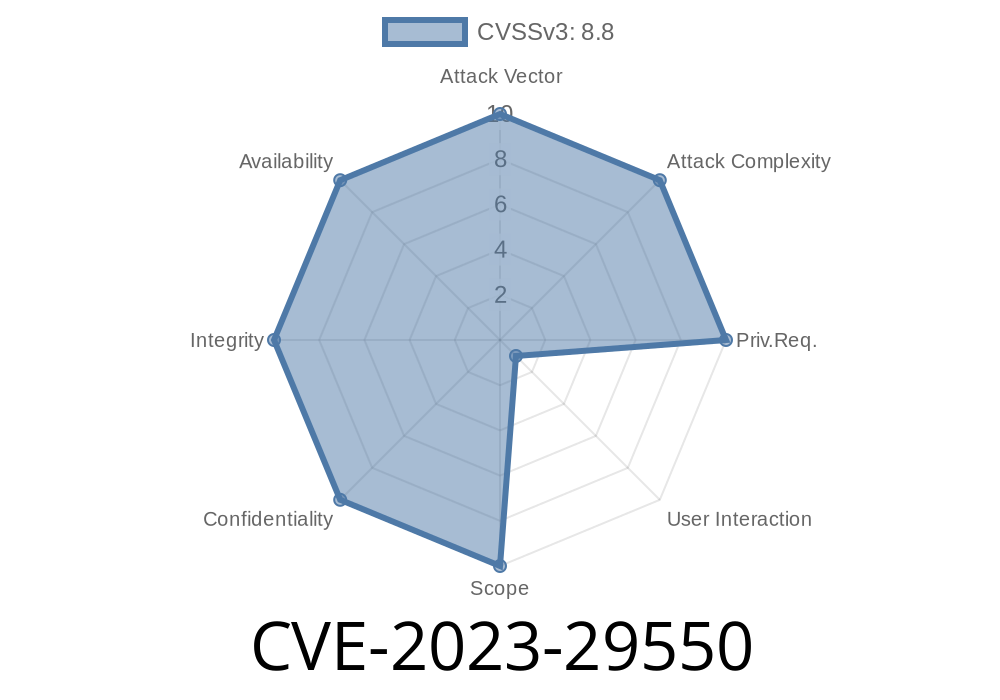
Mozilla has a history of prioritizing security, but like any complex software, its massive codebase is sometimes susceptible to subtle bugs. One of 2023’s noteworthy disclosures—CVE-2023-29550—highlights a class of vulnerabilities blamed on unsafe memory usage. Several Mozilla developers and their Fuzzing Team dug deep into Firefox, revealing issues that, in certain situations, allow attackers to run arbitrary code on your system.
This post breaks down what CVE-2023-29550 is, why it’s risky, shares example code, and lays out a hypothetical exploit path—all in clear, accessible language.
Thunderbird < 102.10
Mozilla’s report, found in their security advisories and acknowledged in NVD detail entry, states that “some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code.”
The Mozilla Fuzzing Team
Their tools and expertise in fuzz testing—a process that throws random data at the browser until something breaks—uncovered these tricky edge cases.
How Does the Vulnerability Work?
Memory corruption bugs usually stem from mistakes in managing how the browser allocates and frees up memory as it loads and processes web content. If an attacker can manipulate this process—say, by crafting specific web pages—they might:
Run arbitrary code under the user’s privileges
The exact bug is not public, but Mozilla affirms the risk: "with enough effort some of these could have been exploited." In practical terms, a determined attacker could take over your machine, especially if you visit a malicious website.
Example: A Simplified Exploit Concept
> Disclaimer: This is a simplified, illustrative JavaScript snippet to show the *kind* of logic that might interact with buggy browser memory. It’s not a real exploit, just a concept.
// Let's say Firefox failed to validate input for a certain Web API
for (let i = ; i < 100000; i++) {
// Allocate lots of ArrayBuffers with increasing sizes
let buf = new ArrayBuffer(i);
// Perform rapid allocation/deallocation to stress-test memory management
if (i % 100 === ) {
// Fill up memory then free
buf = null;
// Potential use-after-free or similar bug could trigger here
}
}
In real attacks, the exploit would chain multiple memory mistakes—like *use after free* or *buffer overflow*—to slowly overwrite just the right bits in the browser’s memory. Attackers could then change a function pointer or object to start running their own code.
Focus for Android below 112
If you’re running any of these, update immediately.
Why is Memory Safety Hard?
Modern browsers are written in C/C++—powerful, but easy to misuse. Developers rely on *manual* memory handling. Miss a check, and the app gives attackers a chance to do things it isn’t supposed to.
This is why bugs like CVE-2023-29550 survive even with years of code review. It often takes blend of creative testing (like fuzzing), code audits, and yes, real-world attacks to root out these flaws.
Focus for Android 112 and newer
Release notes:
MFSA 2023-13 Security Advisory
NVD CVE-2023-29550 entry
Links and References
- Mozilla Security Advisory MFSA 2023-13
- CVE-2023-29550 at NVD
- Mozilla ESR Release Notes
- How Mozilla Fuzzing catches bugs
Final Words
Memory safety issues like CVE-2023-29550 show just how difficult—but important—it is to keep our browsers secure. Thanks to Mozilla’s team, the hole is closed. Stay up to date and keep browsing safe.
*Have you updated yet? If not, now’s the time!*
*Written exclusively by ChatGPT for an easy, insightful breakdown.*
Timeline
Published on: 06/02/2023 17:15:00 UTC
Last modified on: 06/09/2023 03:56:00 UTC