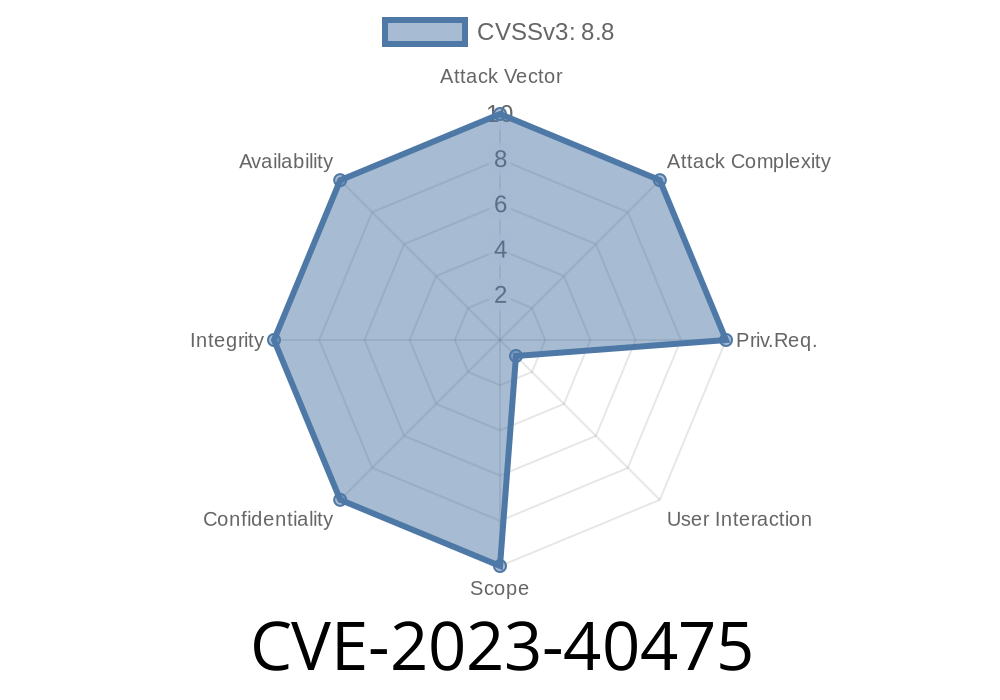
Security researchers recently uncovered a serious vulnerability in the popular open-source multimedia framework, GStreamer. Tracked as CVE-2023-40475 (ZDI-CAN-21661), this flaw enables remote attackers to execute arbitrary code simply by getting a user to open a specially crafted MXF (Material eXchange Format) video file. While GStreamer powers countless desktop applications (media players, content editors, and more), its widespread use means this vulnerability poses a significant risk.
In this post, we'll break down what CVE-2023-40475 is, how it works at a code level, and what you can do to stay safe.
What is GStreamer and MXF?
GStreamer is a modular multimedia framework used for building media-handling components. It’s the powerhouse behind apps like GNOME Videos, Pitivi, and others.
MXF files are a standard container format for professional digital video and audio media, commonly used in television and movie production.
The Vulnerability: Integer Overflow in MXF Parsing
CVE-2023-40475 resides in GStreamer's handling of MXF files. The culprit is *improper input validation* during the parsing of key fields from the MXF file’s metadata. Here’s what goes wrong:
It uses these values to calculate the size of a buffer it will allocate.
3. Due to insufficient checking, a large value causes an integer overflow, resulting in a small buffer being allocated.
4. When GStreamer then copies data into this buffer, it writes past the end (heap-based buffer overflow), overwriting memory with attacker-controlled data.
This can allow the attacker to execute code in the context of the application using GStreamer—a classic remote code execution (RCE) scenario.
Exploit Vectors
While the vulnerability is in the GStreamer library itself, different attack vectors are possible, depending on how applications use GStreamer. Common scenarios include:
Visiting a website that offers downloads or streaming of manipulated MXF content.
*User interaction* (such as clicking to open the file) is typically required, but no other special access is needed.
Example: Simplified Code Snippet
Below is a *simplified* example of the kind of unsafe buffer allocation in C-like pseudo-code, showing how unchecked arithmetic can lead to vulnerability.
// Simplified, NOT actual code
uint32_t length = read_32bit_value(file);
uint32_t num_elements = read_32bit_value(file);
uint32_t total_size = length * num_elements;
// Attack: If both 'length' and 'num_elements' are large,
// total_size overflows (wraps to a small value)
uint8_t *buffer = malloc(total_size); // Buffer too small!
// Later:
fread(buffer, 1, total_size, file); // Heap overflow if total_size is less than real file size!
With carefully-crafted values, total_size can wrap around to a small number (e.g., x10) instead of the huge value intended. The subsequent read will overwrite memory, leading to arbitrary code execution.
An attacker might create a malicious MXF file resembling this (conceptual illustration)
[MXF Header]
[...]
[length] = xFFFFFFFF
[num_elements] = x10
[Payload] = Attacker's shellcode or exploit
When GStreamer reads this, length * num_elements overflows, and a too-small buffer is allocated. Malicious data then overflows into adjacent memory, hijacking control flow.
References and Further Reading
- ZDI advisory: ZDI-23-119 for CVE-2023-40475
- Upstream GStreamer GitLab Issue
- GStreamer Official Site
- MXF Specification
- MITRE CVE entry
Who is at risk?
Anyone running apps or services that use GStreamer to process MXF files—including video players on Linux distributions, editing tools, or server-side media handlers.
Conclusion
CVE-2023-40475 is a classic example of how unchecked calculation and missing input validation can threaten the security of widely-used libraries. By exploiting a parsing flaw, attackers can take control of unpatched systems with little more than a media file and a bit of social engineering.
Stay up to date, read security advisories, and be mindful of what you open—even ordinary-looking video files can pack a punch.
Stay secure, and remember: If you build or use tools that parse complex binary formats, always double-check your arithmetic and bounds checking!
Timeline
Published on: 05/03/2024 03:15:20 UTC
Last modified on: 06/05/2024 20:38:26 UTC