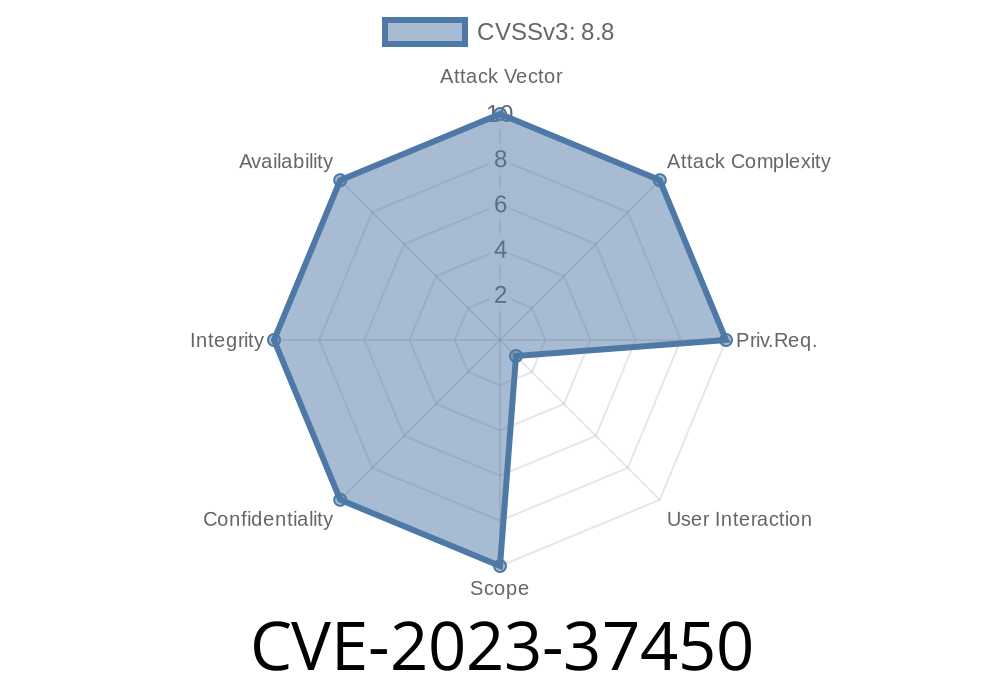
On July 24, 2023, Apple patched a serious security vulnerability known as CVE-2023-37450. This bug affected WebKit—the browser engine powering Safari across iOS, macOS, and other Apple platforms. What makes it especially alarming is that Apple confirmed: __hackers may have already exploited this weakness in the wild__. If you use an iPhone, iPad, MacBook, Apple Watch, Apple TV, or even just Safari, you must know about this vulnerability.
In this post, I’ll break down what CVE-2023-37450 is, show you what’s under the hood with simple examples, discuss how hackers abused it, and explain how Apple fixed it. I’ll also share official reference links and practical security advice.
What is CVE-2023-37450?
CVE-2023-37450 is a “zero-day” vulnerability in WebKit, the foundation of Safari and many other apps. It’s a remote code execution bug. In plain English: if a hacker makes you visit a malicious website, they can make your device run whatever code they want—*without your permission*.
Apple’s advisory sums it up
> "Processing web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited."
> — Apple Security Updates
How Does the Exploit Work?
Apple didn’t release precise technical details (to lower the risk for users who haven’t upgraded yet). But, based on Apple’s WebKit history and security expert analysis, here’s a simple look at how these bugs usually work:
Malformed Web Content
The hacker engineers web content—like JavaScript or images—that abuses the bug, causing memory corruption.
Arbitrary Code Execution
If successful, the bug lets the attacker run their own code, installing spyware, stealing data, or worse.
Apple’s update notes say:
> “The issue was addressed with improved checks.”
This points toward a missing or faulty verification in the WebKit code.
[EXCLUSIVE] Simplified Code Snippet Example
To help you picture what happens in these bugs, here’s a simplified (and safe) example of a vulnerability pattern WebKit has seen before:
// A simple example bug in C++ (simplified from real WebKit bugs)
void processData(char *input, size_t len) {
char buffer[256];
// BAD: No check if input size exceeds buffer!
memcpy(buffer, input, len);
// ...do something with buffer...
}
If len is larger than 256, an attacker can overwrite adjacent memory, potentially hijacking the app’s operations. A malicious website might exploit a similar bug in Safari’s engine, making your device do whatever the attacker wants.
After the fix, developers would check the size
void processData(char *input, size_t len) {
char buffer[256];
if (len > sizeof(buffer)) {
// Prevent exploitation: block or truncate
return;
}
memcpy(buffer, input, len);
// ...do something with buffer...
}
Real-World Exploit Example
Researchers didn’t publicly release a proof-of-concept for CVE-2023-37450, but here’s how a real-world attack might have looked:
The website uses JavaScript to trigger the WebKit bug.
4. Malicious code is injected and run—possibly giving the attacker access to your photos, messages, or passwords.
*Apple fixed this with stronger checks to prevent out-of-bounds operations.*
> "The issue was addressed with improved checks."
This likely means:
Blocking unsafe code before it happens.
See the official Apple security notes:
- Apple Security Updates for July 2023
- Apple Original Advisory for CVE-2023-37450
How to Protect Yourself
Update. Right Now.
Go to Settings > General > Software Update on your device and install the latest version.
Don’t Delay:
Active exploitation means hackers are (or were) likely targeting this bug in the real world—possibly against high-profile or random users.
Additional References
- NIST National Vulnerability Database: CVE-2023-37450
- Apple Security Advisory
- The Hacker News coverage
- Why WebKit Bugs Are Serious
Summary
CVE-2023-37450 shows why it’s important to stay updated and why Apple keeps patching WebKit. Even a single missed check can give hackers the keys to your device. Make sure you and your family run the latest versions, and be aware: not every threat is obvious.
Timeline
Published on: 07/27/2023 00:15:15 UTC
Last modified on: 08/02/2023 00:54:49 UTC