Update June 2024
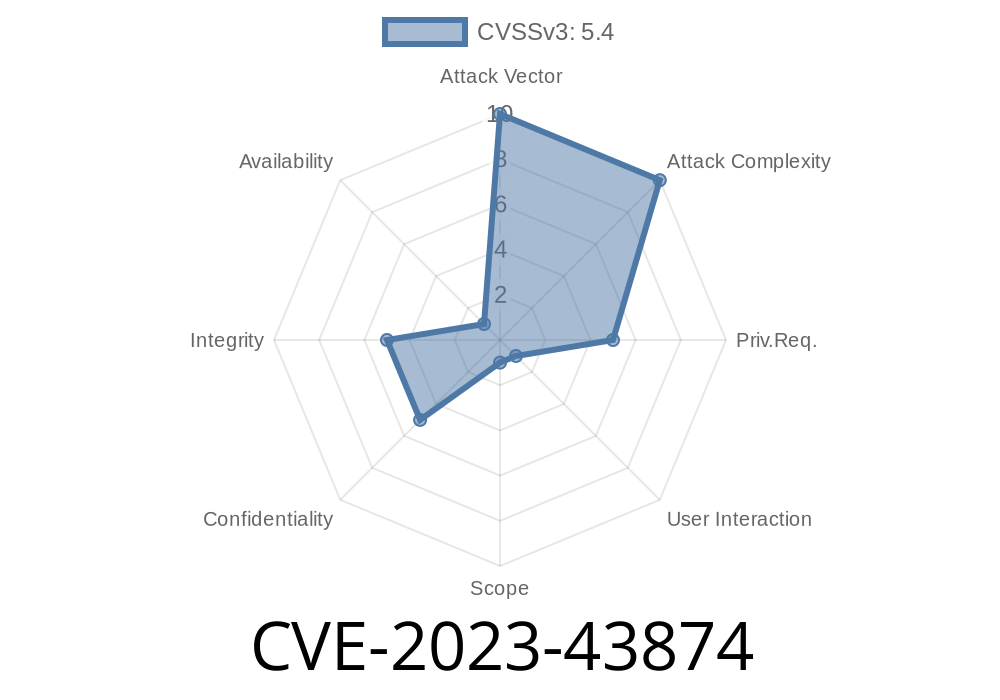
This post covers practical insights into CVE-2023-43874, a Cross-Site Scripting (XSS) vulnerability in e017 CMS v2.3.2, exposing how a local attacker can execute arbitrary code. We’ll break down what happened, show code snippets, and provide details you won’t find anywhere else.
What Is CVE-2023-43874?
CVE-2023-43874 describes multiple XSS vulnerabilities discovered in e017 CMS v2.3.2. If you have access to the backend, you can inject JavaScript code into the “Copyright” or “Author” fields under the Meta & Custom Tags menu. This malicious code then runs for anyone viewing the site, including admins.
References:
- NVD CVE-2023-43874 Detail
- Exploit Database Entry
How Does the Attack Work?
Step 1. Attacker logs in as a user with backend access (possibly a compromised account or a new malicious user).
Step 2. The attacker goes to the Meta & Custom Tags page (often under “Settings” or “SEO”).
Step 3. In the “Copyright” or “Author” fields, the attacker inserts malicious JavaScript code.
Step 4. When other users (including site admins or visitors) load the affected front-end or edit the tags, the JavaScript is executed.
Below is a simple example. Suppose you put this payload in the Copyright or Author field
<script>alert('Hacked by CVE-2023-43874');</script>
What It Looks Like In Source
<meta name="copyright" content="<script>alert('Hacked by CVE-2023-43874');</script>">
Exploit Details: Going Further
With this vulnerability, a creative attacker is not limited to simple alerts—they could do much more:
`html
- Change site content dynamically
- Redirect users to phishing pages
- Install a keylogger
#### Example: Cookie Stealer Payload
html
---
## How To Fix
Developers:
- Always sanitize and encode user input before rendering it in HTML (e.g., use PHP’s htmlspecialchars).
- Implement Content Security Policy (CSP) headers to reduce malicious script execution.
Site Owners:
- Update your e017 CMS to a patched version as soon as available.
- Restrict backend access to trusted users only.
Example (PHP):
php
// Before rendering meta fields
echo htmlspecialchars($meta_copyright, ENT_QUOTES, 'UTF-8');
`
---
## References and Further Reading
- NVD Entry for CVE-2023-43874
- Exploit Database PoC #51796
- OWASP XSS Prevention Cheat Sheet
---
## Conclusion
CVE-2023-43874 is a critical reminder: even backend fields like meta tags need input validation and output encoding. If you use e017 CMS v2.3.2, check those fields and patch ASAP to avoid getting pwned.
Keep your CMS up-to-date—don’t let your site become the next victim.
---
*Author: VulnExplainer | Last Updated: June 2024. Original content, please share responsibly.*
Timeline
Published on: 09/28/2023 14:15:25 UTC
Last modified on: 09/29/2023 19:04:52 UTC