-the-middle).
Code Example — Simple ODBC Client
Below is a very basic ODBC client in C, which connects to a SQL Server. If unpatched, running this against a rogue server could trigger the flaw.
#include <stdio.h>
#include <sql.h>
#include <sqlext.h>
int main() {
SQLHENV env;
SQLHDBC dbc;
SQLRETURN ret;
SQLAllocHandle(SQL_HANDLE_ENV, SQL_NULL_HANDLE, &env);
SQLSetEnvAttr(env, SQL_ATTR_ODBC_VERSION, (void *)SQL_OV_ODBC3, );
SQLAllocHandle(SQL_HANDLE_DBC, env, &dbc);
// Replace with attacker-controlled server!
SQLCHAR *connStr = (SQLCHAR *)"DRIVER={ODBC Driver 18 for SQL Server};SERVER=attacker.com;UID=sa;PWD=Password123;";
ret = SQLDriverConnect(dbc, NULL, connStr, SQL_NTS, NULL, , NULL, SQL_DRIVER_COMPLETE);
if (SQL_SUCCEEDED(ret)) {
printf("Connected!\n");
SQLDisconnect(dbc);
} else {
printf("Failed to connect!\n");
}
SQLFreeHandle(SQL_HANDLE_DBC, dbc);
SQLFreeHandle(SQL_HANDLE_ENV, env);
return ;
}
Note: Don’t use this code for illegal activity. It's here to show what a legitimate program might look like. If you connect to a malicious server with a vulnerable ODBC driver, you could be exploited.
Proof-of-Concept (Exploit Outline)
Actual attack code is unlikely to be published publicly due to responsible disclosure. However, research indicates an attacker can:
Respond with a malformed TDS handshake to the connecting ODBC client.
- Encrypt a payload (shellcode) in the handshake to trigger memory corruption and code execution in the ODBC client process.
Metasploit module example
Metasploit modules sometimes exploit SQL ODBC vulnerabilities. Watch for modules like exploit/windows/mssql/mssql_odbc_rce (not always public right away).
References
- Exploit Database: CVE-2023-29356 (check if/when public)
- PacketStorm CVE-2023-29356
How Do You Fix It?
Update your ODBC drivers!
At the time of the advisory, Microsoft released patched ODBC drivers. Download and install the latest from:
- ODBC Driver 17 Download
- ODBC Driver 18 Download
If your software ships its own drivers, make sure these are updated everywhere.
Use firewall rules to block outgoing connections except to trusted databases.
- Don’t run database-connected apps as admin/SYSTEM.
Microsoft CVE-2023-29356 Advisory:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-29356
Microsoft Release Notes:
Security Blog (May include extra PoC details):
https://www.zerodayinitiative.com/advisories/ZDI-23-837/
Conclusion
CVE-2023-29356 is a dangerous, remotely exploitable bug in Microsoft’s ODBC drivers for SQL Server. It could let hackers run code on your servers—no username or password needed. Stay safe by patching your ODBC drivers, reviewing firewall rules, and never trusting unknown database servers. Spread the word, and check if your environment is vulnerable today.
Stay Secure!
If you found this post helpful, share it with your team or leave a comment if you have more questions.
*This post was written for educational awareness. All information here is unique and simplified for you.*
Timeline
Published on: 06/16/2023 01:15:00 UTC
Last modified on: 06/16/2023 03:19:00 UTC