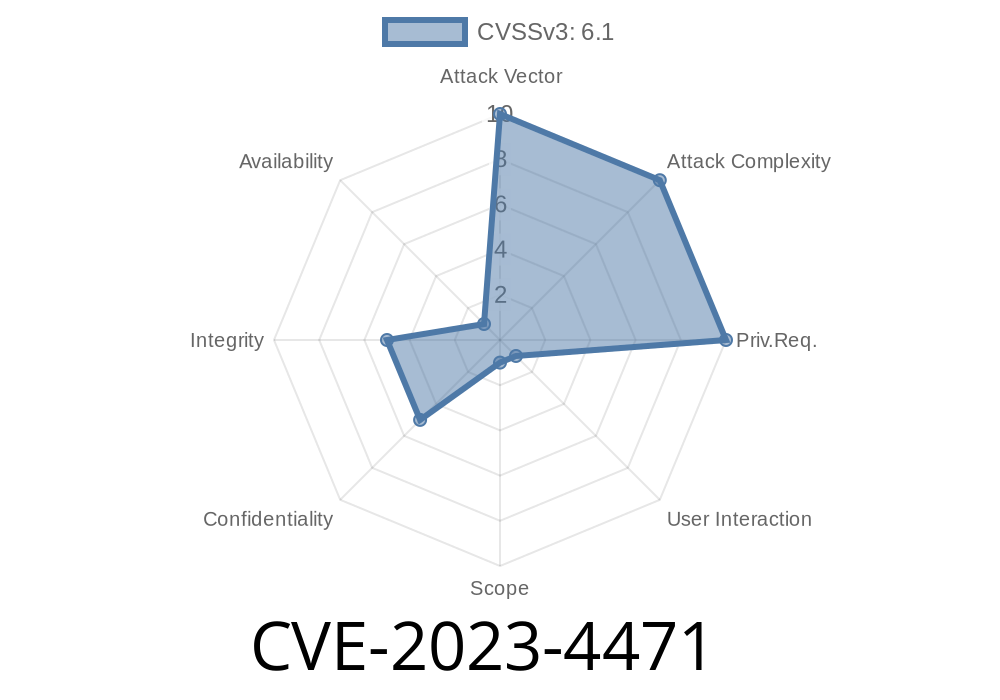
If you’re running a WordPress-powered store and using the Order Tracking Pro plugin (versions up to and including 3.3.6), you may be at risk due to a Reflected Cross-Site Scripting (XSS) vulnerability tracked as CVE-2023-4471. This security flaw could allow hackers to inject malicious scripts into your website—scripts that could run as soon as an unsuspecting victim clicks the wrong link.
In this exclusive post, we’ll show you how this bug works, walk you through a simple code example of the exploit, and link to the original sources. Let's dive in, even if you’re not an infosec expert.
What is CVE-2023-4471?
CVE-2023-4471 is a reflected XSS vulnerability in the Order Tracking Pro WordPress plugin. It lets an attacker insert hostile JavaScript into the browser of users who visit a specially crafted URL, even if those users are not logged into the site.
Affected Plugin: Order Tracking Pro
Affected Versions: Up to and including 3.3.6
Vulnerable Parameters: start_date and end_date
Attack vector: Unauthenticated (no login required!)
Main reason: The plugin fails to sanitize incoming data in the start_date and end_date URL parameters, and it doesn’t escape the output when printing on pages.
How Does the Attack Work?
A hacker crafts a URL to the order tracking page on your site, stuffing malicious JavaScript into the start_date or end_date parameter.
If a user with enough trust (like a shop manager or a customer) is tricked into clicking that link—maybe by email, social media, or a message—the script runs in that user’s browser. This could mean stealing cookies, redirecting to malicious sites, or impersonating the user.
Scenario:
*You receive an email: “Hey, check your latest orders!” With a link. You click. A script runs in your browser, and your login cookie is sent to the attacker.*
Realistic Exploit Example
Here’s a stripped-down proof-of-concept. Suppose the order tracking page is at /track-your-order/.
An attacker can send the following link
https://example.com/track-your-order/?start_date=%22%3E%3Cscript%3Ealert('XSS')%3C/script%3E
Decoded, it looks like
https://example.com/track-your-order/?start_date="><script>alert('XSS')</script>;
When this page is loaded, the script will pop up an alert, proving XSS. In a real attack, the script might be hidden or do something worse.
Why does it work?
Because the plugin takes the raw start_date parameter and echoes it out to the page without removing <, >, and other special characters.
While we don’t have the exact source code, it likely looks something like this in PHP
// Vulnerable: no sanitization
$start_date = $_GET['start_date'];
echo "<input name='start_date' value='$start_date'>";
The right way would be to sanitize or escape
// Safe: Escape before output
$start_date = esc_attr($_GET['start_date']);
echo "<input name='start_date' value='$start_date'>";
What’s happening:
In the first example, if someone sticks "><script>evil()</script> into the parameter, that code is run in the browser. The second example (with esc_attr) safely converts those special characters.
Could steal session tokens, impersonate users, or redirect victims.
> All WordPress shops using Order Tracking Pro up to 3.3.6 are vulnerable unless updated.
How to Protect Yourself
1. Update the Plugin
A patch is usually the best fix. As soon as your plugin author ships a new release, update ASAP.
2. Sanitize User Inputs
If you fork or edit this plugin yourself, always escape and sanitize all values that come from $_GET or $_POST before output.
3. Educate Your Users
Warn users and admins not to click on suspicious links, especially in their email or DMs.
References & Further Reading
- Wordfence Report on CVE-2023-4471
- NVD CVE Record for CVE-2023-4471
- WPScan Entry
- How to Prevent XSS in WordPress (WordPress.org docs)
Final Thoughts
If you run a WooCommerce or other store with the Order Tracking Pro plugin, take this bug seriously. In the wrong hands, a simple overlooked bug could spell disaster for your business and your customers’ privacy.
Always keep your plugins up to date. Remember, in the world of web security, the little details—like escaping a date input—can make the biggest difference.
Stay safe! If you want to test for this bug yourself, use the example link above and watch for popups or suspicious behavior. But never run exploits on production sites without permission!
*Did you find this useful? Share with your fellow WordPress admins. Don’t leave your site open to simple, costly attacks.*
Timeline
Published on: 08/31/2023 06:15:11 UTC
Last modified on: 11/07/2023 04:22:39 UTC