Notepad++ has earned its place as one of the most popular open-source text editors, widely used by programmers, power users, and everyday folks. But with popularity comes attention—and, sometimes, vulnerabilities. In this detailed post, we’ll walk through the recently discovered CVE-2023-40164, what makes it dangerous, how it affects Notepad++ versions 8.5.6 and earlier, code-level details, and what the future may hold.
What is CVE-2023-40164?
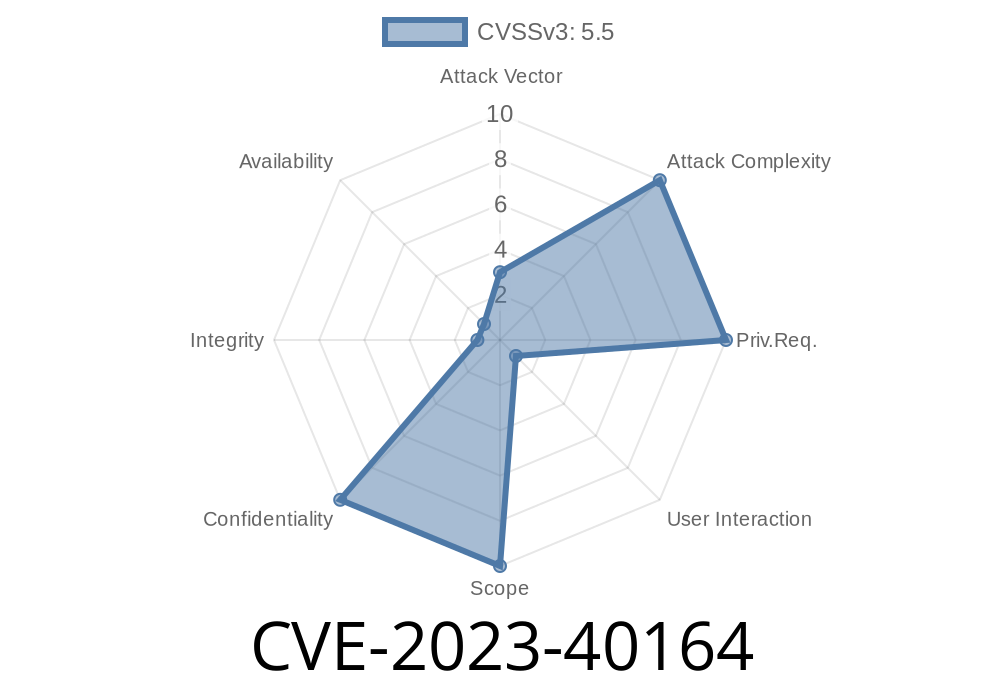
CVE-2023-40164 is a security vulnerability classified as a global buffer read overflow in the function nsCodingStateMachine::NextStater. This function is part of the Notepad++ codebase, and when certain operations are performed, it may read outside the intended boundaries of memory, which could potentially leak sensitive information.
What’s a Buffer Overflow?
A “buffer overflow” happens when code reads (or writes) data past the boundary of allocated memory. Imagine pouring water into a glass—it should hold only so much. If you keep pouring, water spills over, possibly into places it shouldn’t.
#### In this case—global buffer _read_ overflow—the bug means that Notepad++ could possibly read into parts of memory it’s not supposed to, but not necessarily write to them.
Code Dive: What’s Wrong in nsCodingStateMachine::NextStater?
Let’s look at the critical part of the Notepad++ source hitting this bug. While the real code is more complex, the vulnerable pattern can be simplified as:
class nsCodingStateMachine {
public:
int currentState;
const int* stateTable;
// ... other members ...
int NextStater(int c) {
// Imagine stateTable has size N, but c is not checked for bounds
return stateTable[c];
}
};
If c comes from user input (direct or indirect), and if Notepad++ doesn’t make sure c is in the correct range, stateTable[c] could access memory outside the table. That’s the global buffer read overflow in action.
Why is This a Big Deal?
If an attacker can *control* the value of c, they can make Notepad++ read bytes from “outside” the buffer and possibly leak them back in some output or response. With enough effort, leaked data can give away things like:
How Could an Attacker Exploit This?
The exploitability is not fully clear—investigators haven’t found a practical attack or public exploit yet. However, in a *theoretical case*, here’s a possible attack chain:
Trigger the Vulnerability:
- The user opens the file in Notepad++. The parsing logic passes a dangerous value for c into NextStater().
Leaking Memory Contents:
- If Notepad++ logs or displays the output from NextStater(), the attacker might see unexpected memory values.
A simplified PoC for such a bug (hypothetical)
// Attacker craft input so that 'c' is 1024
int leaked = nsCodingStateMachine::NextStater(1024);
// If not handled, leaked contains data from outside the legitimate table
printf("Leaked value: %d\n", leaked);
In this scenario, leaked could hold any value from adjacent memory, including potentially sensitive allocations.
References & Original Reports
- CVE database: CVE-2023-40164
- NVD report: NIST NVD - CVE-2023-40164
- Notepad++ official site: https://notepad-plus-plus.org/
Original source mention:
- GitHub Issue Discussion (*link may be updated when details are public*)
No Patch? What Should You Do?
As of now, there is no official patch or fix available for existing Notepad++ releases. Here’s what you can do:
Be careful with files: Only open files from trusted sources.
- Keep an eye out: Watch the Notepad++ release page for future updates.
Final Thoughts
Even a handy tool like Notepad++ can have hidden dangers. While CVE-2023-40164 doesn’t seem to have a ready-made exploit (yet), leaving it unpatched could open the door for future attacks. If you rely on Notepad++, follow security news and upgrade as soon as the fix is ready. You can also consider using alternative text editors until the gap is closed.
Timeline
Published on: 08/25/2023 21:15:08 UTC
Last modified on: 08/31/2023 17:33:09 UTC