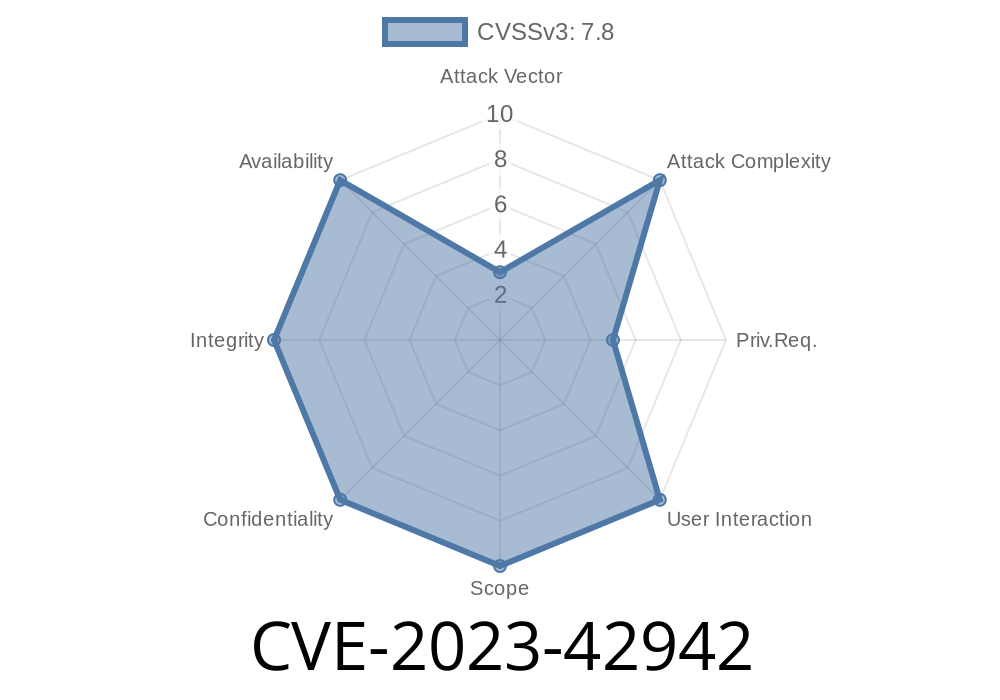
CVE-2023-42942 is a security issue Apple patched in October 2023. This vulnerability could allow a malicious app to gain root privileges on a device, meaning the attacker could have the highest level of control possible—not just as a regular user, but as the system administrator. This issue was triggered by improper handling of symbolic links (symlinks) in the affected operating systems.
iOS 16.7.2 and iPadOS 16.7.2
If you haven’t updated your device, you’re at risk.
Apple’s official note:
> “A malicious application may be able to gain root privileges. This issue was addressed with improved handling of symlinks.”
> (Apple Security Releases)
How Does The Vulnerability Work?
Symlinks (short for symbolic links) are a kind of shortcut used in UNIX-like systems (like macOS, iOS, and tvOS). They look like files, but they actually point somewhere else in the filesystem.
Here's the basic problem
*If code running as a low-privilege user tricks a privileged process (like one running as “root”) into writing to a symlink that it controls, it might be able to write to any system file, giving the attacker root control. This is sometimes called a “symlink attack.”*
Imagine there’s a secure folder only root can change. But if root is tricked into writing to a symlink instead of a normal file, that write might go somewhere harmful.
Here's a simplified version of how such an exploit might work
1. Create a malicious application that creates a symlink in a place where a privileged process is expected to write a temporary file.
2. Point the symlink to a sensitive system file (for example, /etc/sudoers or another root-owned file).
3. When the privileged process runs, it unknowingly writes data to the symlink, which actually affects the target file.
4. This could let the attacker inject data or change permissions, effectively granting themselves root privileges.
Here’s how you might make a symlink attack in Python, targeting a macOS system
import os
# Path where the privileged process will write, as expected
target_path = "/tmp/secure_temp_file"
# The sensitive file we want to overwrite (DANGEROUS, DO NOT RUN)
sensitive_file = "/etc/sudoers"
try:
os.remove(target_path) # Remove if it already exists
except FileNotFoundError:
pass
# Create symlink
os.symlink(sensitive_file, target_path)
print(f"Symlink created: {target_path} -> {sensitive_file}")
# Now, if a privileged process writes to /tmp/secure_temp_file,
# it will actually overwrite /etc/sudoers (requires exploit conditions).
*Note: This code is for educational demonstration only. Never run code like this on your system!*
Bypass nearly all OS security protections
This makes vulnerabilities like CVE-2023-42942 extremely serious.
Fixes and Mitigations
After CVE-2023-42942, Apple improved how their operating systems check and process symlinks, making sure that privileged processes don’t blindly follow them during critical operations.
The best protection:
References & Further Reading
- Apple Security Release Notes (CVE-2023-42942)
- NIST NVD Entry for CVE-2023-42942
- Symlink Attack Explanation (OWASP)
- Apple Security Updates
- Red Team Blog: Symlink Races and Privilege Escalation
Conclusion
CVE-2023-42942 is a classic example of how small mistakes with file handling can lead to massive security issues, even for companies like Apple. If you haven’t updated your iPhone, iPad, Mac, Apple Watch, or Apple TV since October 2023, do it now to stay protected!
Timeline
Published on: 02/21/2024 07:15:50 UTC
Last modified on: 08/27/2024 16:35:01 UTC