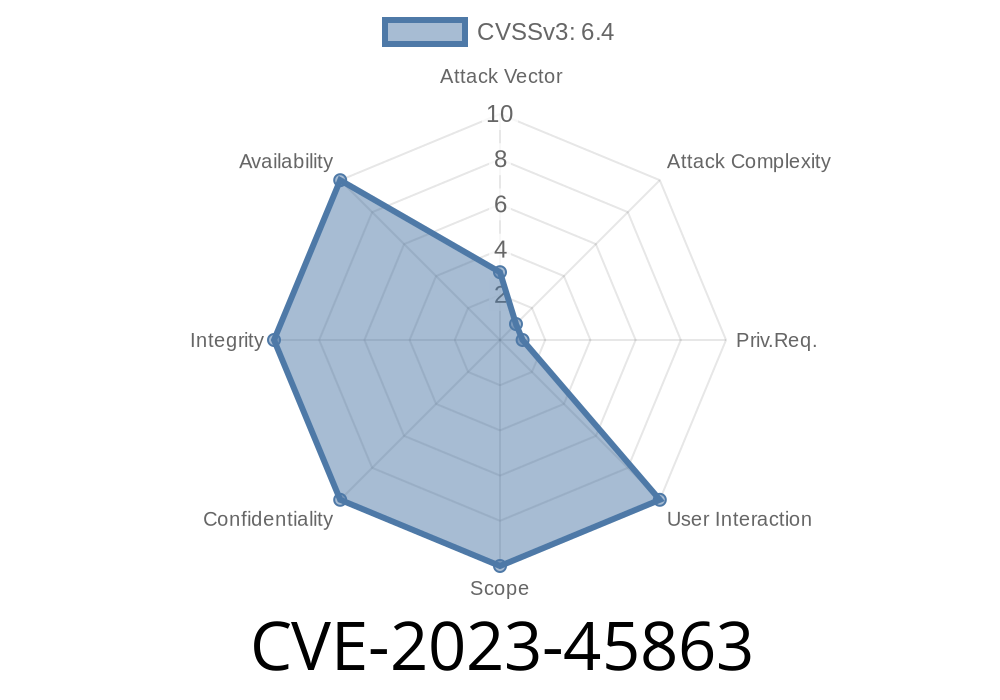
CVE-2023-45863 is a critical vulnerability found in the Linux kernel's lib/kobject.c file, affecting versions before 6.2.3. This issue can lead to an out-of-bounds (OOB) write in the fill_kobj_path function, making Linux systems potentially unstable or vulnerable for privilege escalation. Although root access is needed to exploit this bug, its nature makes it a priority for secure environments and production servers.
In this post, we’ll break down how the vulnerability works, show a code snippet, discuss its impact, share mitigation strategies, and provide direct links to original sources. We aim for clear, simple explanations so anyone with basic Linux knowledge can follow along.
1. What is CVE-2023-45863?
This vulnerability lives in the Linux kernel's object management system (kobject), specifically in the way kobject paths are constructed. If two threads try to interact with the same kernel object at the same time, a race condition can occur. By manipulating the timing, an attacker with root access can force the fill_kobj_path() function to write data outside the boundaries of its allocated buffer—leading to memory corruption.
The problem sits at how fill_kobj_path() fills buffer space
// Vulnerable function: lib/kobject.c (before version 6.2.3)
static int fill_kobj_path(struct kobject *kobj, char *path, int buflen) {
int len = buf_len; // total buffer length
// walk up the kobj tree
while (kobj) {
int cur_len = strlen(kobj->name);
len -= cur_len;
// If not enough space, break (but this logic is flawed)
if (len < )
break;
memcpy(path + len, kobj->name, cur_len);
path[--len] = '/'; // <-- here is the time window for race
kobj = kobj->parent; // Might change due to concurrency
}
// OOB write can happen here if kobj tree changes mid-way
return len;
}
What goes wrong?
If one thread is writing the kobject path and another modifies the kobject hierarchy (like changing a parent), lengths and names can mismatch. This desynchronization lets the function write past the end of the path buffer—a classic out-of-bounds situation.
3. How Could Attackers Exploit It?
While you need root to trigger this (which already limits attackers), local privilege escalation or system crashes are possible. A malicious root process can:
Trigger out-of-bounds writes, corrupting kernel memory
It can result in kernel panics, instability, or more subtle memory manipulations (a stepping stone for chaining other attacks).
Proof-of-Concept (PoC) snippet:
*Note: For learning and research only!*
// A pseudo-code illustration, not safe for real systems!
void *racer(void *arg) {
struct kobject *kobj = (struct kobject *)arg;
while (1) {
set_new_parent(kobj, random_kobj());
}
}
int main() {
// Init kobj and parent
pthread_t t;
struct kobject *mykobj = init_kobj();
// Launch thread to mess with parent
pthread_create(&t, NULL, racer, (void*)mykobj);
char buf[256];
// Rapid calls to vulnerable function
for (int i = ; i < 100000; i++)
fill_kobj_path(mykobj, buf, sizeof(buf));
}
5. Fixes and Mitigation
Mainline Fix:
The bug was patched in Linux 6.2.3 by adding proper locking and validation to prevent concurrent modifications during fill_kobj_path. All major linux distributions have backported the patch to older LTS kernels.
Update Solution:
Update your kernel to at least 6.2.3, or ensure your distribution has applied the fix. If upgrading is not possible:
Monitor for abnormal kernel object activity
Patch Reference:
Upstream patch commit
6. References and Further Reading
- NVD Listing for CVE-2023-45863
- Kernel.org Patch and Discussion
- Original Source Code
- CVE Details Tracker
- Red Hat Security Advisory
7. Conclusion
CVE-2023-45863 is yet another reminder that kernel code must be thread-safe, especially where object hierarchies can morph at runtime. This vulnerability lets race conditions turn into real threats—even with higher privilege levels. Patch quickly, minimize root usage, and always stay tuned to kernel security updates.
*This post was written for education and awareness. Always use responsibly and never attack systems you do not own or have explicit permission to test.*
Timeline
Published on: 10/14/2023 21:15:45 UTC
Last modified on: 10/19/2023 13:12:23 UTC