Exiv2 is a popular open-source C++ library and command-line tool for managing image metadata, such as Exif, IPTC, XMP, and ICC data. It’s widely used by many applications to read, edit, or delete metadata from photos. However, a recent vulnerability—CVE-2023-44398—has been discovered that puts users of Exiv2 v.28. at risk.
In this post, we break down what CVE-2023-44398 is, how it works, what the risks are, and how you can stay safe.
[Proof of Concept (PoC) Exploit](#proof-of-concept-poc-exploit)
- [How to Fix / Patch](#how-to-fix--patch)
[Further Reading](#further-reading)
---
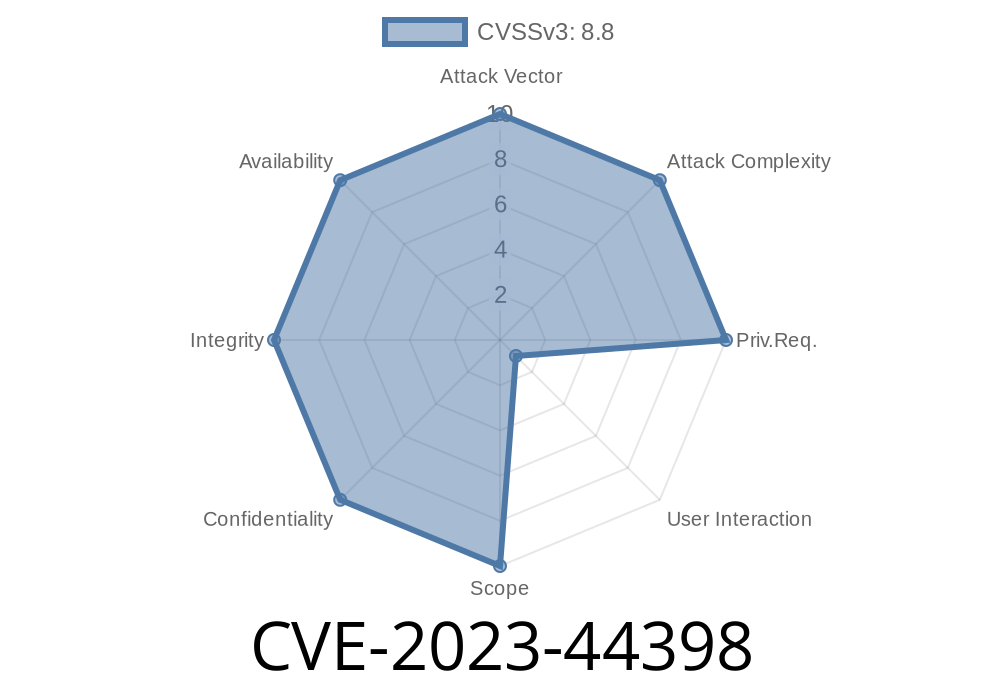
What is CVE-2023-44398?
CVE-2023-44398 is an out-of-bounds write vulnerability that was introduced in Exiv2 version v.28., specifically within the new BmffImage::brotliUncompress function. Earlier versions are _not_ affected.
The vulnerability is triggered when Exiv2 reads a specially-crafted image file.
- This can result in memory corruption, potentially leading to remote code execution if an attacker convinces you to process their malicious image file.
The bug has been fixed in Exiv2 v.28.1.
> BOTTOM LINE: If you’re using Exiv2 v.28., upgrade immediately to v.28.1 or later. There are _no workarounds_.
Technical Details
The problem lies in how BmffImage::brotliUncompress handles decompression. If it trusts size values from the file without proper bounds-checking, a maliciously-formed file can cause Exiv2 to write data past the end of allocated memory (out-of-bounds write). If an attacker controls the data being written, this could let them execute arbitrary code.
Here's what a dangerous code path might look like in C++ (simplified for explanation)
size_t decompressedSize = get_decompressed_size_from_file(file);
std::vector<uint8_t> buffer(decompressedSize);
size_t ret = BrotliDecoderDecompress(
compressedSize, compressedData,
&decompressedSize, buffer.data()
);
// Vulnerability: If decompressedSize is too large, buffer overflows
The attacker crafts an image with malicious metadata.
- The victim runs exiv2 (or any software using the vulnerable library) to extract or process metadata.
1. Craft the Malicious Image
Use tools like vim, dd, or a simple hex editor to inject bad values into the image’s metadata section. For example, setting size fields to extremely large values.
2. Run Exiv2 against the image
exiv2 -pa crafted_image.heic
Result: The vulnerable version (v.28.) might crash, hang, or, in the worst case, execute arbitrary code.
Here’s a minimal example in Python that creates a malicious file (for educational purposes)
with open("exploit.heic", "wb") as f:
# Write fake BFMT header and very high decompressed size value
f.write(b"\x00" * x200) # fake header
f.write(b"\x00" * 1024) # fake Brotli data with bad size
# (In real exploits, you'd make a valid BFMT file but set decompressed size field to huge value)
Warning: _Do not run this on any production system!_
## How to Fix / Patch
Solution:
*Upgrade to Exiv2 v.28.1 or later.*
# If using a Linux distribution:
sudo apt update
sudo apt upgrade exiv2
# Or build from source:
git clone https://github.com/Exiv2/exiv2.git
cd exiv2
git checkout v.28.1
cmake .
make
sudo make install
There are no workarounds.
Further Reading
- Official CVE Description
- Exiv2 GitHub Security Advisory
- Exiv2 Release .28.1 Changelog
- A Guide to ExifTool and Exiv2
Summary
If you use Exiv2—directly or through any graphical apps—CVE-2023-44398 is a critical bug that lets attackers compromise your system using crafted image files. The only safe path is to upgrade to v.28.1 or later right away.
For enterprise deployments, audit any software that uses Exiv2—many photo management tools and CMS platforms might be affected.
Timeline
Published on: 11/06/2023 18:15:08 UTC
Last modified on: 11/14/2023 17:10:42 UTC