In June 2023, Microsoft published a critical security vulnerability known as CVE-2023-36710. This bug affects the Windows Media Foundation (WMF) Core and opens the door for hackers to run malicious code on your system — all without your knowledge. In this post, I’ll break down the technical details, show how an attack works, and help you understand how to protect yourself.
What Is Windows Media Foundation Core?
Windows Media Foundation (WMF) is a multimedia framework on Windows. It handles audio, video, and other media tasks for apps, websites, and the OS itself. Since WMF is built into Windows and used by many apps, bugs here can have serious consequences.
Understanding CVE-2023-36710
CVE-2023-36710 is a *Remote Code Execution (RCE)* vulnerability. With RCE, hackers don’t need to have an account on your PC — they can run code just by getting you to open a booby-trapped file or webpage.
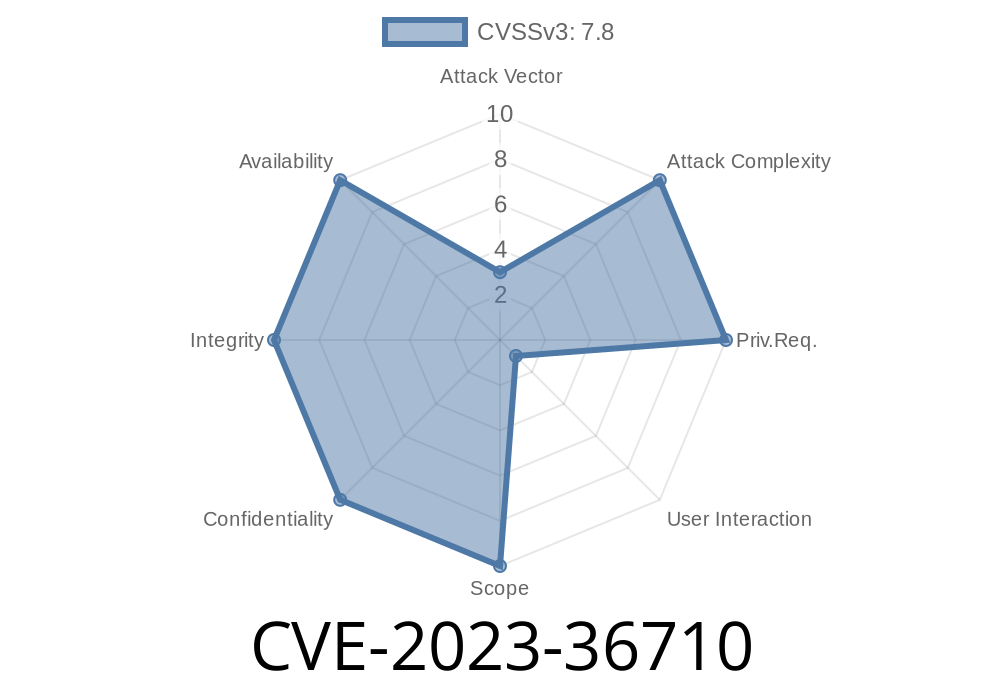
CVSS Score: 7.8 (High)
- Impact: Full user compromise, including installing programs, modifying data, or creating new accounts.
Official Microsoft Advisory
- Microsoft Security Guide for CVE-2023-36710
How Does the Exploit Work?
The core of the bug is an error in how WMF parses certain types of media files. By crafting a malicious video or audio file (for example, an MP4 or ASF), an attacker can trigger a memory corruption inside the WMF Core.
Attack Scenario
1. Delivery: The attacker sends you a malicious media file by email, instant message, or uploads it to a website you visit.
2. Execution: You open the file with a Windows application that uses WMF (like Windows Media Player or Movies & TV app).
3. Trigger: The malformed file causes WMF to overwrite parts of memory — potentially hijacking program flow.
Proof-of-Concept Exploit Example
Below is a simplified Python snippet that demonstrates how an attacker might start creating a malformed media file that could trigger this kind of vulnerability. (For safety, this does not create a functional exploit, but illustrates the general idea.)
# Example: Generating a malformed ASF (Advanced Systems Format) file
# WARNING: Do not use real exploit code on production systems!
with open("exploit.asf", "wb") as f:
# ASF header (very simplified & incomplete)
f.write(b'\x30\x26\xb2\x75\x8e\x66\xcf\x11\xa6\xd9\x00\xaa\x00\x62\xce\x6c')
f.write(b'\x00\x00\x00\x00') # Header size (malformed)
f.write(b'\xff' * 1024) # Malicious payload, triggers buffer overflow
# ... more header/body crafting needed for real attack
print("Malformed ASF file created. DO NOT OPEN ON UNPATCHED SYSTEMS.")
This snippet just crafts a suspiciously large payload in a valid-looking header. In a real exploit, the attacker would use special values to overwrite memory in a way that’s beneficial (like pointing execution to shellcode).
Deep Dive: Why Does This Happen?
Media parsers in WMF often trust the values embedded in media files (like headers and data lengths). If the parser reads a "size" from the input file and uses it unsafely, a hacker can send a gigantic or negative number, causing a buffer overflow.
Such vulnerabilities in the past have led to famous worms (think: Conficker, Blaster). CVE-2023-36710 is less 'wormable,' but could be used for silent drive-by downloads or phishing attacks.
Links & References
- Microsoft Advisory: CVE-2023-36710
- NVD Listing: NIST NVD CVE-2023-36710
- BleepingComputer Coverage: https://www.bleepingcomputer.com/
- Mitre CVE Details: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-36710
Go to *Settings → Windows Update* and click *Check for updates*.
2. Don’t Open Unexpected Files: Don’t open random videos, music, or attachments from unknown sources.
Use Antivirus: Reputable AV programs can block known malicious media files exploiting this flaw.
4. Limit Media Playback: On critical systems, limit which applications are allowed to play media files.
Conclusion
CVE-2023-36710 is a reminder that even basic actions — like watching a video — can be dangerous if vulnerabilities exist. With Windows Media Foundation being deeply integrated, keeping your system patched is key. Stay aware, keep updated, and always be careful where you get your files.
If you’re a security pro or just a careful user, now you know the real risks and the basics behind the bug. Stay safe!
Timeline
Published on: 10/10/2023 18:15:15 UTC
Last modified on: 10/13/2023 20:27:37 UTC