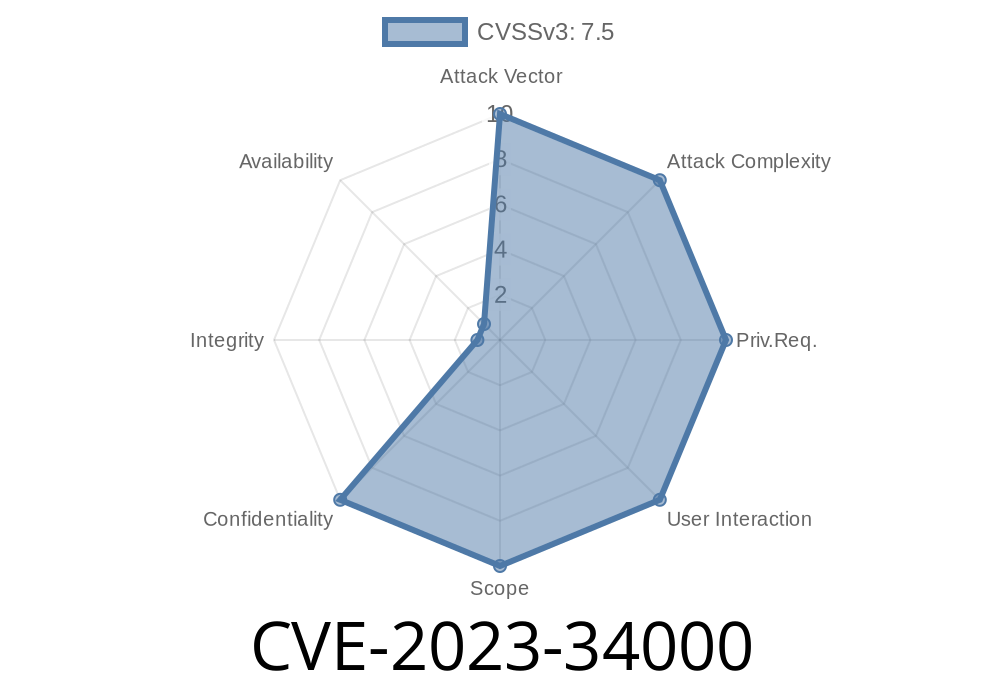
In June 2023, a major vulnerability was discovered in the popular WooCommerce Stripe Payment Gateway WordPress plugin affecting all versions up to 7.4.. This vulnerability – called CVE-2023-34000 – allows someone who isn’t logged in to your WooCommerce shop to view personal customer details, including payment info, using a common web attack called IDOR. Let’s break down what happened, how the exploit works, and why you should urgently update.
What is an "IDOR"?
IDOR stands for Insecure Direct Object Reference. Basically, a website trusts user-supplied IDs too much—like passing a customer ID in a URL without checking if the visitor is allowed to see it. If you change the ID in the link, you can get someone else’s data. This usually happens on endpoints (URLs) that are poorly protected.
Details of CVE-2023-34000
The plugin lets online shops accept credit card payments via Stripe. To do so, it processes and stores sensitive information, including personally identifiable information (PII): names, emails, order details, etc.
Vulnerability Overview
A public REST API endpoint in the plugin did *not* verify if a person was logged in or had the right permissions before serving private customer data, like payment intent and billing details. Any random visitor (even logged out!) could change the ID in the request and get access to others’ PII.
Impacted versions:
WooCommerce Stripe Payment Gateway <= 7.4.
Fixed in:
7.4.1
The Vulnerable Endpoint
The plugin registers a public REST endpoint for retrieving payment intents, which exposes billing details.
Example Code Snip (from vulnerable version)
// This is simplified for illustration.
add_action( 'rest_api_init', function () {
register_rest_route( 'wc-stripe/v1', '/payment-intents/(?P<id>[\w]+)', array(
'methods' => 'GET',
'callback' => 'wc_stripe_get_payment_intent',
// Note: No permission_callback used! No user check.
));
});
function wc_stripe_get_payment_intent( $request ) {
$intent_id = $request['id'];
// No user auth or check if current user can access this payment intent.
$order = get_order_by_payment_intent( $intent_id );
return $order->get_billing_details(); // Returns PII!
}
Real HTTP Request Example
A normal (intended) use:
GET /wp-json/wc-stripe/v1/payment-intents/pi_abcdef123456
What an attacker does:
Try sequential IDs (like pi_abcdef123457, pi_abcdef123458, etc.) to extract data from other users’ orders.
Full name
- Billing/shipping address
Order details (products, price)
- Stripe intent/payment info
Testing the Vulnerability
Warning: Only do this on your test site (never attack someone else’s site).
Open your browser or use a tool like curl
curl https://example.com/wp-json/wc-stripe/v1/payment-intents/pi_abcdef123456
You’ll see a full JSON with the details of the order, even if you’re logged out!
Change the id parameter (guess, increment, or scrape IDs), and you can get *any* order’s PII.
References
- Wordfence Advisory: Sensitive Information Disclosure in WooCommerce Stripe Payment Gateway
- Official WPScan Entry
- WooCommerce Stripe Payment Gateway changelog
How Was It Fixed?
After the report, the plugin added proper permission checks to the REST route. Here’s a corrected version:
register_rest_route( 'wc-stripe/v1', '/payment-intents/(?P<id>[\w]+)', array(
'methods' => 'GET',
'callback' => 'wc_stripe_get_payment_intent',
'permission_callback' => function() {
return current_user_can( 'view_woocommerce_reports' ); // Only shop managers/admins now!
},
));
*Now, only allowed users can use this endpoint.*
Review your REST API endpoints and use permission_callback for all sensitive data
- Monitor for any suspicious activity or GDPR/privacy complaints
Final Thoughts
CVE-2023-34000 is a good reminder: Even mature, top-tier plugins can have dangerous bugs. If you run a WooCommerce site, protecting your customers’ private info should always be top priority.
Check your plugins’ changelogs often and don’t delay security updates.
For more technical details or help, see the plugin’s GitHub page, and security advisories linked above.
Timeline
Published on: 06/14/2023 08:15:00 UTC
Last modified on: 06/21/2023 21:06:00 UTC