---
Introduction
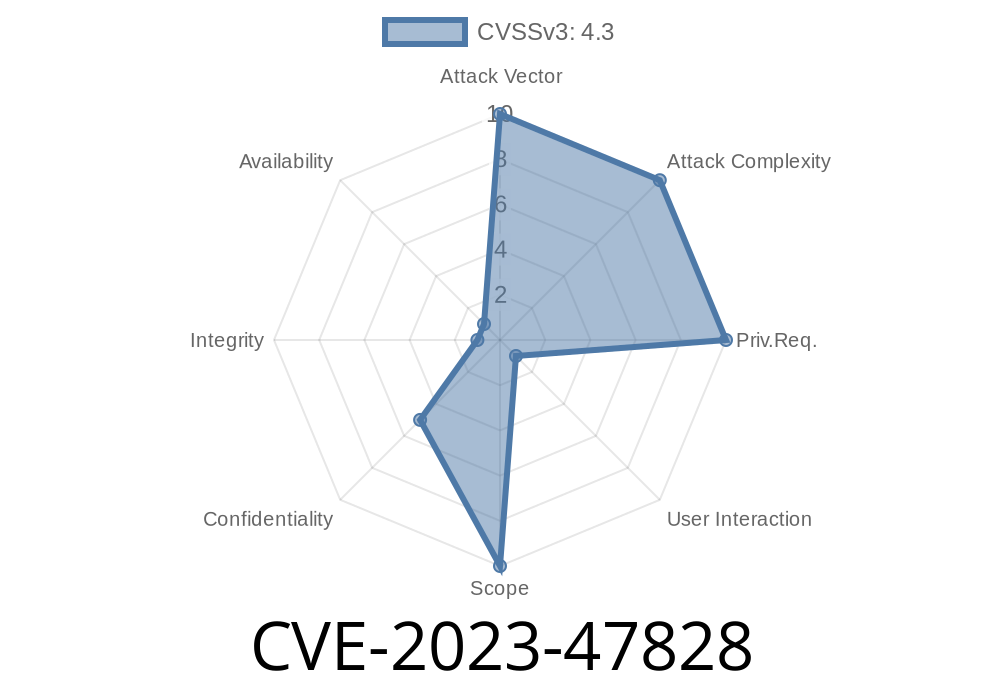
A critical security vulnerability, identified as CVE-2023-47828, has been discovered in the WordPress plugin wpMandrill—a popular integration for sending emails through the Mandrill API. The issue, classified as a *Missing Authorization* vulnerability, affects all versions of wpMandrill up to and including version 1.33.
In this blog post, we’ll explain what CVE-2023-47828 is, how attackers can exploit it, see code snippets illustrating the issue, and what you can do to protect your website.
What is wpMandrill?
wpMandrill is a plugin that allows WordPress sites to integrate with Mandrill, an email delivery service by Mailchimp. With it, all outgoing emails from WordPress are sent through Mandrill’s servers, helping improve deliverability and analytics.
What is CVE-2023-47828?
CVE-2023-47828 is a *Missing Authorization* vulnerability. This means a function or endpoint in the plugin does not properly check user permissions. As a result, attackers may access or manipulate plugin features—potentially exposing sensitive data or causing unwanted site actions.
Affected versions: All versions up to 1.33 (the latest at time of writing)
Vulnerability Type: Missing Authorization / Improper Access Controls
How Does the Vulnerability Work?
*Attackers can call certain AJAX actions or endpoints in wpMandrill without being authenticated or authorized.* If these endpoints perform sensitive actions, this could lead to data leaks or compromise of email-sending functionality.
Here’s a simplified code snippet inspired by wpMandrill’s vulnerabilities
// File: wpmandrill.php
add_action( 'wp_ajax_wpmandrill_get_stats', 'wpmandrill_get_stats' );
add_action( 'wp_ajax_nopriv_wpmandrill_get_stats', 'wpmandrill_get_stats' );
function wpmandrill_get_stats() {
// MISSING CHECK: No current_user_can() or nonce verification
$stats = wpmandrill_stats_api_call();
echo json_encode($stats);
wp_die();
}
The Issue:
- Both authenticated users and unauthenticated visitors (nopriv) can access the 'wpmandrill_get_stats' AJAX action.
- The function does not verify the user’s role or permissions nor does it check for a valid nonce.
Consequence:
- Anyone on the internet could call this function and fetch Mandrill usage stats (or in similar cases, modify settings or send emails).
1. Discover the AJAX Action
AJAX actions in WordPress can be called by sending a POST request to /wp-admin/admin-ajax.php with the action parameter.
Anyone—without authentication—can trigger the AJAX action. Here’s a sample cURL command
curl -X POST https://victim-site.com/wp-admin/admin-ajax.php \
-d 'action=wpmandrill_get_stats'
3. Get the Response
If the site is vulnerable, it will respond with statistics data or other sensitive info meant only for admins.
Potential Impact
- Information Disclosure: Attackers can view email usage stats, recipients, or other internal data.
- Privilege Escalation: If other AJAX functions are exposed, attackers might send emails or modify plugin settings.
- Spam and Phishing: Attackers could (depending on other code flaws) use your Mandrill setup to send unauthorized emails, impacting your reputation and domain health.
Timeline and References
- Vulnerability discovery: Huntr.dev Advisory
- CVE record: NVD CVE-2023-47828
- Patch status: No fix released as of June 2024. The plugin has not been updated since version 1.33.
1. Disable wpMandrill
If you are using any version up to 1.33, deactivate the plugin until a patch is released.
2. Monitor for Security Updates
Watch the WordPress plugin page and security feeds for updates.
3. Restrict admin-ajax.php
Consider restricting access to admin-ajax.php (with .htaccess or firewall rules) to trusted users only where possible.
4. Replace wpMandrill
Switch to maintained solutions with proper access controls, such as WP Mail SMTP with Mandrill integration.
Add capability checks and nonce verification
add_action( 'wp_ajax_wpmandrill_get_stats', 'wpmandrill_get_stats' );
function wpmandrill_get_stats() {
if ( !current_user_can('manage_options') || !check_ajax_referer('wpmandrill_stats_nonce', 'nonce', false) ) {
wp_send_json_error("Unauthorized");
wp_die();
}
$stats = wpmandrill_stats_api_call();
wp_send_json_success($stats);
wp_die();
}
Summary
- CVE-2023-47828 is a serious vulnerability in wpMandrill, allowing unauthorized users to access plugin endpoints.
All versions up to 1.33 are affected, with no fix available yet.
- Immediate action: disable the plugin, restrict AJAX endpoints, and await a patch or move to a secure alternative.
Original References
- huntr.com Advisory
- NVD CVE Record
- wpMandrill Plugin
*Have questions? Leave a comment below or reach out to your webmaster/security team for support!*
Timeline
Published on: 06/12/2024 10:15:27 UTC
Last modified on: 06/13/2024 18:36:09 UTC