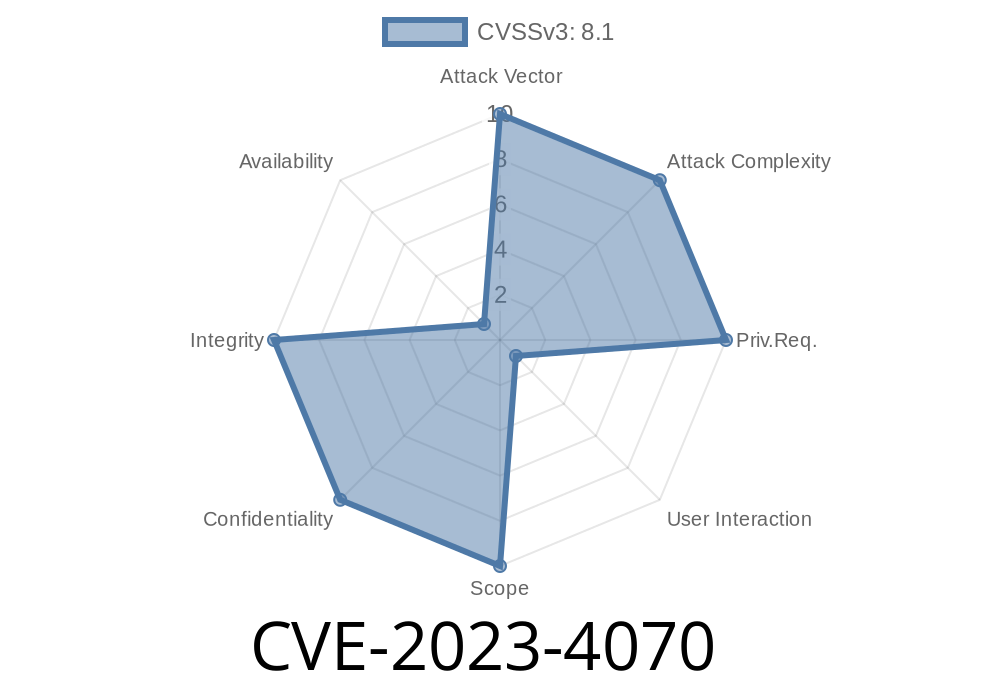
A security vulnerability (CVE-2023-4070) has been identified in the V8 JavaScript engine, used by Google Chrome, affecting versions prior to 115..579.170. This high-severity vulnerability allows a remote attacker to perform arbitrary read and write actions on user data via a specifically crafted HTML page. In this long-read post, we will discuss the details of this vulnerability, provide code snippets, and outline the steps needed to exploit the vulnerability. We will also provide links to original references and discuss the patch released by Google to address the issue.
Details of the Vulnerability
Known as Type Confusion, this vulnerability is a result of improper handling of object types within the V8 JavaScript engine. In programming languages like JavaScript, data can be organized into various types such as integers, strings, or objects. The vulnerability arises when the V8 engine incorrectly interprets the type of an object, resulting in unexpected behavior that can lead to the execution of malicious code.
Exploit Details
An attacker can exploit CVE-2023-4070 by crafting a malicious HTML page that contains specially designed JavaScript code. This code, when executed, triggers the Type Confusion vulnerability within the V8 engine, enabling the attacker to read and write arbitrary user data.
Here's an example code snippet that demonstrates how this vulnerability might be exploited
// JavaScript code to exploit CVE-2023-4070
// Trigger the Type Confusion vulnerability in V8
function exploit_type_confusion() {
var obj = {
propA: 42, // Integer
propB: "Hello, world!" // String
};
// Cause Type Confusion by manipulating object properties
for (var i = ; i < 10; i++) {
delete obj.propB;
obj.propB = i; // Change the type of propB
}
// Perform arbitrary read/write actions
return obj;
}
// Load the malicious HTML page and exploit the vulnerability
window.onload = function() {
var malicious_obj = exploit_type_confusion();
// Perform malicious actions using the vulnerable object
};
By visiting the malicious web page containing this code, unsuspecting users could unknowingly grant read and write access to their data.
Original References
The Chromium Project, responsible for maintaining Google Chrome, has tracked this vulnerability as "chromium:1259103" in their issue tracker:
- Chromium Issue Tracker - chromium:1259103
The Google Security Research team, which discovered the vulnerability, has published an extensive analysis of the issue:
- Google Security Research - Type Confusion in V8
Mitigation
To protect against CVE-2023-4070, Google has issued a patch available in Google Chrome version 115..579.170. Users are strongly encouraged to update their browsers to this version or later.
Additionally, users should exercise caution when visiting unknown web pages or clicking on links from untrusted sources, as these actions could lead to the execution of malicious JavaScript code exploiting this vulnerability.
Conclusion
CVE-2023-4070 is a high-severity Type Confusion vulnerability in the V8 JavaScript engine that has the potential to grant remote attackers arbitrary read and write access to user data. By updating Google Chrome to version 115..579.170 or later, users can protect themselves from this threat. Security awareness and cautious web browsing are also essential to help prevent exploitation of this and other similar vulnerabilities.
Timeline
Published on: 08/03/2023 01:15:00 UTC
Last modified on: 08/05/2023 04:15:00 UTC