---
Introduction
In June 2023, Microsoft disclosed a critical vulnerability in its MSHTML platform, tagged CVE-2023-36436. Exploiting this flaw lets attackers remotely execute code on a victim’s Windows machine through malicious web content. In this post, we'll explain how this vulnerability works in simple terms, show an example exploit, and point you to original resources for deeper investigation.
If you rely on Windows—especially for web browsing or opening files from untrusted sources—this is a must-read.
What is MSHTML?
MSHTML, also known as "Trident," is the legacy rendering engine behind Internet Explorer, and parts of it are still present in modern Windows for things like file previews and Office document views. Because it’s so widely integrated, even if you don't use Internet Explorer, you might still be at risk.
What is CVE-2023-36436?
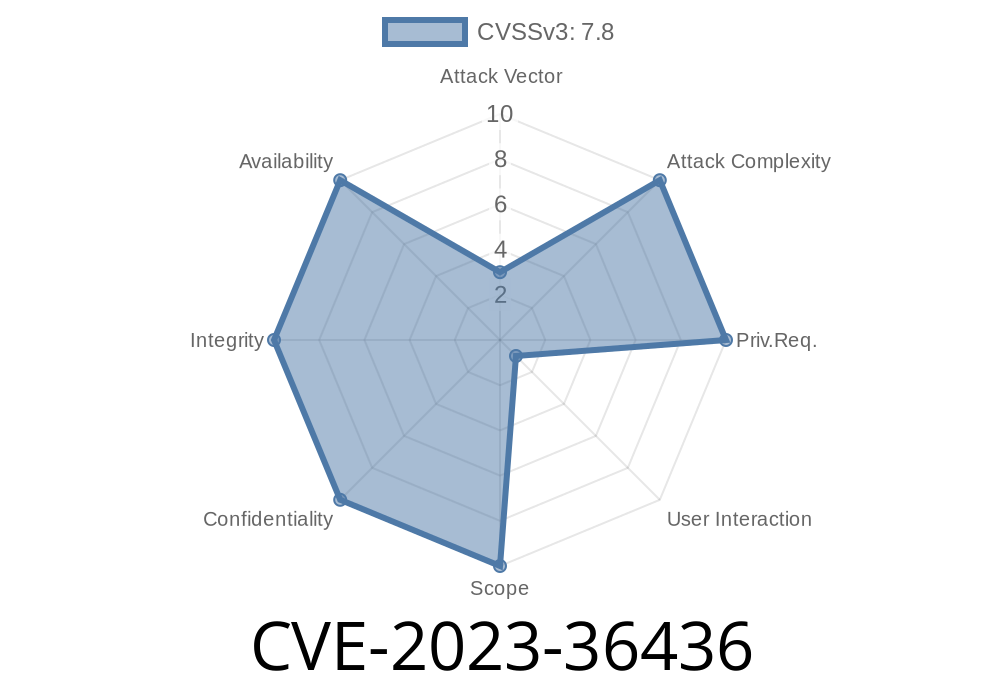
CVE-2023-36436 is a *remote code execution (RCE)* vulnerability that allows attackers to run arbitrary code on a victim’s computer. All an attacker needs to do is convince a user to open a specially-crafted file (like an Office document) or visit a rogue web page that uses MSHTML to render content.
Severity: Microsoft rated this as "Important", with a CVSS score of 7.5.
How Does the Exploit Work? (Simple Terms)
1. Attacker crafts a harmful file or web page, often using advanced HTML, JavaScript, or embedded objects.
Malicious code embedded in the content triggers the vulnerability inside the MSHTML engine.
4. If successful, the attacker gains the ability to execute their code—possibly installing malware, stealing data, or taking control of the victim’s machine.
Proof-of-Concept Exploit
Below is a simplified conceptual snippet demonstrating what part of an MSHTML/IE attack payload might look like. (This is *illustrative*—not a real-world weaponized exploit.)
Suppose an attacker creates a crafted HTML page using ActiveX
<!-- Dangerous HTML exploiting MSHTML object handling -->
<html>
<body>
<!-- ActiveX object initialization -->
<object classid="clsid:XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX" id="attackObject"></object>
<script>
try {
// Exploit-specific code here:
// For example, triggering an old method or property in a way that causes buffer overflow / RCE
document.getElementById('attackObject').vulnerableMethod('malicious_payload');
} catch(e) {
alert("Exploit failed: " + e.message);
}
</script>
</body>
</html>
*(Note: The real exploit would target a specific unpatched vulnerability deep inside MSHTML, possibly involving memory corruption.)*
Privileges Required: None (runs as the user)
- Bypassing Protections: Some exploits can skirt around defenses like Protected View in Office if the victim chooses to "Enable Editing".
How to Protect Yourself
1. Install Microsoft Updates: MSRC Security Update Guide for CVE-2023-36436
References
- Microsoft Security Response Center: CVE-2023-36436
- NIST NVD Entry
- CISA KEV List
- CVE Details - CVE-2023-36436
Final Thoughts
CVE-2023-36436 highlights the dangers of legacy components like MSHTML lurking in modern systems. Attackers keep finding new ways to exploit old code, making it crucial that you keep Windows and Office updated and be cautious about what you open or click.
Want to learn more about patching and security best practices? Check out Microsoft's official guide.
Timeline
Published on: 10/10/2023 18:15:12 UTC
Last modified on: 10/13/2023 17:21:16 UTC