---
WordPress is the world’s most popular website platform, so security holes in its plugins could impact lots of websites. On November 24, 2023, a reflected cross-site scripting (XSS) vulnerability was published in the FreshMail For WordPress plugin, maintained by Borbis Media. This flaw affects all versions up to and including 2.3.2.
If you use this plugin, read on to learn how the bug works, see exploit examples, and find helpful links to protect your site.
What is CVE-2023-46074?
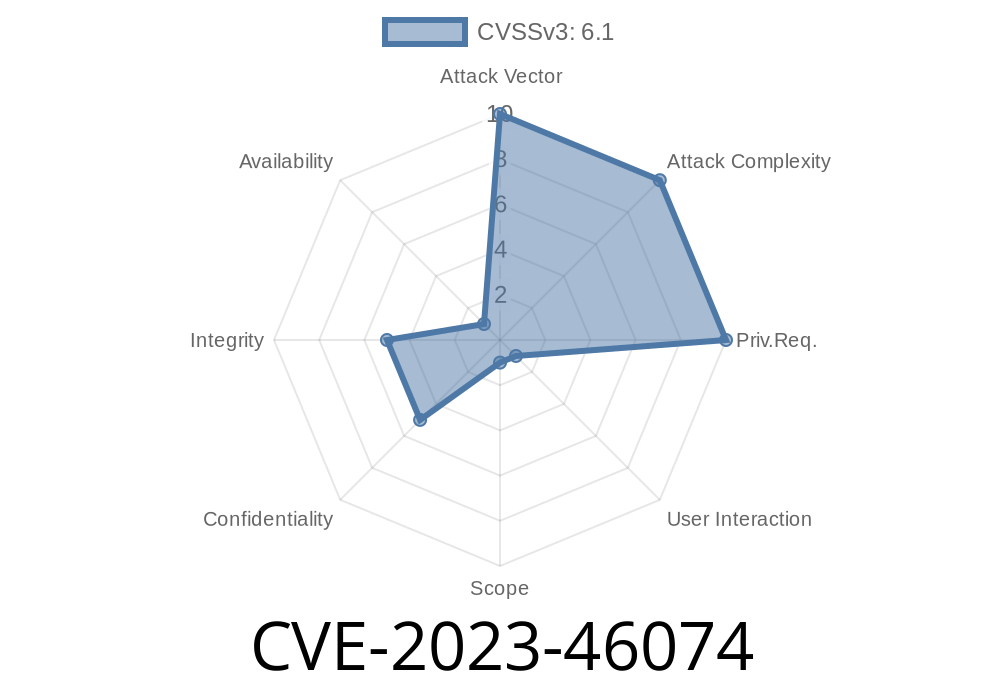
CVE-2023-46074 describes a security weakness called a reflected cross-site scripting (XSS) vulnerability. Attackers can make a victim’s browser run malicious JavaScript just by clicking a crafted link — without authentication.
- Plugin: FreshMail For WordPress
Vulnerability type: Unauthenticated Reflected Cross-Site Scripting (XSS)
- CVE page: NVD - CVE-2023-46074
Attack Impact:
An attacker could trick any logged-in admin (or even a regular site visitor) into opening a malicious link to your site — stealing their session, performing actions as them, or redirecting them to other malicious sites.
How the Vulnerability Works
The bug lives in FreshMail’s implementation that fails to sanitize user input in certain URLs. When it loads information on a backend page, it reflects user-supplied parameters directly into the page’s output — without escaping or filtering dangerous JavaScript.
Here’s a simplified example (not full plugin code, but the essential vulnerable part)
<?php
// Vulnerable segment (simplified)
if (isset($_GET['fm_message'])) {
// No escaping or validation!
echo "<div class='fm-message'>{$_GET['fm_message']}</div>";
}
?>
Suppose an attacker creates this link
https://yoursite.com/wp-admin/admin.php?page=freshmail&fm_message=<script>alert('XSS!')</script>;
Any user who clicks this link will see an “alert” popup — but real attackers can inject far more dangerous JavaScript, e.g., stealing cookies or changing admin settings behind your back.
Let’s walk through a simple proof-of-concept.
Step 1:
Construct a link as follows (adjust yoursite.com to your real domain)
https://yoursite.com/wp-admin/admin.php?page=freshmail&fm_message=%3Cscript%3Ealert(document.domain)%3C/script%3E
The value is URL-encoded:
- <script>alert(document.domain)</script> becomes %3Cscript%3Ealert(document.domain)%3C/script%3E
Step 2:
Send this link to an admin or visitor, or embed it into a phishing email. Anyone following that link will execute the attacker’s script in the context of your site!
Video Demo (Unofficial)
You can see a similar XSS in action in this generic demo:
How Reflected XSS Works - YouTube
Wordfence Vulnerability Report:
Unauth. Reflected XSS in FreshMail For WordPress
Patchstack Database Entry:
FreshMail For WordPress XSS Up To 2.3.2
NVD (National Vulnerability Database):
Upgrade Immediately:
If you use FreshMail for WordPress, update to the latest version now. If no fix is available, strongly consider disabling the plugin until it’s patched.
WAF (Web Application Firewall):
Use a modern firewall like Wordfence to block XSS attempts site-wide.
Alert Your Team:
Tell site admins and editors to avoid clicking suspicious links, especially those to /wp-admin/ with odd parameters.
Visit Plugins → Updates in WP Admin, update FreshMail For WordPress.
3. If no secure update is available, disable/delete the plugin.
Review user accounts for signs of compromise.
5. Scan your site using Wordfence or Sucuri SiteCheck.
Conclusion
Reflected XSS vulnerabilities are an ever-present threat on WordPress, especially in plugins that handle input data. CVE-2023-46074 is easy to exploit because no login is needed and the payload can be anything a browser will run. This makes a dangerous situation for site owners and visitors alike.
Patch now. Stay aware of plugin security bulletins. Protect your site and keep your users safe!
> *If this post helped you understand CVE-2023-46074 and how to defend against reflected XSS, share it with your fellow WordPress site owners!*
Timeline
Published on: 10/26/2023 12:15:08 UTC
Last modified on: 10/30/2023 16:21:25 UTC