---
Introduction
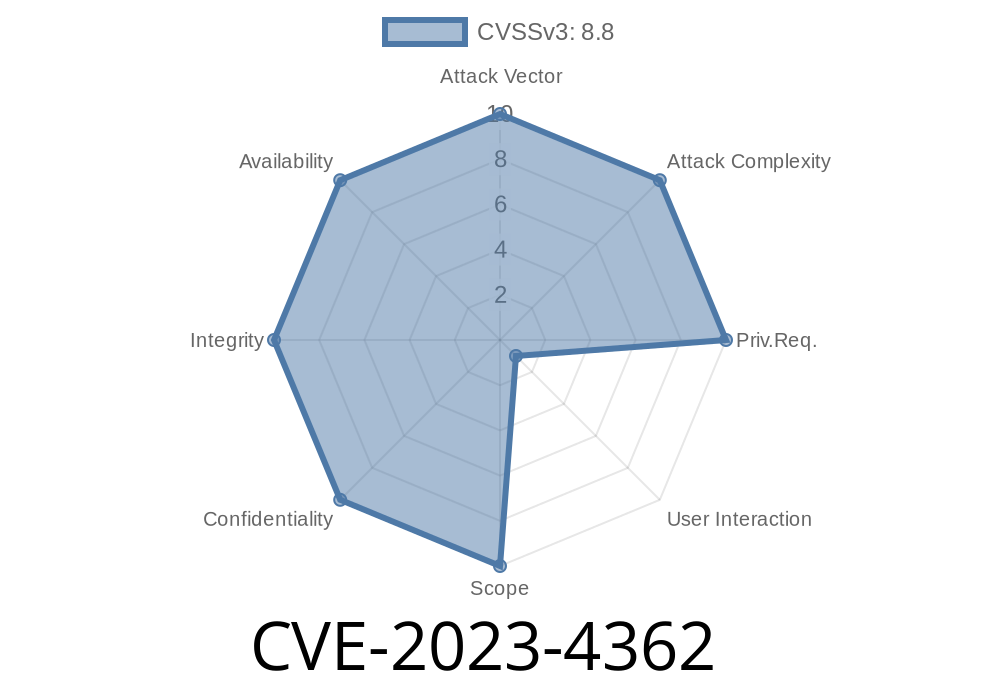
In August 2023, Google Chrome patched a new vulnerability: CVE-2023-4362. This bug hides inside the "Mojom IDL" part of Chrome, allowing attackers to potentially corrupt the browser's memory and do much more damage—if they already have a foothold in the renderer process. Here, we'll break down what the bug is, what an attacker needs, how an exploit might work, and show you sources and code along the way.
What is Mojom IDL?
Mojom IDL (Interface Definition Language) is a part of Chrome’s messaging system (Mojo IPC). It's how separate processes (like tabs or browser windows) safely talk to each other. If something in Mojom is coded wrong, it can let data sneak past the lines where it shouldn’t.
Component: Mojom IDL (Chrome’s inter-process communication)
- Severity: Medium (Chromium Bug Tracker)
Patched Version: 116..5845.96
- What could happen? Heap buffer overflow — a classic “writing too much data” issue that can corrupt memory and let hackers do unexpected things.
Official Description
> Heap buffer overflow in Mojo. ... allowed a remote attacker who has compromised the renderer process and controlled a WebUI process to potentially exploit heap corruption via a crafted HTML page.
In plain English:
If an attacker already got code running in one Chrome tab (renderer process), and can talk to a special part of Chrome called WebUI, they can send evil data across Mojom’s message lines. That can overwrite memory in the browser, maybe running new code or crashing the app.
Where Is the Bug?
- Affected File: mojom_blink.idl
Here’s what a real attack could look like, step by step
1. Initial compromise: Attacker finds a bug in Chrome’s renderer, like in JS or image processing, gets code running there.
2. WebUI access: They use this to open or redirect to a Chrome page using WebUI (for example, chrome://extensions).
3. Crafted message: They send a message to WebUI using Mojom IDL, sizing data to be just right (or wrong).
4. Overflow: WebUI code parses the message, overruns its buffer, and now the attacker controls memory in the privileged WebUI process.
Vulnerable Code Pattern
// Pseudocode illustrating the bug
struct SomeMojomStruct {
uint32_t size;
char data[AN_EXPECTED_MAX_SIZE];
};
// Somewhere in parsing:
void Parse(const uint8_t* input, size_t len) {
SomeMojomStruct* obj = new SomeMojomStruct;
memcpy(obj->data, input, len); // No length check!
}
Exploit Payload Example
An attacker could use JavaScript and a compromised renderer context to send an abnormally large payload:
// JavaScript running in compromised renderer context
// (requires earlier bug/chrome exploit chain)
const forgePayload = (size) => {
let arr = new Uint8Array(size);
// Fill with arbitrary data, could include ROP chain, shellcode, etc.
arr.fill(x41);
return arr.buffer;
};
// Send big payload that overruns expected size
chrome.webui.send('vulnerableMojomMethod', forgePayload(4096));
When the WebUI-side handler (vulnerableMojomMethod) tries to parse this, it can overrun internal buffers, leading to heap corruption.
Real Exploit? Who’s at Risk?
This bug is not a one-click remote exploit. The attacker needs to already compromise the Chrome renderer (like with another exploit). That's why the rating is only "medium". Still, in the world of browser chains—stacking multiple bugs together—this is a serious piece of the puzzle.
Patch & Fix
Google closed the hole in Chrome version 116..5845.96. The fix included stronger size checks during Mojom IDL parsing.
Fixed Pattern (Pseudocode)
if (len > EXPECTED_MAX_SIZE) {
// Error: input too large
return false;
}
memcpy(obj->data, input, len);
More Details
- Chromium Security Bug: Issue 1460486
Release Notes:
- Chrome 116..5845.96 Security Fixes
Mojom Overview:
Other writeups:
Conclusion
CVE-2023-4362 is classic browser plumbing: an attacker would need a foot in the door, but with that, could use Mojom IDL's missing checks to heap overflow a buffer. Always keep your Chrome updated!
TL;DR:
Chrome <116..5845.96 is vulnerable if an attacker already has renderer code execution—they could use Mojom messages to smash WebUI process memory. Update Chrome. Stay safe!
Links & References
- Chromium Issue Tracker #1460486
- Chrome 116 Release Blog
- Project Zero: Exploiting Vulnerabilities in Chrome
- Mojo IPC in Chromium
Timeline
Published on: 08/15/2023 18:15:00 UTC
Last modified on: 08/27/2023 03:15:00 UTC