___
Introduction
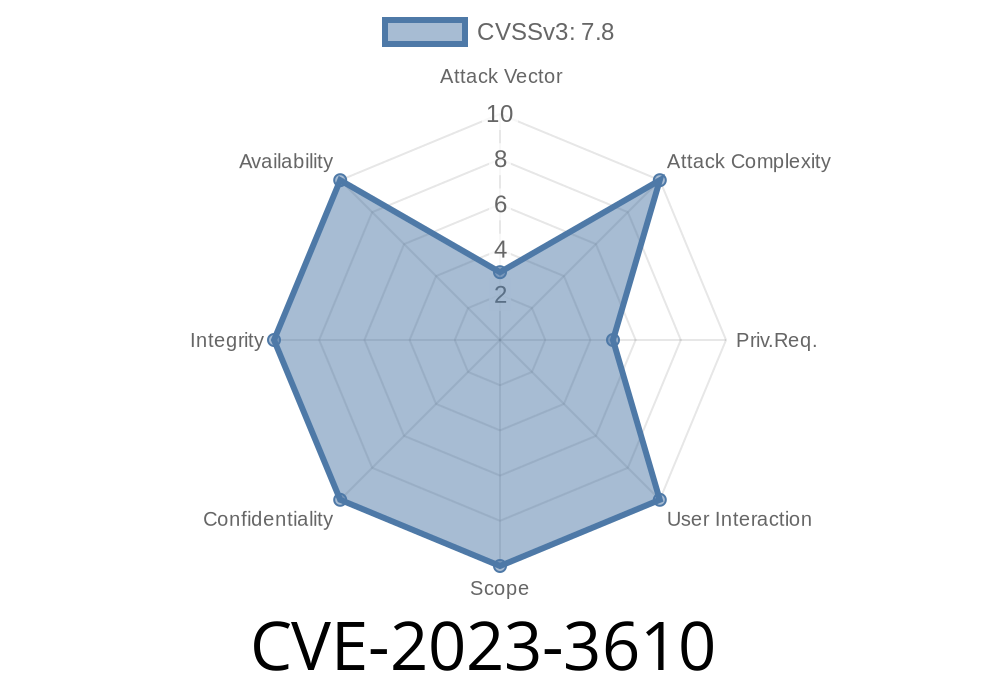
Security researchers recently discovered a use-after-free vulnerability in the Linux kernel's netfilter, specifically the nf_tables component. This security flaw, CVE-2023-3610, is a result of the error handling of bound chains and has been demonstrated to be capable of being exploited to achieve local privilege escalation. This issue requires CAP_NET_ADMIN, the Linux capability to administer network resources, to be triggered. We highly recommend updating your kernel to include commit 4bedf9eee016286c835e3d8fa981ddece5338795 or later versions to mitigate this potential security threat.
Code Snippet
The problematic code can be found in nf_tables when abort path of NFT_MSG_NEWRULE is triggered. This code is vulnerable to the attackers trying to exploit the use-after-free vulnerability in the error handling of bound chains.
static int nf_tables_newrule(...)
{
...
if (IS_ERR(chain)) {
nft_trans_destroy(trans);
return PTR_ERR(chain);
}
...
err = nf_tables_commit(...)
...
if (err < ) {
nf_tables_abort(...)
return err;
}...
}
Source: Linux kernel git reference
Exploit Details
By invoking the abort path of NFT_MSG_NEWRULE, attackers can gain escalated privileges on the local system. This occurs when the chain is in use and is improperly handled by nf_tables, causing a use-after-free situation. This can allow for arbitrary code execution, resulting in an attacker gaining unauthorized access to the target system.
Securing Your System
To protect against this vulnerability, it is strongly advised to upgrade your kernel to a version that has the fix incorporated. You can update to the kernel version past the following commit: 4bedf9eee016286c835e3d8fa981ddece5338795. For more information on how to update your kernel on various Linux distributions, please refer to your specific Linux distribution's documentation.
Original References
Please refer to the official Linux kernel git repository for more detailed information on this security vulnerability and the fix incorporated in commit 4bedf9eee016286c835e3d8fa981ddece5338795:
- Linux kernel commit
In conclusion, CVE-2023-3610 is a potentially dangerous use-after-free vulnerability in the nf_tables component of the Linux kernel's netfilter subsystem. To mitigate this risk, it's crucial to maintain an updated kernel that incorporates the relevant fixes and ensure that your systems' CAP_NET_ADMIN capability is strictly managed. By following the recommendations outlined above, you'll greatly reduce the likelihood of an attacker exploiting this vulnerability on your systems.
Timeline
Published on: 07/21/2023 21:15:00 UTC
Last modified on: 08/18/2023 14:15:00 UTC