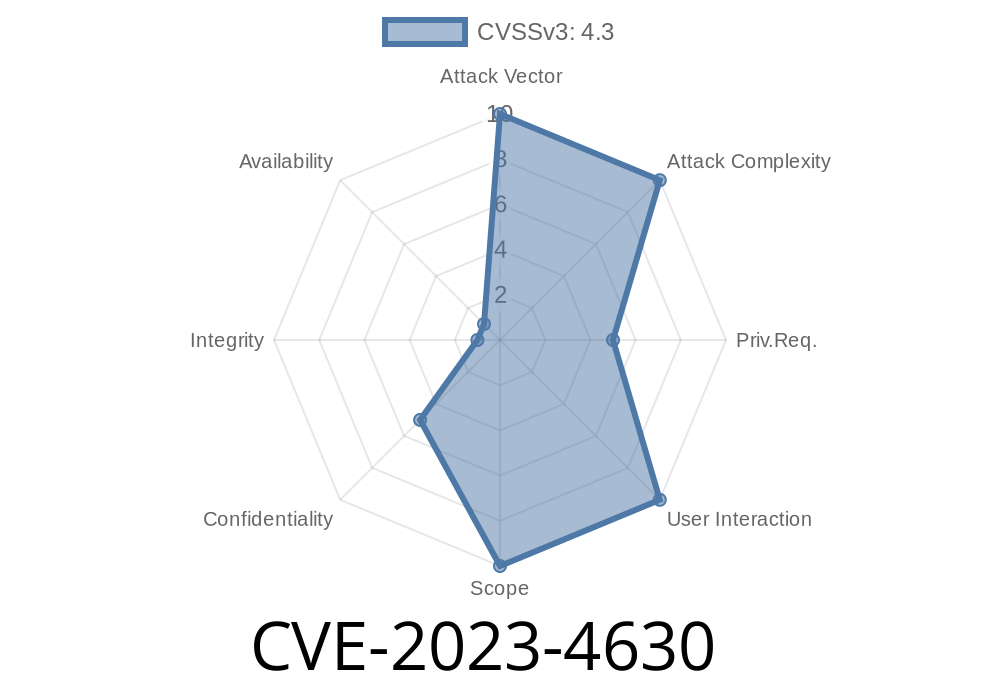
A recent vulnerability, CVE-2023-4630, has been identified and is currently affecting different versions of GitLab, a widely-used web-based software for managing Git repositories. The vulnerability allows any user to view limited information about any project's imports, even if they are not authorized to do so.
If you use GitLab platforms in your organization, it is crucial to address this vulnerability immediately to prevent potential risks to your sensitive data.
Description
Due to a weak permission check in the GitLab platform, unauthorized users are capable of viewing limited information about any project's imports. This can be exploited by malicious actors to gain unauthorized access to sensitive data or obtain information that could help them carry out further attacks on the affected systems.
The original references for this vulnerability include
- GitLab's official security advisory: https://about.gitlab.com/releases/2023/03/05/security-release-16-2-5-and-eslint-security-announcement/
- National Vulnerability Database (NVD) entry: https://nvd.nist.gov/vuln/detail/CVE-2023-4630
Code Snippet
Below is a code snippet illustrating the weak permission check in GitLab.
class Project::ImportController < Projects:ApplicationController
def show
respond_to do |format|
format.json do
# Affected line: Missing proper permission check
import = project_import.find_by(project_id: params[:id])
render json: { import_status: import.try(:status_raw), import_error: import.try(:last_error) }
end
end
end
end
Exploit Details
The vulnerability exists in the show method of the Project::ImportController. The method lacks a proper permission check, which allows unauthorized users to view limited information about any project's imports simply by changing the project_id parameter in the affected API endpoint.
To exploit this vulnerability, a malicious actor could send a crafted HTTP request to the GitLab instance and receive limited information about any given project's imports.
Recommendations
If your organization uses the affected versions of GitLab, it is highly recommended to apply the necessary updates as soon as possible:
Upgrade GitLab to version 16.3.1 or newer if you are running any version between 16.3 to 16.3..
In addition to applying the updates, it is essential to continuously monitor any suspicious activity in your GitLab environment and report them to the appropriate security team.
Conclusion
This vulnerability (CVE-2023-4630) is a critical issue in GitLab that needs to be addressed promptly. By upgrading your organization's GitLab instance to the latest secure version, you can help protect your environment from potential threats and ensure the safety of your sensitive data.
Timeline
Published on: 09/11/2023 14:15:00 UTC
Last modified on: 09/13/2023 16:50:00 UTC